Malwarebytes Threat Intelligence builds a monthly picture of ransomware activity by monitoring the information published by ransomware gangs on their Dark Web leak sites. This information represents victims who were successfully attacked but opted not to pay a ransom.
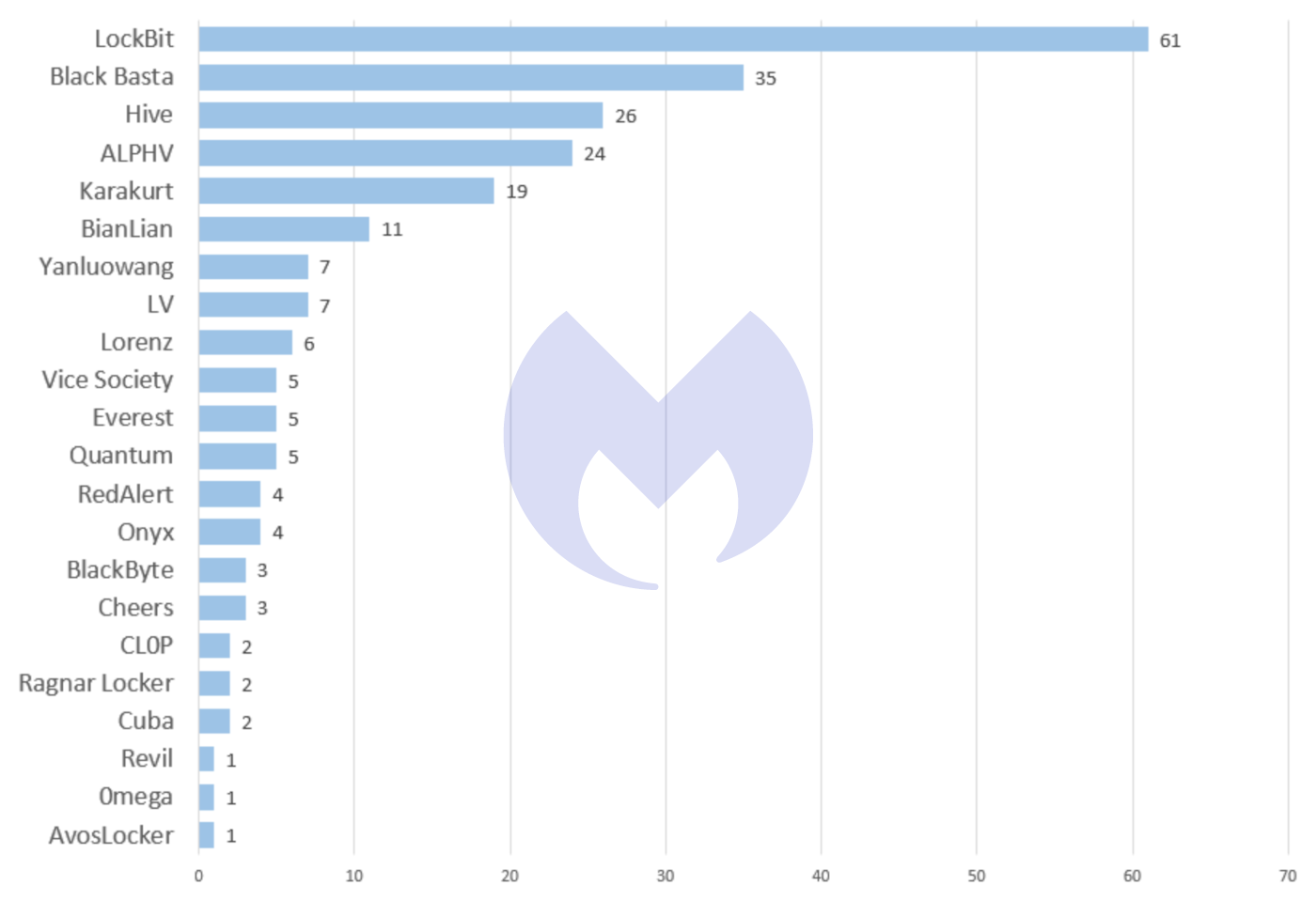
In July, LockBit maintained the place it has occupied all year as the most active ransomware variant. Notably, BlackBasta, a relatively new ransomware variant that first appeared in April, took the place occupied by Conti for much of the year as the second most active variant. BlackBasta has been strongly linked to the gang behind Conti and may be the closest thing it has to a successor.
