If you’re one of the thousands of businesses using Malwarebytes Nebula today, there’s a few best practices you should know for maximum functionality. From toggling on extra layers of protection to configuring regular updates, this post covers ten recommended settings for your Nebula console.
First, a bit of context. Our Nebula solutions build on each other, so as you move forward with our Endpoint Protection or Endpoint Detection and Response recommendations below, make sure you follow our suggestions for Incident Response as well.
For a quick overview of the three types of Nebula subscriptions:
-
-
Provides scheduled scanning of your endpoints based on your specifications, and on-demand scanning of areas where most malware hides. If a threat is detected, it is quarantined for later remediation.
-
-
-
Provides all functionality that IR offers, including our multi-layered real-time protection modules (anti-malware, anti-exploits, behavioral protection, and malicious web control).
-
-
Endpoint Detection and Response (EDR)
-
Provides all functionality that IR and EP offers, including Suspicious Activity Monitoring and Flight Recorder search.
-
In this post, each best practice is tied to one of these three specific solutions, followed by either (IR), (EP), or (EDR). Without further ado, let’s jump into our ten Malwarebytes Nebula best practices.
- Create Daily Software Inventory Scans, Daily Threat Scans and Weekly Custom Scans (IR)
- Exclude your software applications from being flagged or monitored (IR)
- Turn off Scan for rootkits (IR)
- Turn on Tamper protection (IR)
- For servers, change a few endpoint agent settings (EP)
- Keep protection settings enabled (EP)
- Enable Brute Force Protection (EP)
- Toggle on Flight Recorder to enable endpoint data storage for threat investigation (EDR)
