If you’re looking to send letters or parcels outside of the UK using Royal Mail, you’ll want to hold off for a little while. Royal Mail is suffering from “severe disruption” after an unnamed cyber incident.
While no specifics are currently available, Royal Mail has disclosed enough to let us know that the disruption is very bad indeed.
The statement reads as follows:
“We are temporarily unable to despatch items to overseas destinations. We strongly recommend that you temporarily hold any export mail items while we work to resolve the issue. Items that have already been despatched may be subject to delays. We would like to sincerely apologise to impacted customers for any disruption this incident is causing.
Our import operations continue to perform a full service, with some minor delays. Parcelforce Worldwide export services are still operating to all international destinations though customers should expect delays of one to two days.”
Hunting for clues
The attack is being investigated by third parties, but there’s no word currently with regard to how quickly the services will be back online. Royal Mail has told Bleeping Computer that domestic deliveries are unaffected, so for now people will just have to steer clear of anything overseas bound. This is of course a big problem for people selling items online, or simply sending items to friends and relatives.
Potentially more costly alternative solutions may have to be found until Royal Mail can get its services back up and running.
We will update this blog as more details are released.
Updated to add new information about LockBit Ransomware
More news broke overnight, pinning the blame for this one firmly in the direction of LockBit ransomware being responsible for the Royal Mail incident. LockBit, often found in our write ups and summaries, is one of the emerging stars in notorious ransomware compromise land. Some claim LockBit has ties to Russia, while the group itself claims to be based in The Netherlands. No self respecting ransomware group is going to confirm their real location, but for the time being anything related to point of origin is tied up in a fair amount of speculation. Speaking of speculation…
LockBit: Sorry, it wasn’t us
While the “public facing support” of the LockBit gang is denying responsibility for the attack, this claim feels rather tenuous as some researchers have pointed out.
If, somehow, the LockBit group is not behind the attack then at the very least, someone is using the LockBit gang encryptors like (for example) an affiliate. The links supplied via the ransom note link back to several “official” LockBit URLs such as customer support / negotiation, and data leak portal.
This would strongly suggest the LockBit group is behind it, yet they claim otherwise.
Is it more realistic that the LockBit back end has been compromised to allow for this to happen, or is it simply that the LockBit group itself did indeed carry out this attack? As Bleeping Computer notes, if this is someone other than the actual group carrying out the attack then it’s more along the lines of a destructive reputation damage campaign.
A system breakdown
The Telegraph is reporting that LockBit has infected devices used for printing labels for overseas parcel destinations. The somewhat underwhelming offer from the ransomware group to “decrypt one file for free” is considerably offset by the threat to publish stolen data on a LockBit operated dark web portal.
There is currently no word as to the specifics of the ransom demands. However, LockBit is in the business of big money hauls with possible extortion profits of around $100m covering a period of just several years. Not so long ago, car dealership Pendragon refused to pay a $60m ransom after their devices were attacked by LockBit. When we said big money hauls, we weren’t kidding.
The ever-popular LockBit
LockBit frequently sits at the top of our known ransomware by group charts.
