Last year, we documented a new social engineering toolkit we called “Domen” being used in the wild. Threat actors were using this kit to trick visitors into visiting compromised websites and installing malware under the guise of a browser update or missing font.
Despite being a robust toolkit, we only saw Domen in sporadic campaigns last year, often reusing the same infrastructure that had already been partially disrupted. However, we recently came across a new malvertising campaign with brand new infrastructure that shows Domen is still being used by threat actors.
Even though Domen shares similarities with other social engineering templates, it is unique in its own ways. The client-side JavaScript responsible for the fake updates is one of the most thorough and professional coding jobs we had ever seen.
Previously, we had observed Domen pushing the NetSupport RAT and Predator the thief using its own custom downloader. This time, we noticed a change where the threat actor seems to be experimenting with Smoke Loader, followed by several different payloads.
Domen: the origins
We published our original blog in September 2019, however Domen had been active for several months already. We confirmed this when we found an advertisement posted in a blackhat forum in April 2019 that promoted the toolkit as a way to install EXEs and APKs.
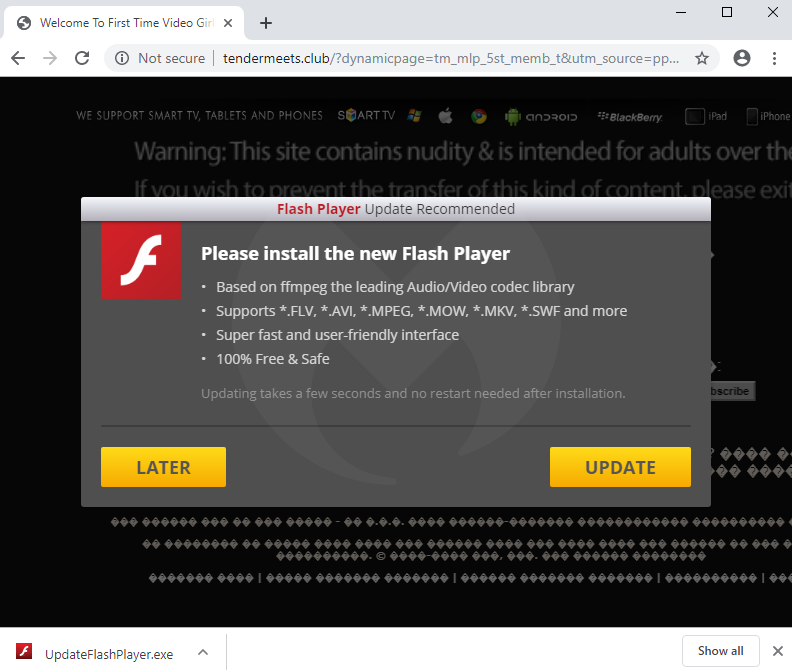
A couple months after our blog, we observed Domen in another campaign—probably carried out by the same threat actor. However, unlike the former one that had been used on compromised websites, this time it was via a malvertising chain (celeritascdn[.]com) leading to a decoy adult site hosted at tendermeets[.]club (a copycat of ftvgirls[.]com).
The reason we believe the two campaigns are related is because the delivery vector for the payload uses the same technique, namely uploading malicious files to Bitbucket.

Between the end of November 2019 and most of February 2020, Domen fell fairly silent.