- Enable Advanced settings for Suspicious Activity Monitoring
- Enable Ransomware Rollback (EDR)
1. Create Daily Software Inventory Scans, Daily Threat Scans and Weekly Custom Scans (IR)
We recommend creating Daily Software Inventory Scans in order to maintain up-to-date information about your endpoints, as well as Daily Threat Scans to regularly detect any malicious files on your endpoints.
Weekly Custom Scans are also recommended to enable you to scan for precisely what you want, with options to quarantine found threats automatically and more.
For more information on how to set up Daily Software Inventory Scans, Daily Threat Scans and Weekly Custom Scans, please refer to the Set scheduled scans in Malwarebytes Nebula page.
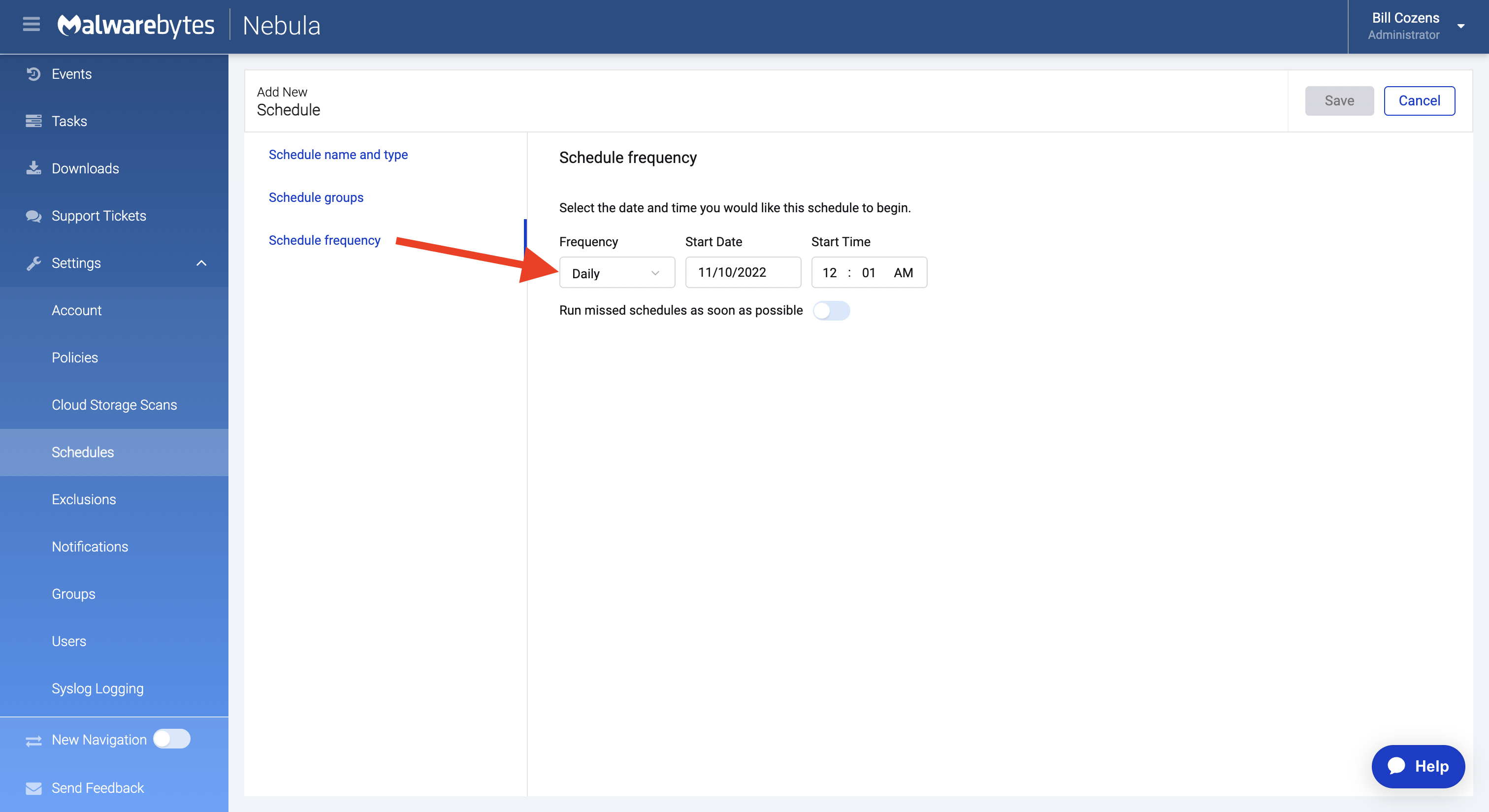
What setting up a Daily Scan looks like.
2. Exclude your software applications from being flagged or monitored (IR)
By excluding specific programs, web addresses, or file locations from being flagged or monitored, you can improve Malwarebytes performance in your environment. Be sure to exclude trusted applications or data files to avoid them being flagged as a false positive.
We also recommend toggling on Exclude GPO PUMs, which prevents Malwarebytes from flagging intentional Group Policy registry modifications. For more information on GPO PUMs, see Group Policy registry keys detected as PUMs in Endpoint Protection.
3. Turn off Scan for rootkits for Threat Scans (IR)
Policies define how Malwarebytes behaves when running a scheduled scan. When configuring scan settings options for policies, we recommend keeping everything enabled except for Scan for rootkits, as enabling this will prolong scans and is not necessary for identifying threats.
