Exactly one week ago, Emotet, one of the most dangerous threats to organizations in the last year, resumed its malicious spam campaigns after several months of inactivity. Based on our telemetry, we can see that the botnet started becoming chatty with its command and control servers (C2), about a week or so before the spam came through.
As each new week rolls in, the threat actors behind Emotet are always punctual with delivering their spam messages, thanks to their large botnet. And once they’ve spammed and infiltrated an endpoint, their work is far from over. As we’ve said before, Emotet is a double or even triple threat if it is not quarantined right away.Follow up payloads, such as TrickBot and Ryuk ransomware are those that can truly cripple any business that is not prepared.
Malwarebytes business users and Premium home users are already protected against this threat.
Users who are not Malwarebytes customers or who use the free scanner will want to take additional steps to protect against Emotet or clean up the infection, if they’ve already been hit. Businesses and organizations that may currently be battling an Emotet infection can view our Emotet emergency kit, which includes a contact number for those in need of immediate assistance, as well as background information on how Emotet works and a list of protection and remediation tips.
Indicators of Compromise (IOCs)
Malicious Word document
5ab7a5cf290ebf52647771f893a2fa322a9b1891e5a5e54811c500dd290c8477
Emotet payload
757b35d20f05b98f2c51fc7a9b6a57ccbbd428576563d3aff7e0c6b70d544975
Network traffic
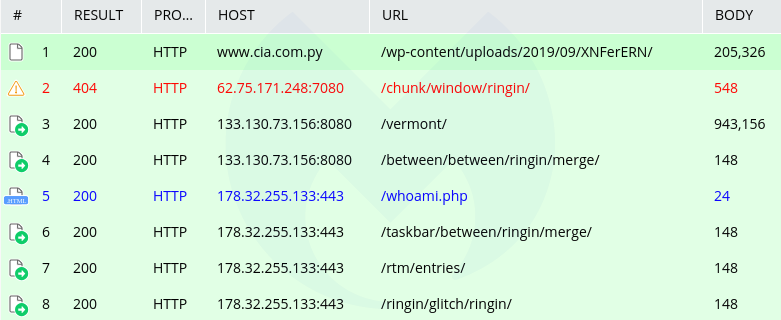