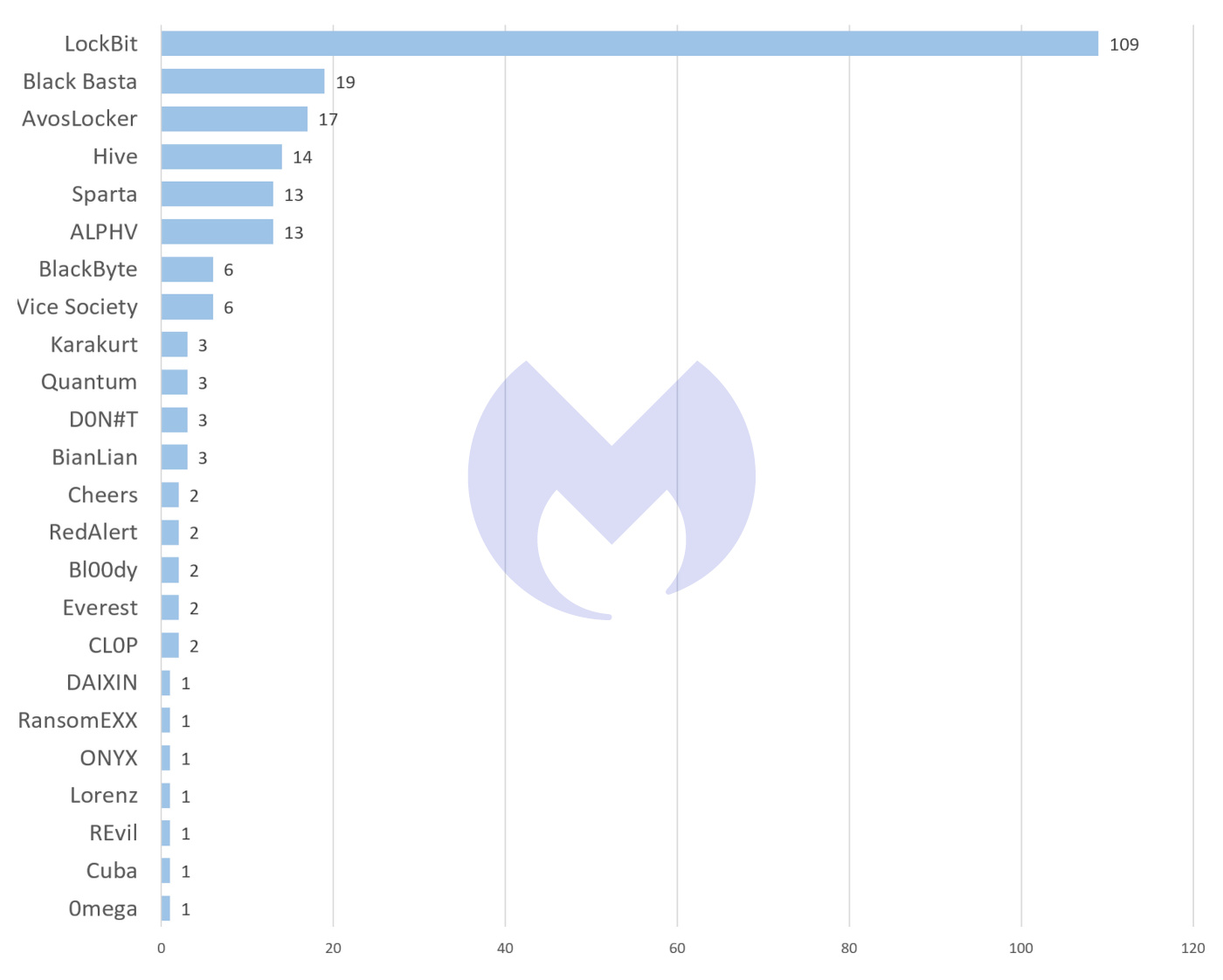
Known ransomware attacks by group, September 2022
In fact, it’s been quite the dominant force across 2022 and shows no sign of slowing down as the star player of the Ransomware as a Service (RaaS) team. The group, known for being overly chatty with its affiliates, even launched its own bug bounty program in June with up to one million dollars promised as a reward for discovering bugs and bounties.
Genuine offer or a way to drum up publicity? Either way, they’re almost never out of the news and this latest story is reinforcing that situation.
By September, LockBit was found in almost six times as many attacks as its next most prevalent rival, Black Basta. In fact, it accounted for 48% of known attacks, which was almost as many attacks as all of the other variants combined. Along the same lines, LockBit has proven to be the main and most consistent player in the RaaS stakes.