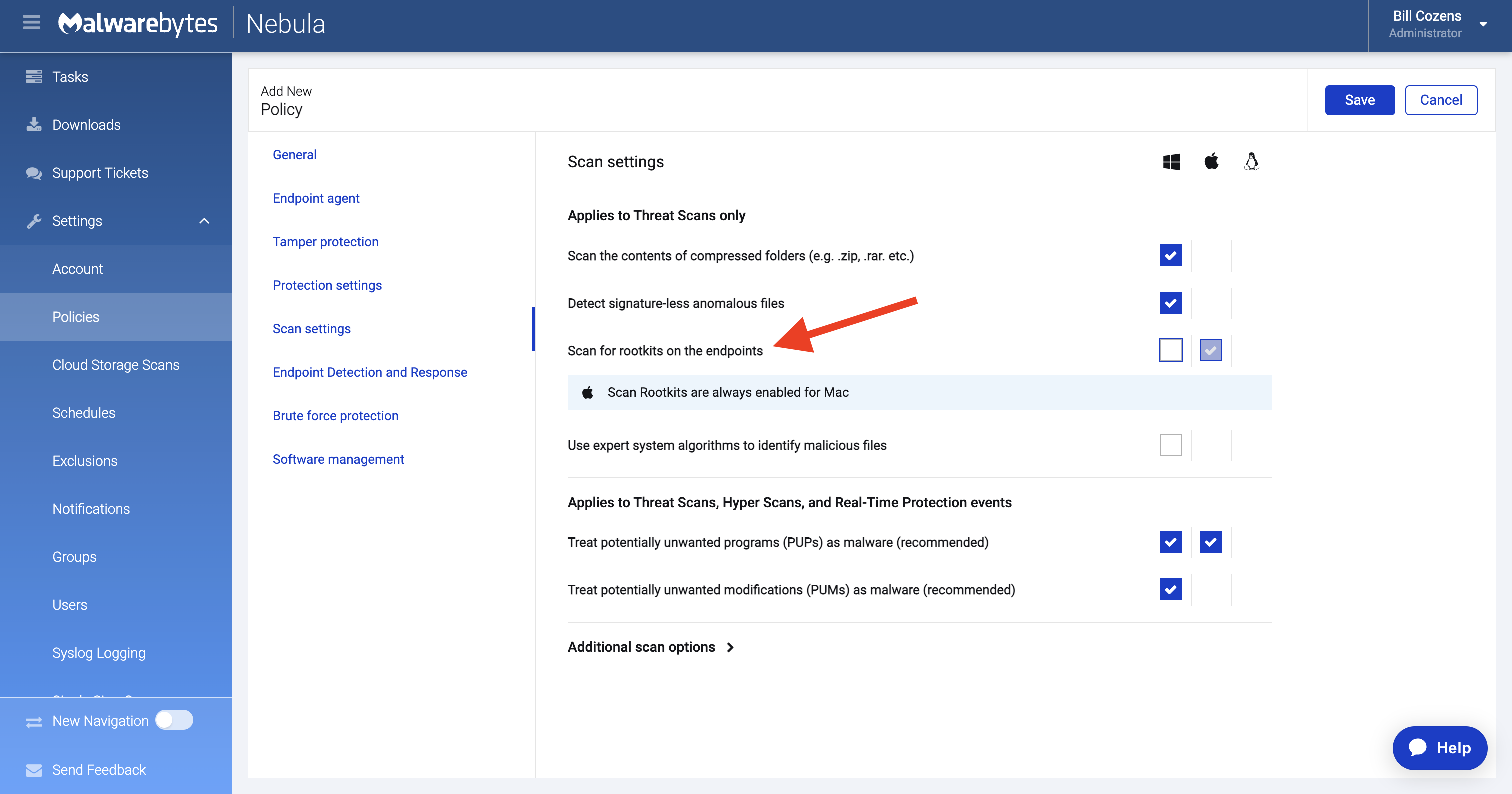
We recommend keeping everything enabled here except for Scan for rootkits.
4. Turn on Tamper protection (IR)
We recommend toggling on Tamper Protection, which adds an additional layer of protection by limiting the ability for an end user to uninstall Malwarebytes.
To find and toggle Tamper Protection, click Settings > Policies > select a policy > select the Tamper protection tab. See Configure Tamper protection options in Malwarebytes Nebula for more details.
5. For servers, change a few Endpoint Agent settings (EP)
Endpoint Agent settings control how the Malwarebytes Endpoint Agent software interfaces with the endpoint. For servers, we recommend changing a few Endpoint Agent settings.
-
User interface options: Controls the Endpoint Agent interface settings on an endpoint.
-
Allow only Administrator level users to interact with the Malwarebytes Tray: Prevents the tray icon from loading on standard level user accounts. This is helpful for multi-user environments such as Microsoft Terminal Services.
-
-
Endpoint agent updates
-
Automatically download and install Malwarebytes application updates: Disable this to prevent servers from automatically updating. Manually update servers during your scheduled maintenance window.
-
-
Reboot settings: Disable this to prevent servers from automatically rebooting after installing an update or quarantining a threat.
6. Keep protection settings enabled (EP)
When configuring protection settings, we recommend enabling all Real-time protection features, which includes web protection, exploit protection, and more. We also recommend enabling Additional Protection, which includes other protection methods that focus on other threat vectors.