Latest Domen campaign
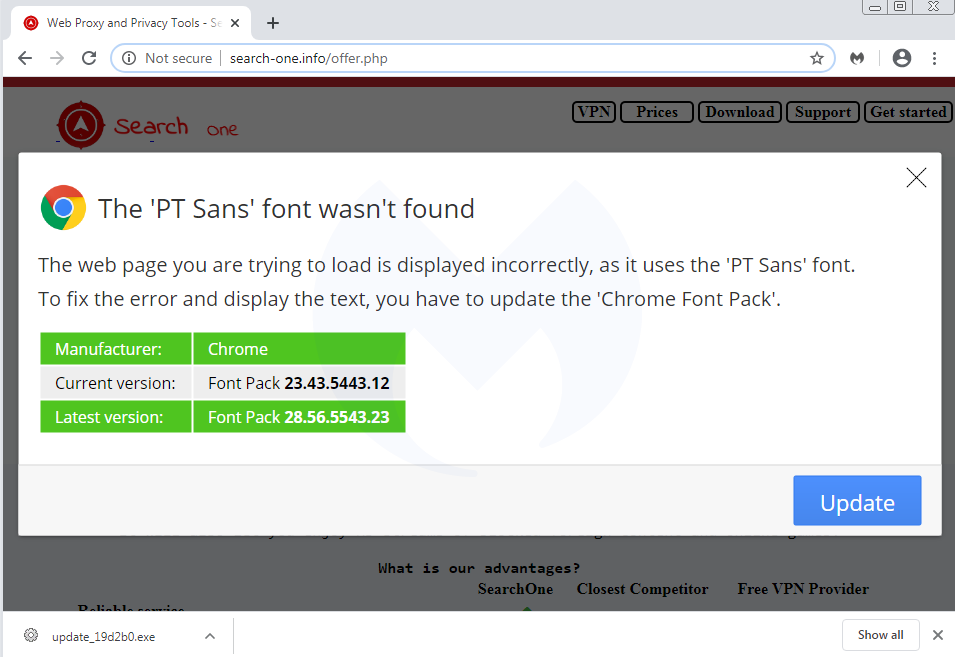
On February 19, we caught a new malvertising chain with new domains, this time using a VPN service as a lure.
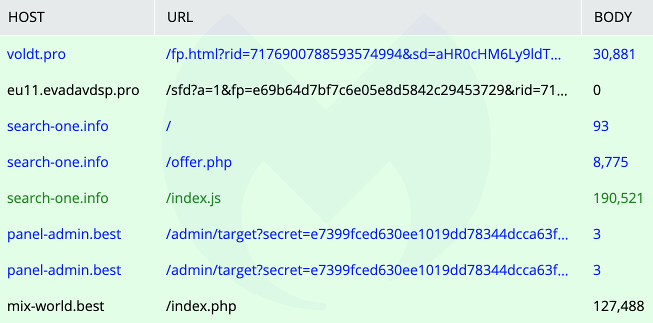
The threat actor had just created new infrastructure to host the fraudulent page (search-one[.]info), the download site (mix-world[.]best), and the backend panel (panel-admin[.]best).
The payload is this infection chain is Smoke Loader. In one instance, Smoke Loader distributed several secondary payloads, including the IntelRapid cryptominer, a Vidar stealer, and Buran ransomware.
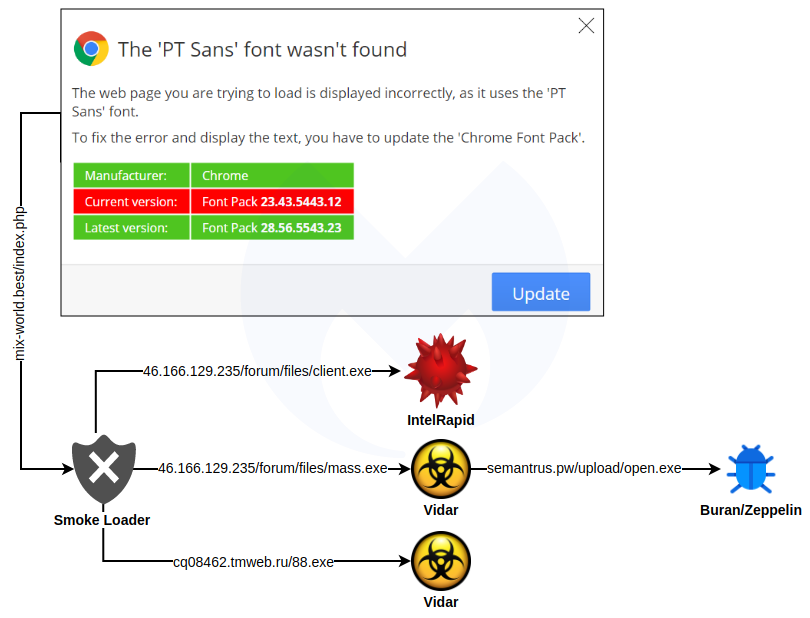
This is an interesting payload combination that seems to be more common these days.