Two other gangs linked to Conti, Hive and KaraKurt, were also very active during July, ensuring that the gang behind “the costliest strain of ransomware ever documented” by the FBI continues to cast a long shadow, despite the retirement of the Conti “brand”.
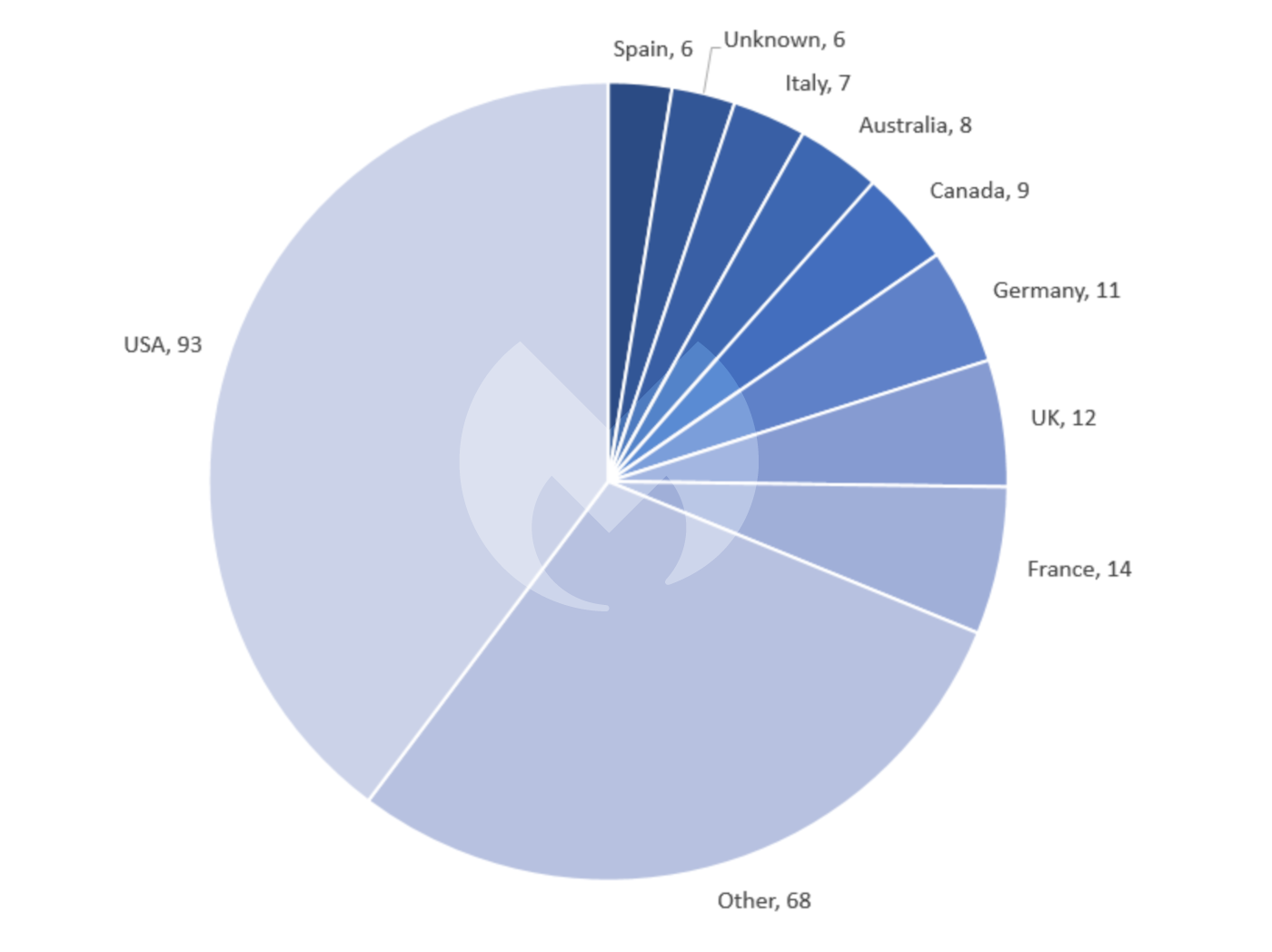