For more information, see Configure Protection settings in Nebula.
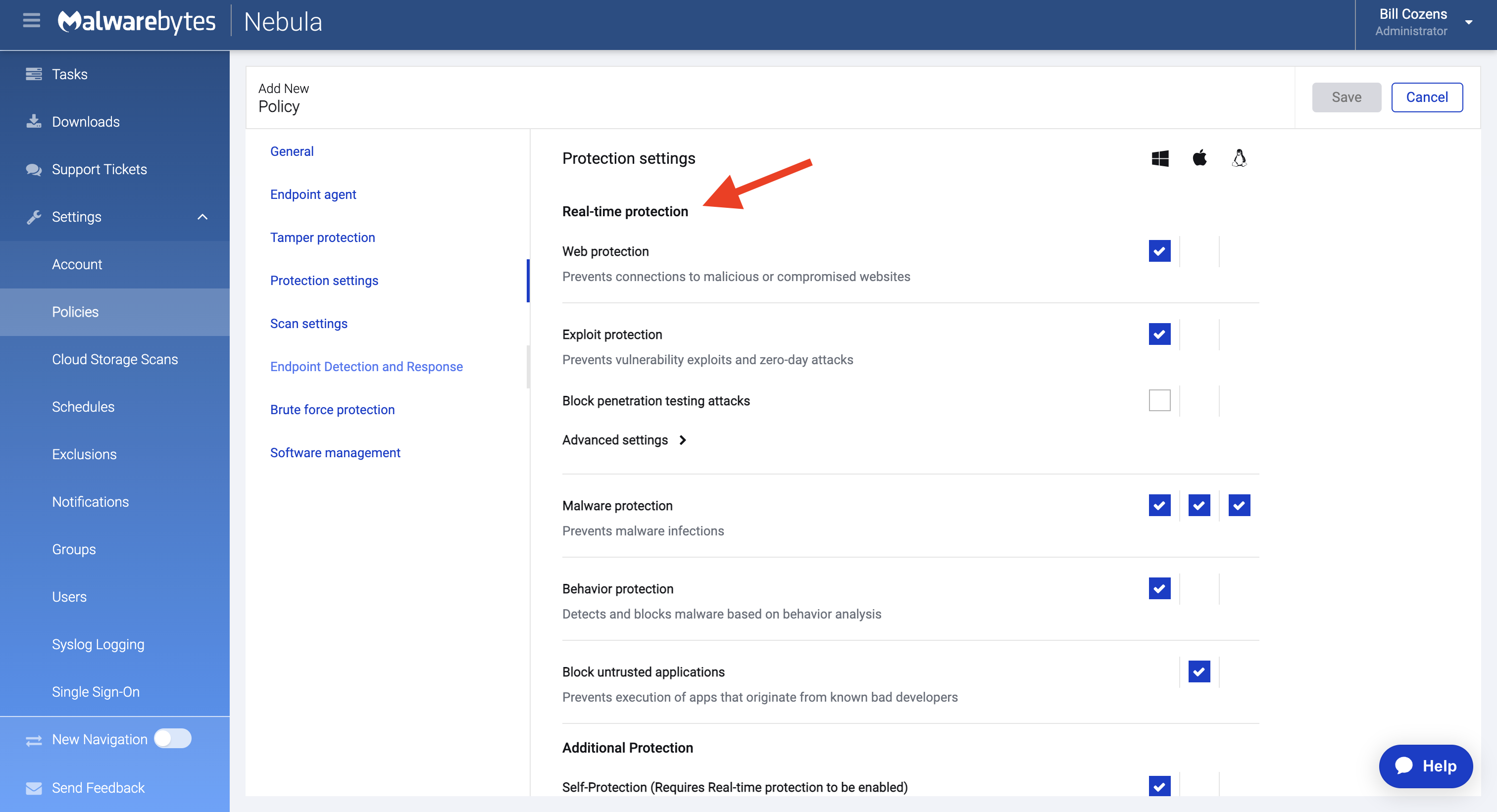
It is recommended to keep Real-time protection features enabled.