More social engineering schemes
Domen is a well-made toolkit that has been used to distribute a variety of payloads by using tried and tested social engineering tricks. While tracking its author (or distributor), we noticed other forum postings advertising the same sort of payload installs, but using different and creative themes.
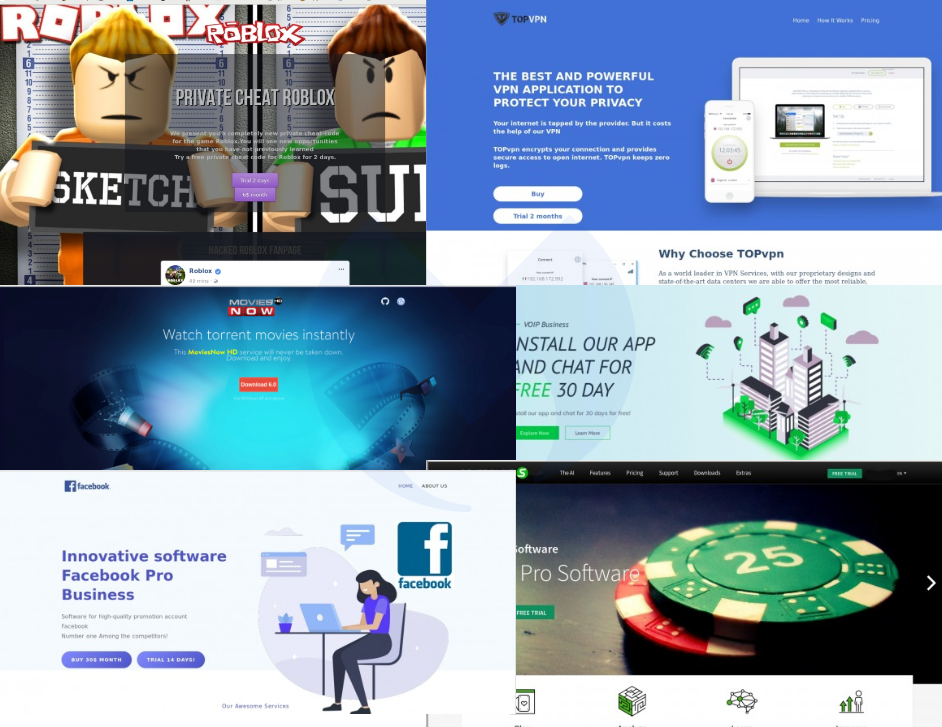
The concept is the same, namely, those bogus sites are tempting users to download software that happens to be malware.
Since the decline in browser exploits in recent years, threat actors have migrated toward other infection vectors. As far as web threats are concerned, social engineering remains highly effective.
Malwarebytes business and Malwarebytes for Windows Premium users are already protected against this distribution campaign and its accompanying payloads.
Indicators of Compromise
Domen toolkit
search-one[.]info
panel-admin[.]best
mix-world[.]best
Smoke Loader
1a91b2a3a252554842de875c89f6eee105bc419d7e32d3a5c9f0f9078780ab30
vuterfaste[.]ru
IntelRapid
46.166.129[.]235/forum/files/client.exe
33d5f80242b4006ce14bba56692e1936157e0216b93faac823c42cc3f9ab4ec1
Vidar
46.166.129[.]235/forum/files/mass.exe
76ce130d2447f71bea8ed902959fd7e0aeac86b55f9e44a327c1f1c1bd73ba3f
molothunsen[.]com
Buran/Zeppelin
semantrus.pw/upload/open.exe
0163bb148d4eb632d00d6d3080e07bba46f2f3549e8f95a8ca8951c10280694f
Vidar
cq08462.tmweb[.]ru/88.exe
628a9c97a55155f60d3b5ae29bc64f1dca5a6baf2b4f6a1a1de5e836cd4fb73f
desperate[.]website