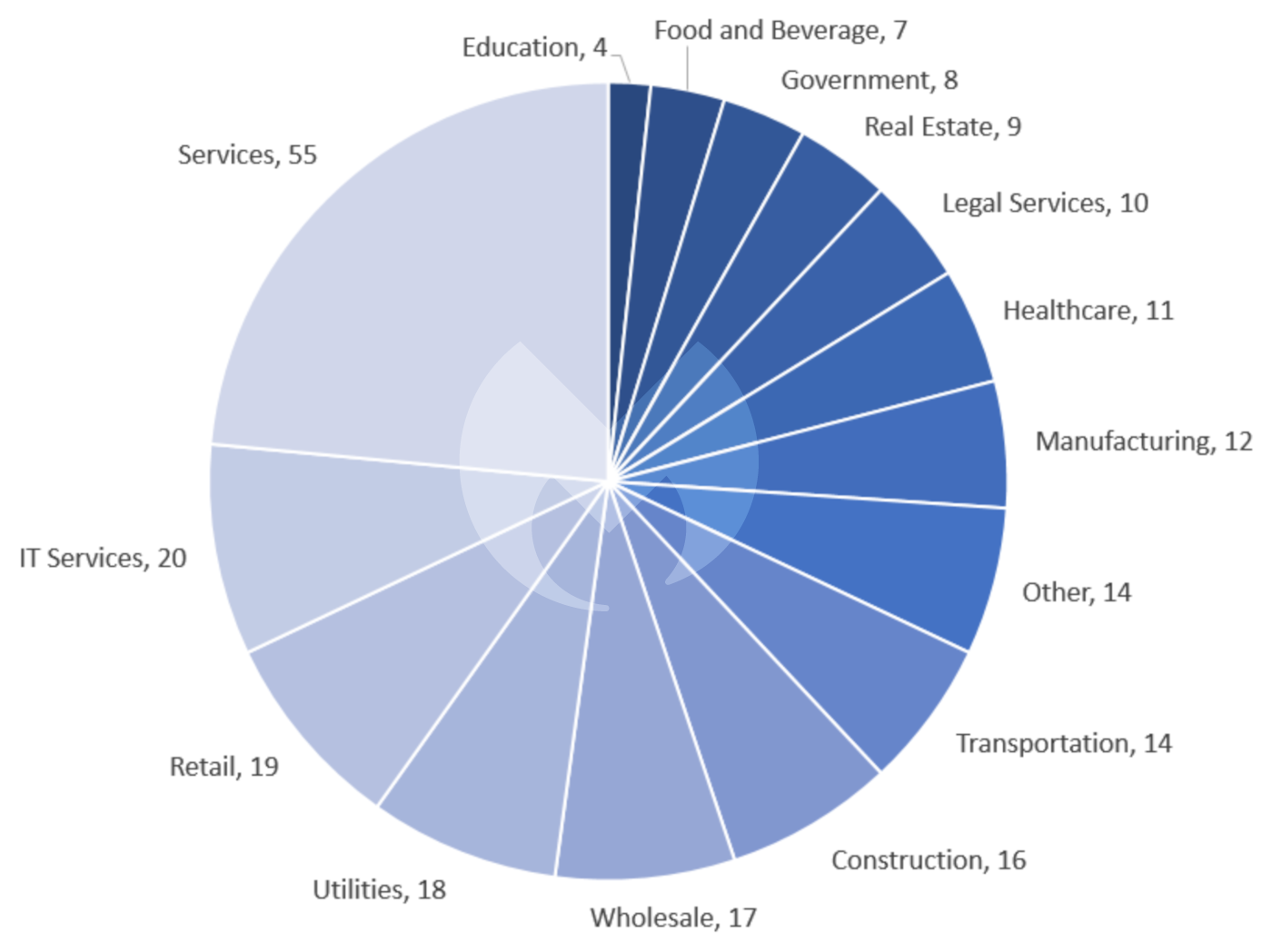
The international picture followed a familiar pattern, with the USA suffering the largest number of attacks by far, distantly followed by a collection of the largest European economies. Services remained the sector most afflicted, suffering almost a quarter of all attacks.
