QBot, an infostealer-turned-dropper that aids criminal gangs in their malicious campaigns, is now being distributed as part of a phishing campaign using PDFs and Windows Script Files (WSF), according to recent discoveries by malware hunter Proxylife (@pr0xylife) and the Cryptolaemus group (@Cryptolaemus1).
The last time QBot (aka QakBot) had its modus operandi changed was in November. Campaign operators adopted tactics from Magniber’s playbook to successfully exploit a Mark of the Web (MotW) zero-day flaw to run a JavaScript (JS) that executed QBot.
The latest QBot phishing campaign is illustrated simply in the diagram below:
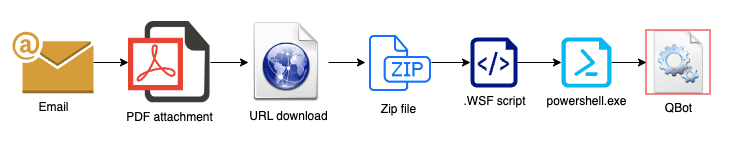
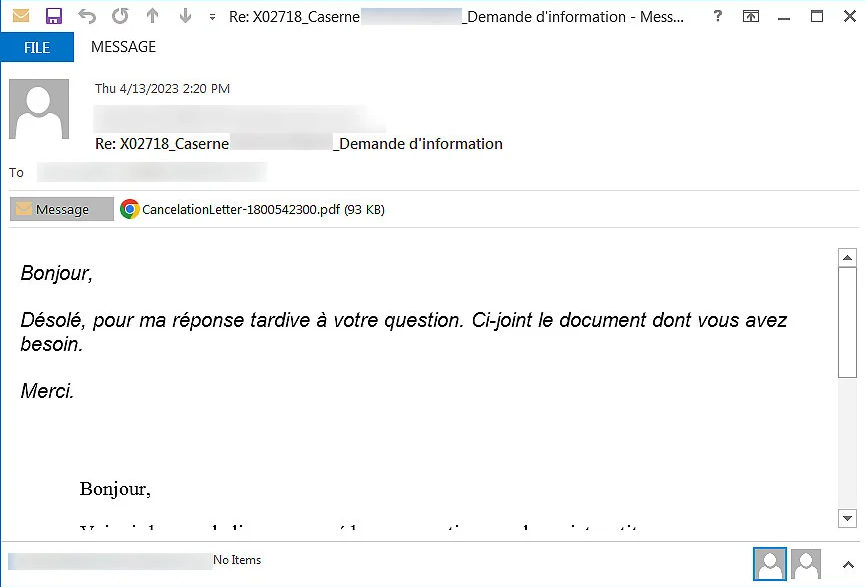
The attack starts with a reply-chain phishing email, when threat actors reply to a chain of emails with a malicious link or attachment. BleepingComputer has noted that these phishing emails use a variety of languages. This means the language barrier is absent in such an attack, so any business from any part of the world could be affected.
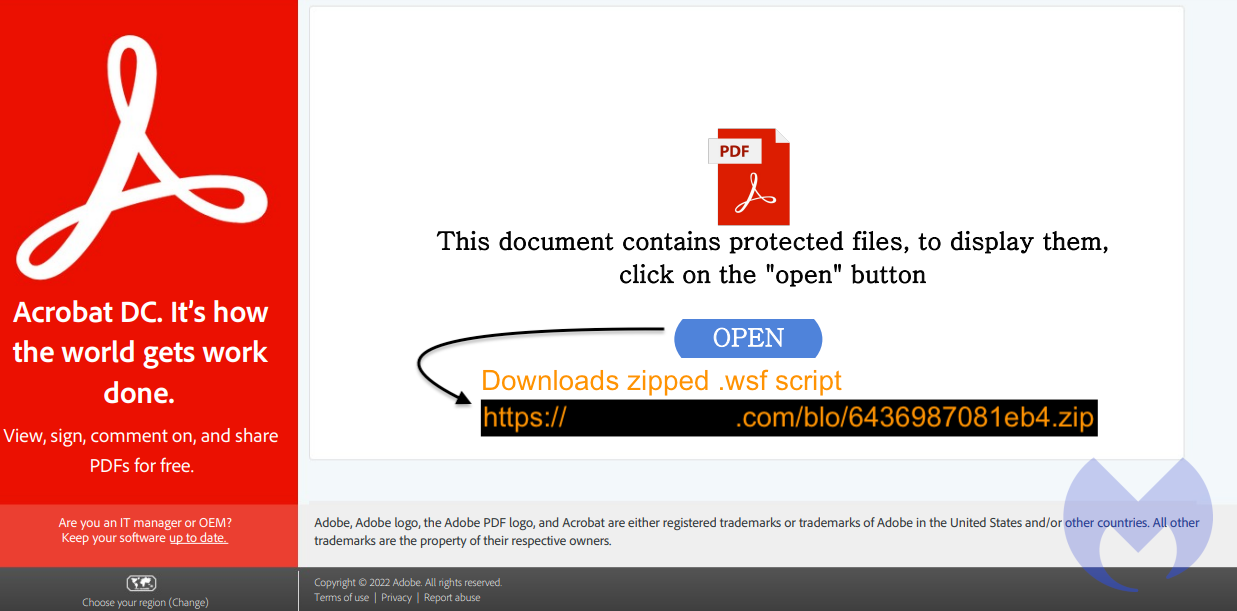
Once someone in the email chain opens the attached PDF, they see a message saying, “This document contains protected files, to display them, click on the ‘open’ button.” Clicking the button downloads a ZIP file containing the WSF script.
