Recently a Microsoft blog was released describing a new Facebook Trojan classified as JS.Febipos.A by several AV vendors. Febipos is currently active in Brazil and takes control of your Facebook profile using a Firefox and/or Chrome extension that’s installed during execution. I managed to obtain several copies of the Febipos executable, which uses Facebook-like icons in an attempt to appear legitimate, along with being signed by digital certificates from ‘Updates LTD’.
According to Microsoft’s report, Febipos beacons to a C2 server and receives the following commands:
– Liking a page – Sharing a post – Posting messages – Joining a group – Inviting your friends to a group – Sending messages and links via chat – Commenting on posts
Febipos is packaged in a self-extracting archive (SFX) and is coded to silently install into the user’s temporary directory (%temp%). The Trojan’s main component is called ‘fbinstupd.exe’, appearing to be shorthand for ‘Facebook Install Update’. All program strings are in Portuguese, Brazil’s official language.
Upon execution you’ll also get a confirmation dialog that translates to ‘Installation completed successfully!’ Glad to know there weren’t any errors =)
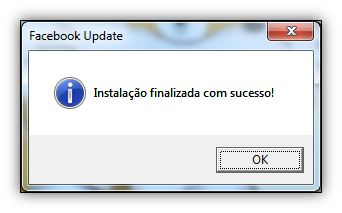
In the image below, you’ll also see the results from a regshot capture; notice the installed Firefox extension that was place in my profile directory. The Chrome extension was dropped in the %temp% directory along with the Trojan and another PE file.
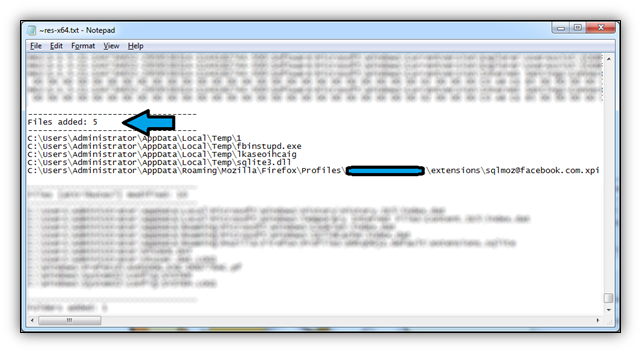
Febipos’ main component is heavily armored, and was passed through a software protection system known as ‘Obsidium’. You can check it out at http://www.obsidium.de/ for more information. While many programs like Obsidium, VMProtect, Themida, intend to protect commercial software products from piracy and reverse-engineering, they’re also used frequently to fortify malware. This has caused some AV vendors to flag files as malicious if they’re been processed by these protection systems.
Unfortunately, I couldn’t get a copy of Febipos that still had a live C2 server, so I wasn’t too interested in doing any further analysis; however, Febipos along with Facbook scams attest to the fact that social media has come under heavy fire from blackhat cyber-criminals. As platforms like Facebook and Twitter allow everyone to be constantly connected, hackers have a new way to ‘connect’ with us.
On underground forums, for instance, it’s very common to see posts offering techniques to hack accounts, generate likes, etc. A lot of these tricks involve social engineering and sometimes exploiting Facebook’s password recovery options.
This has brought about a whole new market for many, who buy and sell Facbook traffic to the highest bidder. If you remember back in January I did a post on Malwarebiter, a Malwarebytes imitator with a Facebook page containing a suspicious number of likes, probably attributed to this kind of behavior.
With that being said, a word to the wise for our readers: safeguard your social media accounts like you would your email account, bank account, or other online account containing personal information. As sites like Facebook continue to integrate into much of our lives, we find that it’s used for much more than stating what’s on our minds. Now we can login to other websites with our Facebook credentials, and sites like Twitter allow us to retrieve news that may influence our everyday decisions. For example, the Associated Press (AP) Twitter account hack of last month briefly impacted the stock market, causing a noticeable drop in the DOW after a fabricated tweet of White House explosions.
What’s more, the threat of malware targeting social media is becoming more apparent, as evidenced by Febipos. While current threats like Febipos are isolated and aren’t capable of doing irreparable harm, Facebook malware is still in its infancy stages, and is sure to advance given ample time. Reports are already surfacing of users creating Facebook botnets, leveraging the power and connectivity of social media to do their dirty work.
However, in Facebook’s defense, the social media giant hasn’t remained quiet amidst the attacks on its users. In recent times, there have been many security updates to password recovery, account creation, and a huge crackdown on fake profiles. Today if you created a new Facebook profile, you’d notice you have to verify who you are, not only with a captcha, but by providing a phone number to retrieve an SMS code needed for account activation.
We all need to follow ‘common sense’ guidelines to keep our Facebook profile safe, along with other online accounts. For Facebook, this includes ignoring Friend requests from unknown/suspicious persons, and not following any links you don’t trust, even if they’re posted by friends. These could be Clickjack scams or other malicious links that exploit your browser, exposing your private information or your computer to malware. Falling victim to these traps might be easier than you think, as a hyperlink may initially appear harmless on the surface. Exercise caution when using all forms of social media and make sure you’re using strong passwords, or a Password Manager. Check out this article if you need help with that part.
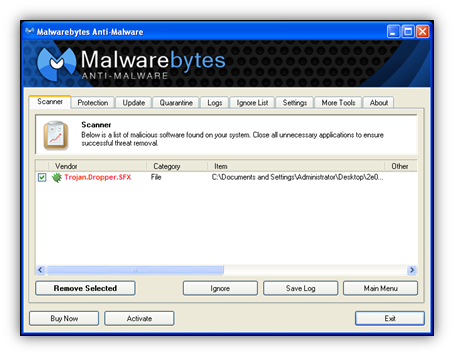
One final word to our readers: users of Malwarebytes Anti-Malware will be happy to know that JS.Febipos.A is detected as Trojan.Dropper.SFX. Make sure to stay tuned to Unpacked for any updates on social media malware.
_______________________________________________________________________________
Joshua Cannell is a Malware Intelligence Analyst at Malwarebytes where he performs research and in-depth analysis on current malware threats. He has over 5 years of experience working with US defense intelligence agencies where he analyzed malware and developed defense strategies through reverse engineering techniques. His articles on the Unpacked blog feature the latest news in malware as well as full-length technical analysis. Follow him on Twitter @joshcannell