LockBit
We wrote extensively about LockBit, and the appearance of LockBit 3.0, in last month’s ransomware review. Part of the gang’s success seems to have come from simply avoiding the attention-seeking pitfalls of other gangs. We wrote “…while some ransomware gangs seem to want to tell the world what they think, and how great they are, LockBit seems to care more about what its users think.”
Perhaps we spoke to soon. In July LockBit responded to an interview request by Red Hot Cyber in which it trotted out it’s version of the careworn old nonsense that criminal hackers help security, saying “we are ordinary pentesters and make this world safer”. Thanks to the gang’s threats and ruthless exploitation “companies can learn a security lesson and close vulnerabilities”, apparently. Whatever helps you sleep at night, we suppose.
The interview did contain some useful information too though, revealing that between 10%-50% of LockBit victims pay the ransom. The numbers we report each month are victims who appear on leak sites because they have not paid the ransom, so this tidbit helps us understand the true scale of the ransomware problem.
The interviewee also confirmed the suspected relationship between LockBit 3.0 (also known as LockBit Black) and DarkSide/BlackMatter ransomware, revealing that the LockBit gang paid for DarkSide source code and based the latest version of its ransomware on it. If DarkSide sounds familiar, you may recall that it was the ransomware used in the infamous Colonial Pipeline attack. The DarkSide gang disappeared shortly after the attack “due to the pressure from the US”, only to reemerge as BlackMatter in July, before disappearing again in October 2021, again due to pressure from “authorities”.
BlackBasta
BlackBasta was the second most prolific ransomware variant behind LockBit in July, and it has occupied either the second or third place in our list ever since May, having only emerged the month before.
It burst into existence in April with 11 known victims. Being able to hit so many victims in its first month led some to speculate that it must be the work of an established gang that had a network of experienced affiliates in place, ready to work. It has since been linked to the gang behind the recently retired Conti ransomware, with which it enjoys an eye-catching overlap.