The heavily obfuscated script contains a mix of JS and VBScript code that, when run, triggers a PowerShell that then downloads the QBot DLL from a list of hardcoded URLs. This script tries each URL until a file is downloaded to the Windows Temp folder (%TEMP%) and executed.
Once QBot runs, it issues a PING command to check for an internet connection. It then injects itself into wermgr.exe, a legitimate Windows Error Manager program, to run quietly in the background.
Because QBot is said to be used by operators of ransomware-as-a-service (RaaS) offerings, its presence in company systems could be disastrous. Therefore, any organization must take its QBot-infected systems offline as soon as possible and thoroughly scan and review network logs for unusual behavior.
The DFIR Report in February 2022 showed QBot collecting data from a compromised system 30 minutes after infecting it. Within an hour, QBot can be spread to adjacent systems.
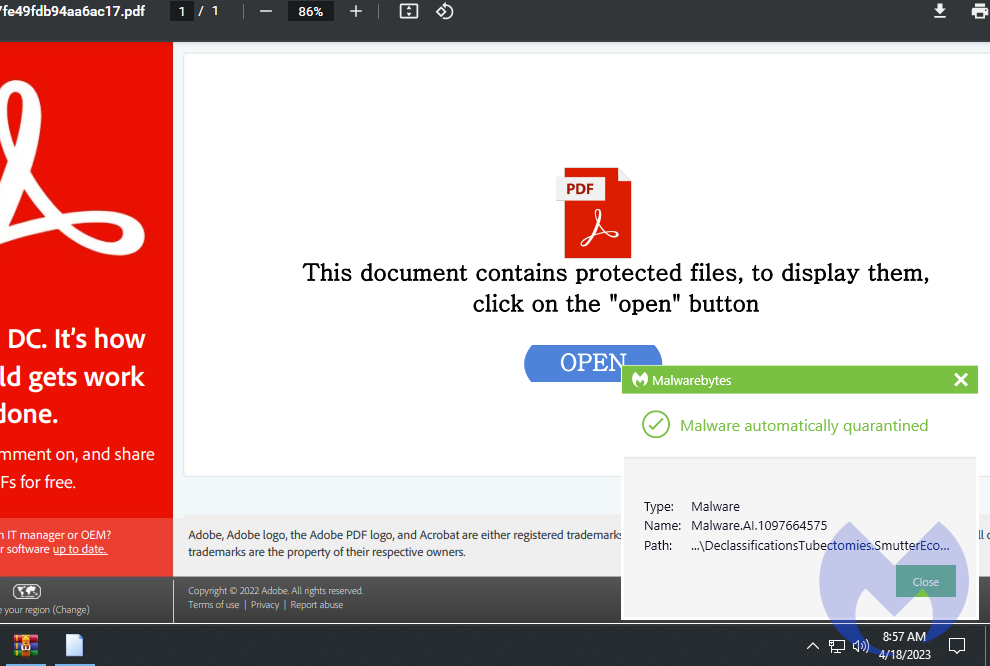
Malwarebytes detects the malicious DLL (QBot).
Malwarebytes removes all remnants of ransomware and prevents you from getting reinfected. Want to learn more about how we can help protect your business? Get a free trial below.