Emotet: www.cia.com[.]py/wp-content/uploads/2019/09/XNFerERN/ Emotet C2: 62.75.171.248:7080/chunk/window/ringin/ Emotet C2: 133.130.73[.]156 Emotet C2: 178.32.255[.]133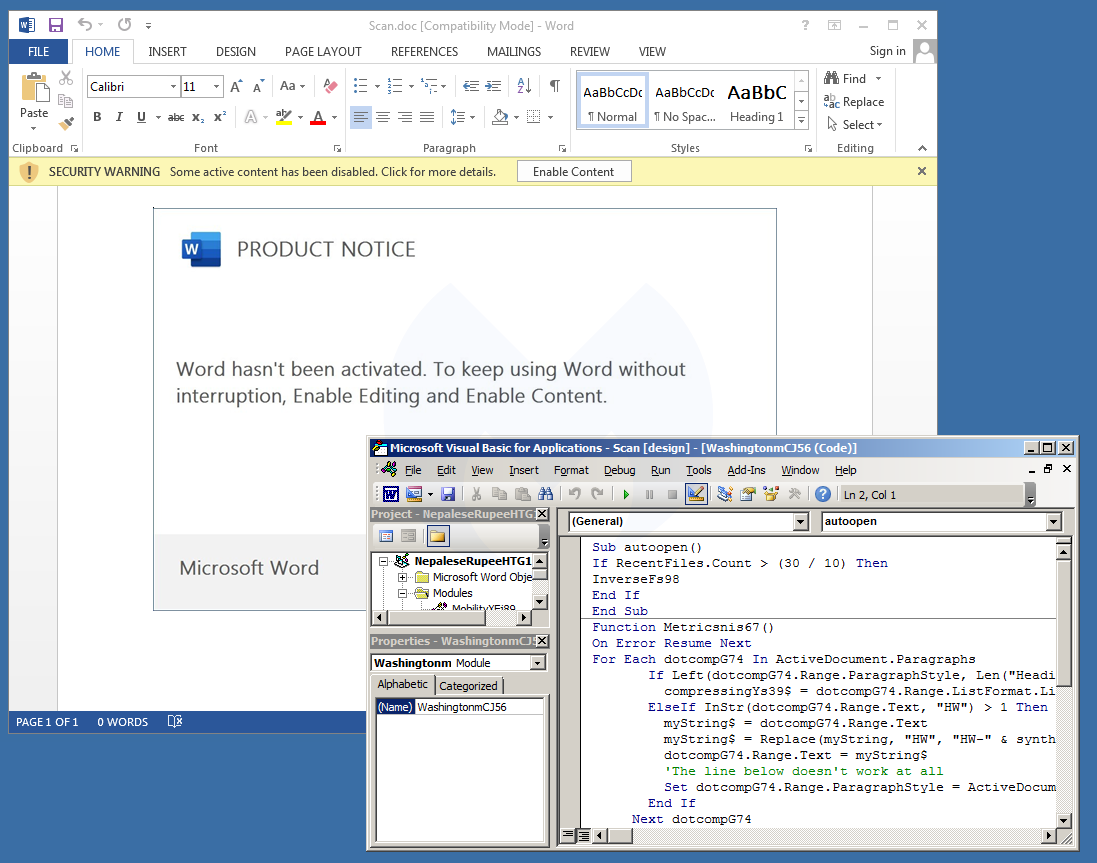
The macro triggers a PowerShell command that will retrieve the Emotet malware binary from a compromised WordPress site. After infection, the machine will attempt to reach out to one of Emotet’s many C2s:

As each new week rolls in, the threat actors behind Emotet are always punctual with delivering their spam messages, thanks to their large botnet. And once they’ve spammed and infiltrated an endpoint, their work is far from over. As we’ve said before, Emotet is a double or even triple threat if it is not quarantined right away.Follow up payloads, such as TrickBot and Ryuk ransomware are those that can truly cripple any business that is not prepared.
Malwarebytes business users and Premium home users are already protected against this threat.
Users who are not Malwarebytes customers or who use the free scanner will want to take additional steps to protect against Emotet or clean up the infection, if they’ve already been hit. Businesses and organizations that may currently be battling an Emotet infection can view our Emotet emergency kit, which includes a contact number for those in need of immediate assistance, as well as background information on how Emotet works and a list of protection and remediation tips.
Indicators of Compromise (IOCs)
Malicious Word document
5ab7a5cf290ebf52647771f893a2fa322a9b1891e5a5e54811c500dd290c8477
Emotet payload
757b35d20f05b98f2c51fc7a9b6a57ccbbd428576563d3aff7e0c6b70d544975
Network traffic