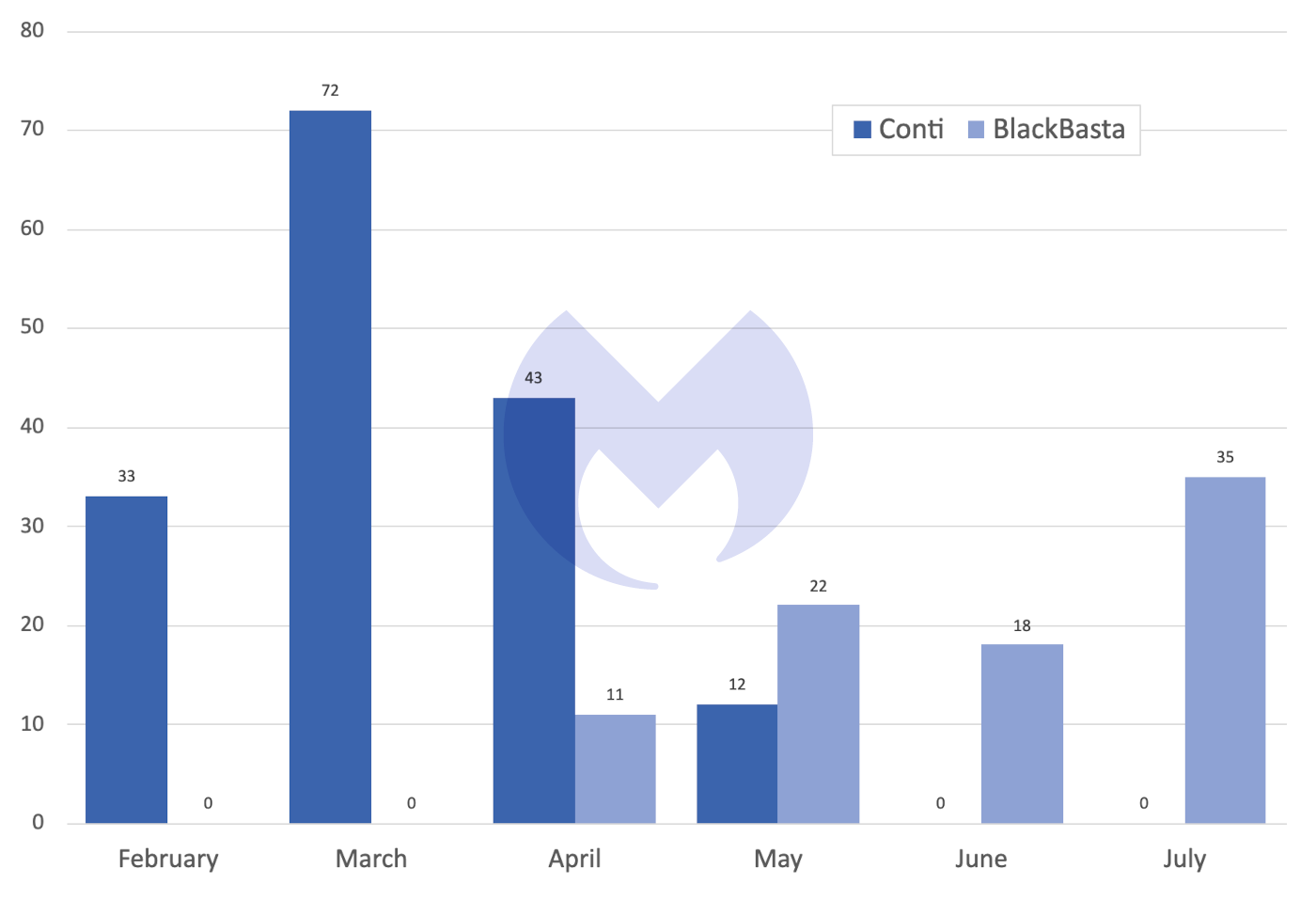
As we reported in May and June, Conti hatched a scheme to fake its own death this year, after its support for Russia’s invasion of Ukraine caused ransom payments to dry up. Members of the gang were alleged dispersed to other “brands” owned by the Conti gang, as well as other gangs it had a relationship with.
Apparent beneficiaries included operators of three of the five most prevalent ransomware variants in July: BlackBasta, Hive, and the resurgent KaraKurt.
REvil returns
July was also notable for the reappearance of REvil, aka Sodinokibi, perhaps the most notorious name in ransomware. A single victim appeared on the gang’s Tor leak site in July, the first since May.
While many other groups were far more active, the group’s reputation ensures that any sign of life demands to be taken seriously.
REvil is responsible for two of the most significant ransomware attacks in history: The 2021 attack on JBS, the world’s largest meat processing company, and an enormous, cascading supply-chain attack against Kaseya VSA and its customers a month later. The attack on Kaseya was ultimately resolved when the company announced that it had acquired the decryption key needed to free the victims, without paying REvil its $70 million ransom demand. The source of the key was later revealed to have been the FBI, which had successfully infiltrated the group’s infrastructure.
Since then REvil has led a stop-start existence. Under pressure from US law enforcement, the gang went dark in July 2021. It reappeared a few months later before being forced offline when its infrastructure was hijacked by a multi-country law enforcement operation in October.
In January, in a highly unusual move, eight of its members were arrested in Russia by the FSB. However, even that wasn’t enough to keep the gang down for long. It’s infrastructure sparked back into life in April before going dark again, only for it to reappear in July.
New gangs appear
Last month also saw a glut of new ransomware gangs appear. The newcomers in our list are BianLian, Yanluowang, 0mega, Cheers, and RedAlert. With 11 known victims, the debut of BianLian is comparable in size to the appearance of BlackBasta in April, so we will be watching it closely in August.