7. Enable Brute Force Protection (EP)
Enabling Brute Force Protection (BFP) on your console protects Windows endpoints from suspicious connections via remote devices. To learn how to configure BFP, see Configure Brute Force Protection in Nebula.
8. Toggle on Flight Recorder to enable endpoint data storage for threat investigation (EDR)
By default, Flight Recorder Search (FRS) data retention is disabled for all customers except for Managed Detection and Response (MDR) and active FRS users. Toggle on Flight Recorder to enable endpoint data storage for threat investigation.
For more information, see Flight Recorder in Nebula.
9. Enable Advanced settings for Suspicious Activity Monitoring
In the Endpoint Detection and Response settings tab in your policy, you’ll find checkboxes for Suspicious Activity Monitoring and more.
Under advanced settings of Suspicious Activity Monitoring, enable Collect networking events to include in searching to allow searching for contacted domains and IPs in flight recorder.
For servers, you must check Enable server operating system monitoring for suspicious activity under advanced settings to utilize EDR. For more information, see Configure Endpoint Detection and Response options in Malwarebytes Nebula.
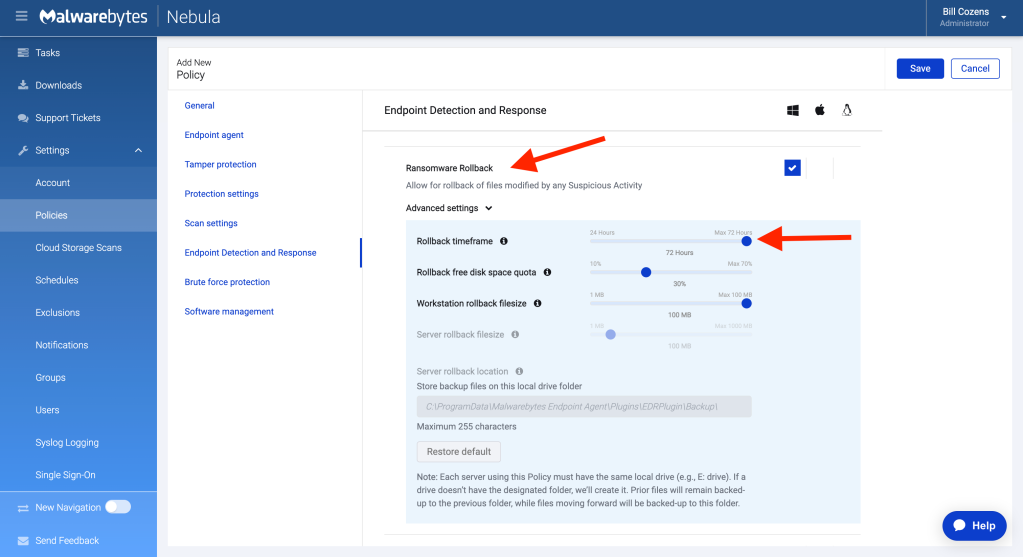
10. Enable Ransomware Rollback (EDR)
Enable Ransomware Rollback to allow for rollback of files modified by any Suspicious Activity. Set the rollback timeframe to 72 hours for maximum coverage.
For more information, see Configure Ransomware Rollback in Nebula.
Empowering our customers by expanding the Nebula platform
With an easy-to-use cloud dashboard and in-product automations, Malwarebytes Nebula enables teams of all skill levels to effectively maintain their endpoint security—and with these 10 best practices in mind, you can increase levels of performance and add extra-layers of protection.
Malwarebytes is constantly building upon the Nebula platform with new modules that simplify breach prevention, including Vulnerability Assessment & Patch Management, and DNS Filtering.
For more information on the Nebula platform and other product modules, visit: https://www.malwarebytes.com/business/cloud.
For a full list of best practices, see https://service.malwarebytes.com/hc/en-us/articles/7314370266643-Malwarebytes-Nebula-best-practices-guide
Have a burning question or want to learn more about our cyberprotection? Get a free business trial below.
More resources
Malwarebytes recognized as endpoint security leader by G2
Introducing Malwarebytes Managed Detection and Response (MDR)
How IT teams can prevent phishing attacks with Malwarebytes DNS filtering