Emotet: www.cia.com[.]py/wp-content/uploads/2019/09/XNFerERN/ Emotet C2: 62.75.171.248:7080/chunk/window/ringin/ Emotet C2: 133.130.73[.]156 Emotet C2: 178.32.255[.]133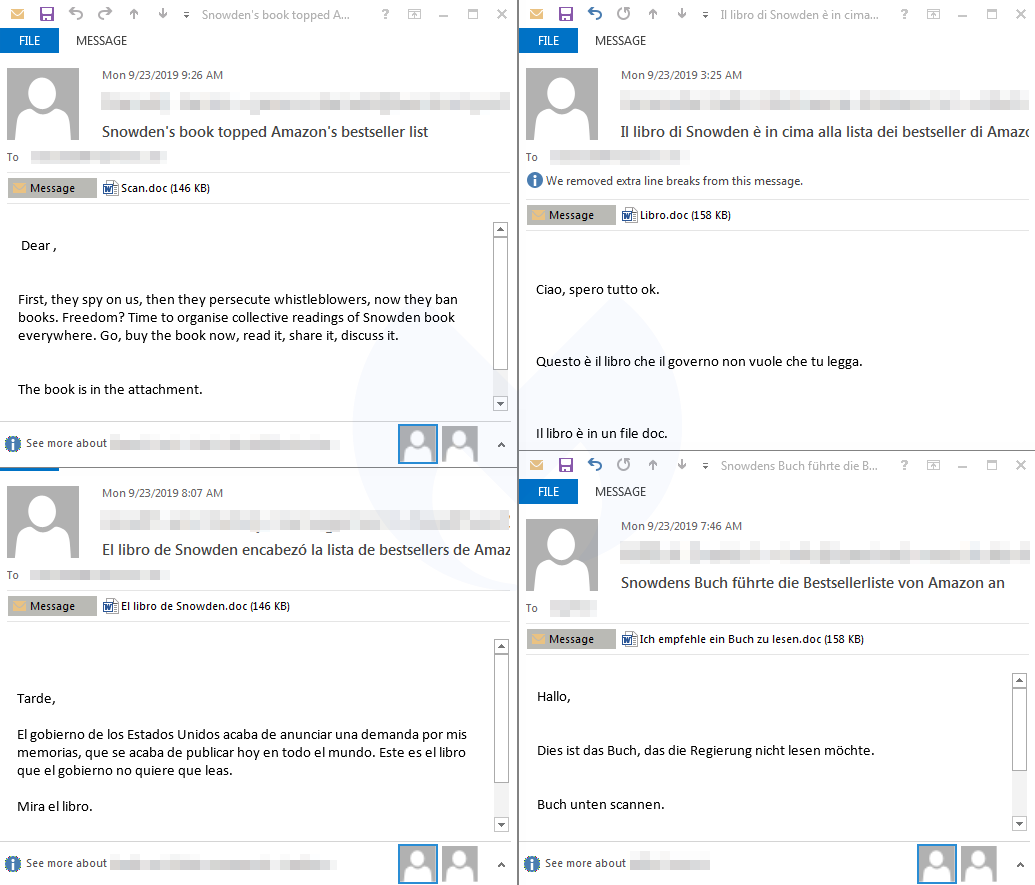
Upon opening the document, a fake message that “Word hasn’t been activated” is displayed to victims who are prompted to enable the content with a yellow security warning. Once they do, nothing appears to happen. However, what users don’t see is the malicious macro code that will execute once they click on the button.

The macro triggers a PowerShell command that will retrieve the Emotet malware binary from a compromised WordPress site. After infection, the machine will attempt to reach out to one of Emotet’s many C2s:

As each new week rolls in, the threat actors behind Emotet are always punctual with delivering their spam messages, thanks to their large botnet. And once they’ve spammed and infiltrated an endpoint, their work is far from over. As we’ve said before, Emotet is a double or even triple threat if it is not quarantined right away.Follow up payloads, such as TrickBot and Ryuk ransomware are those that can truly cripple any business that is not prepared.
Malwarebytes business users and Premium home users are already protected against this threat.
Users who are not Malwarebytes customers or who use the free scanner will want to take additional steps to protect against Emotet or clean up the infection, if they’ve already been hit. Businesses and organizations that may currently be battling an Emotet infection can view our Emotet emergency kit, which includes a contact number for those in need of immediate assistance, as well as background information on how Emotet works and a list of protection and remediation tips.
