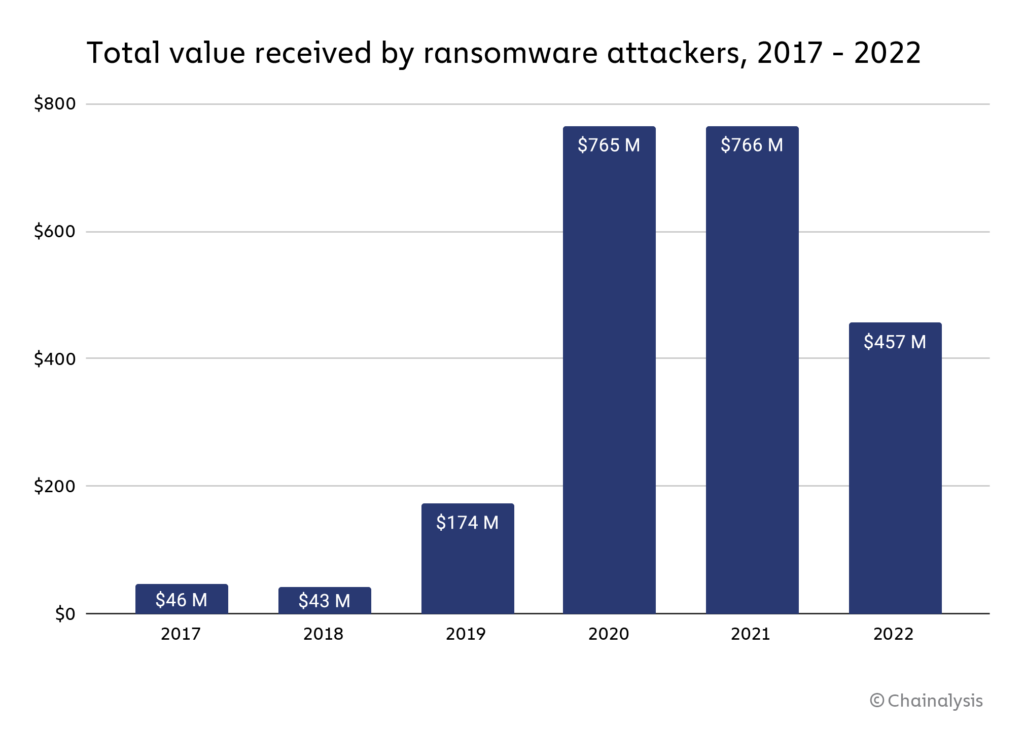
According to blockchain data platform Chainalysis, ransomware revenue “plummeted” from $765.6 in 2021 to at least $456.8 in 2022. The data is based on an analysis of the cryptocurrency addresses known to be controlled by ransomware attackers.
Precision
While the real numbers are likely much higher, it does present us with an idea of the development of ransomware payments. Last year’s estimate at this point seemed to show a decline from $765 million to $602 million, but turned out to be a small gain after correction.
Payments, not attacks
This decline could be explained in a number of ways:
- Fewer attacks
- Lower ransom demands or demand being negotiated down
- Fewer victims willing to pay
According to our own research and Chainalysis, the declining numbers are mainly due to victim organizations increasingly refusing to pay ransomware attackers.
Number of attacks
Ransomware attacks make headlines, but that doesn’t mean we learn about all of them. In fact, the chances of learning about an attack are bigger when the victim decides not to pay, since that will get them posted on a leak-site controlled by the ransomware group. Many ransomware operators use these sites to post data they exfiltrated during the attack as extra leverage to get victims to pay the ransom. Monitoring these sites always gives us a good idea of which ransomware groups are most active and how many victims actually refuse to pay.
According to IT service provider AAG, there were 236.1 million ransomware attacks worldwide in just the first half of 2022. Through 2021, there were 623.3 million ransomware attacks globally. That seems to indicate the number of attacks could be slightly down.
Negotiators
One thing victims have learned is that ransomware sums can be negotiated down. In fact, a new form of ransomware response has emerged in the past year—the ransomware negotiator. On our Lock & Code podcast, Calling in the ransomware negotiator, with Kurtis Minder: Lock and Code S03E20, Kurtis Minder talk about how he has helped clients with ransomware negotiation and his company has worked to formalize ransomware negotiation training.
Not willing to pay
There are many reasons, besides the obvious one, that companies are unwilling to meet the ransom demands:
- Paying keeps the ransomware eco-system alive
- There is no guarantee you will get your systems back
- It is no immediate cure, it sometimes takes just as long as restoring your systems from backups
- Organizations have learned the importance of backups
- In some cases it is prohibited due to embargoes and sanctions against certain countries
Sometimes organizations feel they have no other choice, which is understandable, but it gives us hope to see that the numbers are declining.
Continental
In our ransomware review of October 2022 we highlighted the case of automotive parts giant Continental. According to a transcript of the negotiations, obtained from LockBit’s dark web site, ransom negotiations began on September 23 and progressed slowly for a month. In the transcript, Continental sought proof that the ransomware group had the 40 terabytes of internal company data it claimed to have stolen, and then asked for assurances that the group would delete the data if the ransom was paid.
The final message attributed to Continental, dated October 24, reads “Hello, we have to hold a management meeting and will come back to you tomorrow end of business day.” It seems that the meeting did not go the way that LockBit hoped, and after several fruitless days trying to restart the negotiation, the ransomware group has made the Continental data available on its dark web site—for sale or destruction—for $50 million. It is unknown whether anyone shelled out that amount to obtain the stolen data.
Chainalysis queried several ransomware experts and is convinced that the drop in revenue is due to more victims refusing to pay. For those interested, the report provides a lot more details.
We don’t just report on threats—we remove them
Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by downloading Malwarebytes today.











