
ALPHV is singling out healthcare sector, say FBI and CISA
In an updated #StopRansomware security advisory, the Cybersecurity and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI), and the Department of Health and Human Services (HHS) has warned the healthcare industry about the danger of the ALPHV ransomware group, also known as Blackcat. According to the advisory:
Since mid-December 2023, of the nearly 70 leaked victims, the healthcare sector has been the most commonly victimized.
We have reported in the past that ransomware groups show absolutely no respect to previous promises to leave the healthcare sector alone. This is not a new phenomenon, but ALPHV focusing on healthcare specifically is a relatively new one.
On the grapevine you can hear that ALPHV asked their affiliates to focus on this industry as a kind of payback for the disruptions to their infrastructure in December last year by law enforcement.
The recent attack on Change Healthcare has been reportedly caused by ALPHV, but we don’t feel it’s right to say that they didn’t attack healthcare way before the said disruption.
And unfortunately ALPHV is not the only one. In a new low, the attack on Lurie Children’s Hospital has been claimed by the Rhysida ransomware group.
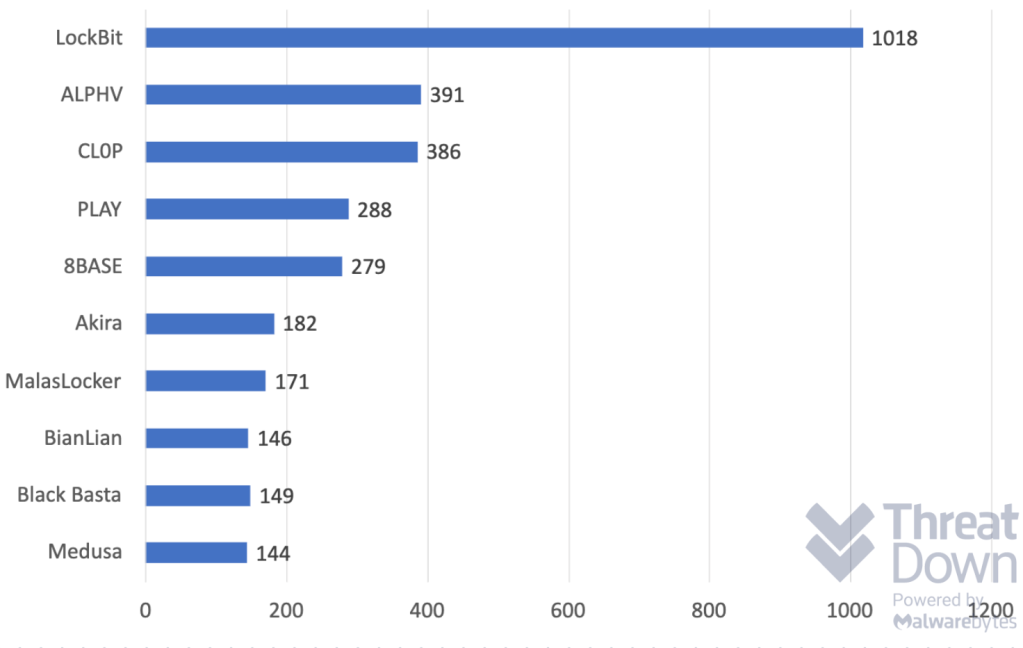
ALPHV is a Ransomware-as-a-Service (RaaS) group, meaning that its ransomware is made available to criminal affiliates using a software-as-a-service (SaaS) business model. ALPHV was ranked second in the list of most active big game ransomware groups of 2023.
According to the advisory, ALPHV’s affiliates use advanced social engineering techniques and open source research on a company to gain initial access. They pose as company IT and/or helpdesk staff and use phone calls or SMS messages to obtain credentials from employees to access the target network. After the initial breach they deploy remote access software such as AnyDesk, Mega sync, and Splashtop to prepare the theft of data from the network.
From the initial access they use various other legitimate, living off the land (LOTL), tools to further their access. Once the data has been safely moved to their Dropbox or Mega accounts, the ransomware is deployed to encrypt machines in the network. The latest ALPHV Blackcat update has the capability to encrypt both Windows and Linux devices, as well as VMWare instances.
It is unclear how ALPHV would stimulate attacks on healthcare institutions among its affiliates. We do understand that some of the data found during these attacks is very valuable on the underground market.
Having seen how devastating attacks on healthcare can be, we would encourage every cybercriminal involved to waive their right to be treated in any healthcare facility. Or, at least, try and realize the damage they are doing and the potential impact on people’s health.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like ThreatDown EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.