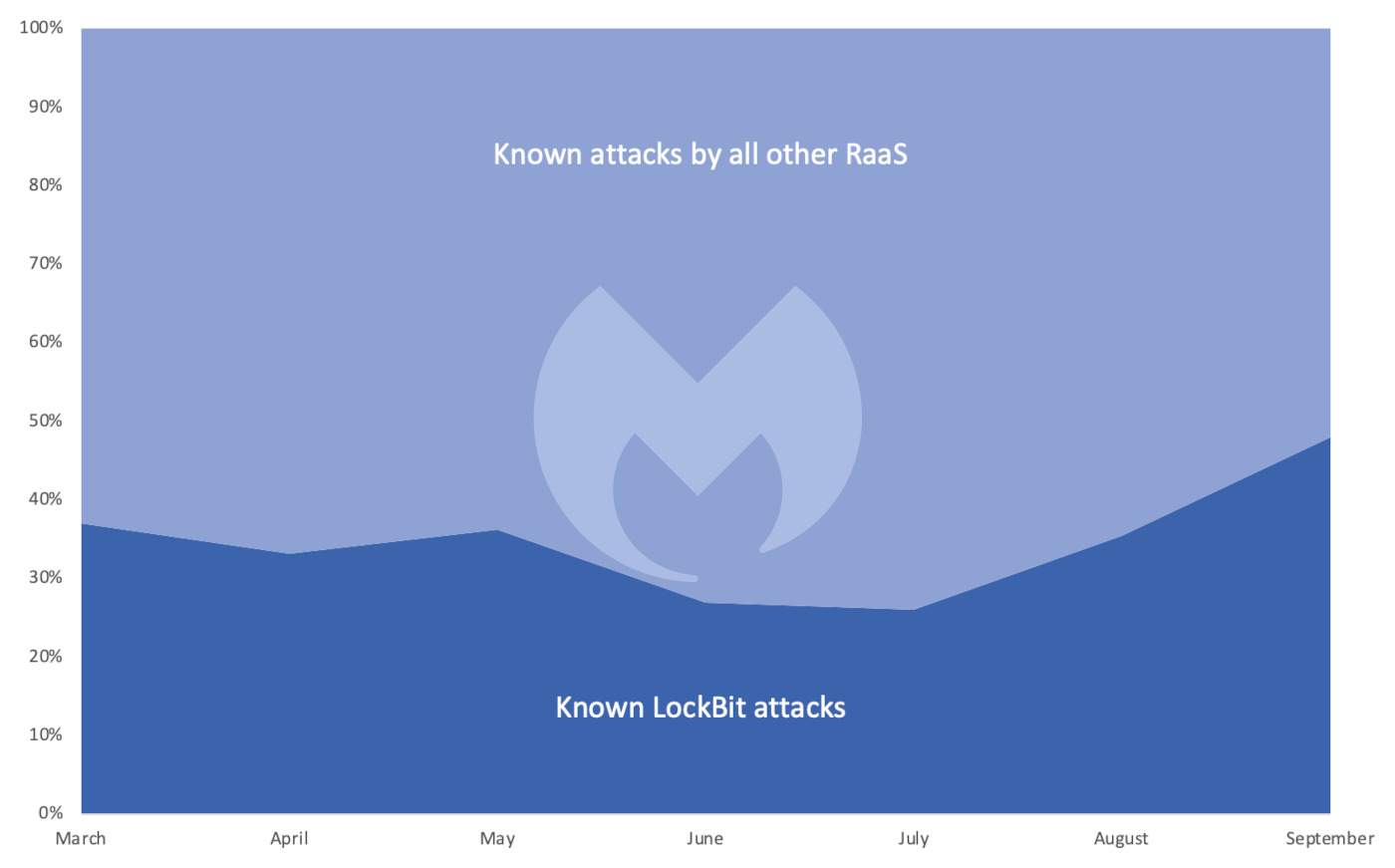
The share of known RaaS attacks involving LockBit
It remains to be seen if the compromised data will be leaked further down the line. For now, we’ll have to play the waiting game for something other than a parcel delivery.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.