Indicators of Compromise (IOCs)
Malicious Word document
5ab7a5cf290ebf52647771f893a2fa322a9b1891e5a5e54811c500dd290c8477
Emotet payload
757b35d20f05b98f2c51fc7a9b6a57ccbbd428576563d3aff7e0c6b70d544975
Network traffic
Emotet: www.cia.com[.]py/wp-content/uploads/2019/09/XNFerERN/ Emotet C2: 62.75.171.248:7080/chunk/window/ringin/ Emotet C2: 133.130.73[.]156 Emotet C2: 178.32.255[.]133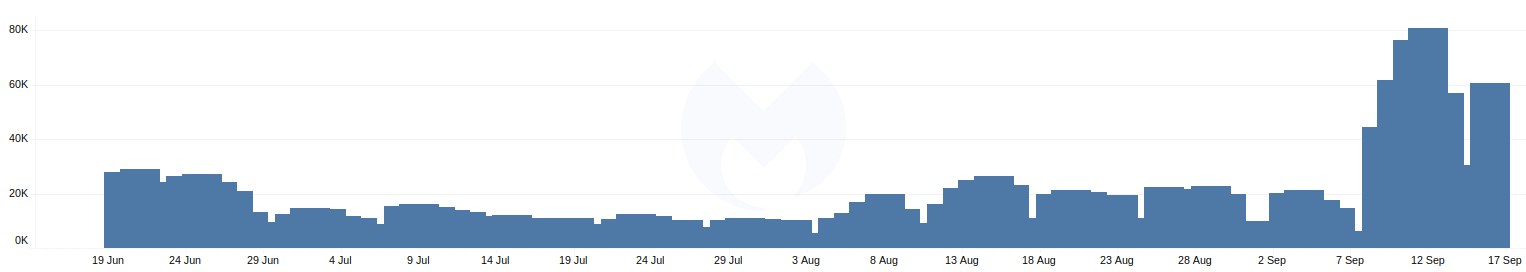
To kick off its spam campaign last week, Emotet resumed spear phishing tactics it adopted in late spring 2019, hijacking old email threads with personalized subject lines and appearing as old invoices.
This week, Emotet is trying a different tactic, incorporating the news about NSA whistleblower Edward Snowden’s new book Permanent Record as a lure. The memoir, which is already on Amazon’s bestseller list, has been the subject of intense debates. In addition, the US government is also suing Snowden for violating non-disclosure agreements and publishing without prior approval.
Criminals are known to capitalize on newsworthy events for scams and other social engineering purposes. In this particular case, Emotet authors are supposedly offering Snowden’s memoir as a Word attachment. We collected emails from our spam honeypot in English, Italian, Spanish, German and French claiming to contain a copy of Snowden’s book in Word form.

Upon opening the document, a fake message that “Word hasn’t been activated” is displayed to victims who are prompted to enable the content with a yellow security warning. Once they do, nothing appears to happen. However, what users don’t see is the malicious macro code that will execute once they click on the button.

The macro triggers a PowerShell command that will retrieve the Emotet malware binary from a compromised WordPress site. After infection, the machine will attempt to reach out to one of Emotet’s many C2s:

As each new week rolls in, the threat actors behind Emotet are always punctual with delivering their spam messages, thanks to their large botnet. And once they’ve spammed and infiltrated an endpoint, their work is far from over. As we’ve said before, Emotet is a double or even triple threat if it is not quarantined right away.Follow up payloads, such as TrickBot and Ryuk ransomware are those that can truly cripple any business that is not prepared.
Malwarebytes business users and Premium home users are already protected against this threat.
Users who are not Malwarebytes customers or who use the free scanner will want to take additional steps to protect against Emotet or clean up the infection, if they’ve already been hit. Businesses and organizations that may currently be battling an Emotet infection can view our Emotet emergency kit, which includes a contact number for those in need of immediate assistance, as well as background information on how Emotet works and a list of protection and remediation tips.
Indicators of Compromise (IOCs)
Malicious Word document
5ab7a5cf290ebf52647771f893a2fa322a9b1891e5a5e54811c500dd290c8477
Emotet payload
757b35d20f05b98f2c51fc7a9b6a57ccbbd428576563d3aff7e0c6b70d544975
Network traffic
Emotet: www.cia.com[.]py/wp-content/uploads/2019/09/XNFerERN/ Emotet C2: 62.75.171.248:7080/chunk/window/ringin/ Emotet C2: 133.130.73[.]156 Emotet C2: 178.32.255[.]133









