This article is based on research by Marcelo Rivero, Malwarebytes’ ransomware specialist, who monitors information published by ransomware gangs on their Dark Web sites. In this report, “known attacks” are those where the victim didn’t pay a ransom. This provides the best overall picture of ransomware activity, but the true number of attacks is far higher.
In April, LockBit maintained its position as the top ransomware attacker and was also observed expanding into the Mac space. Meanwhile, Cl0p, which dramatically expanded its attack operations in March, has gone quiet this month, despite Microsoft observing them exploiting PaperCut vulnerabilities.
LockBit’s macOS ransomware is an interesting development in the threat landscape, showing that the group is dipping its toes into the historically ransomware-free Mac environment. The variant, targeting macOS arm64 architecture, first appeared on VirusTotal in November and December 2022 but went unnoticed until late April when it was discovered by MalwareHunterTeam.
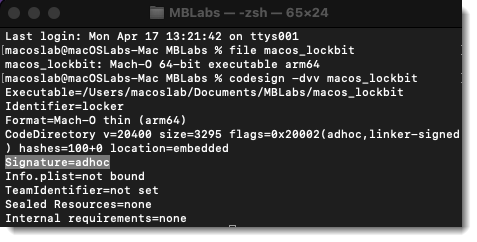
The LockBit macOS samples analyzed by Malwarebytes seem ineffective due to being unsigned, not accounting for TCC/SIP restrictions, and being riddled with bugs, like buffer overflows, causing premature termination when executed on macOS.
“The LockBit encryptor doesn’t look particularly viable in its current form, but I’m definitely going to be keeping an eye on it,” says Thomas Reed, director of Mac and mobile platforms at Malwarebytes. “The viability may improve in the future. Or it may not, if their tests aren’t promising.”
Keep an eye out, because LockBit’s work in developing a macOS ransomware variant—plagued though it may currently be—could signal a trend toward more Mac-targeting ransomware in the future.
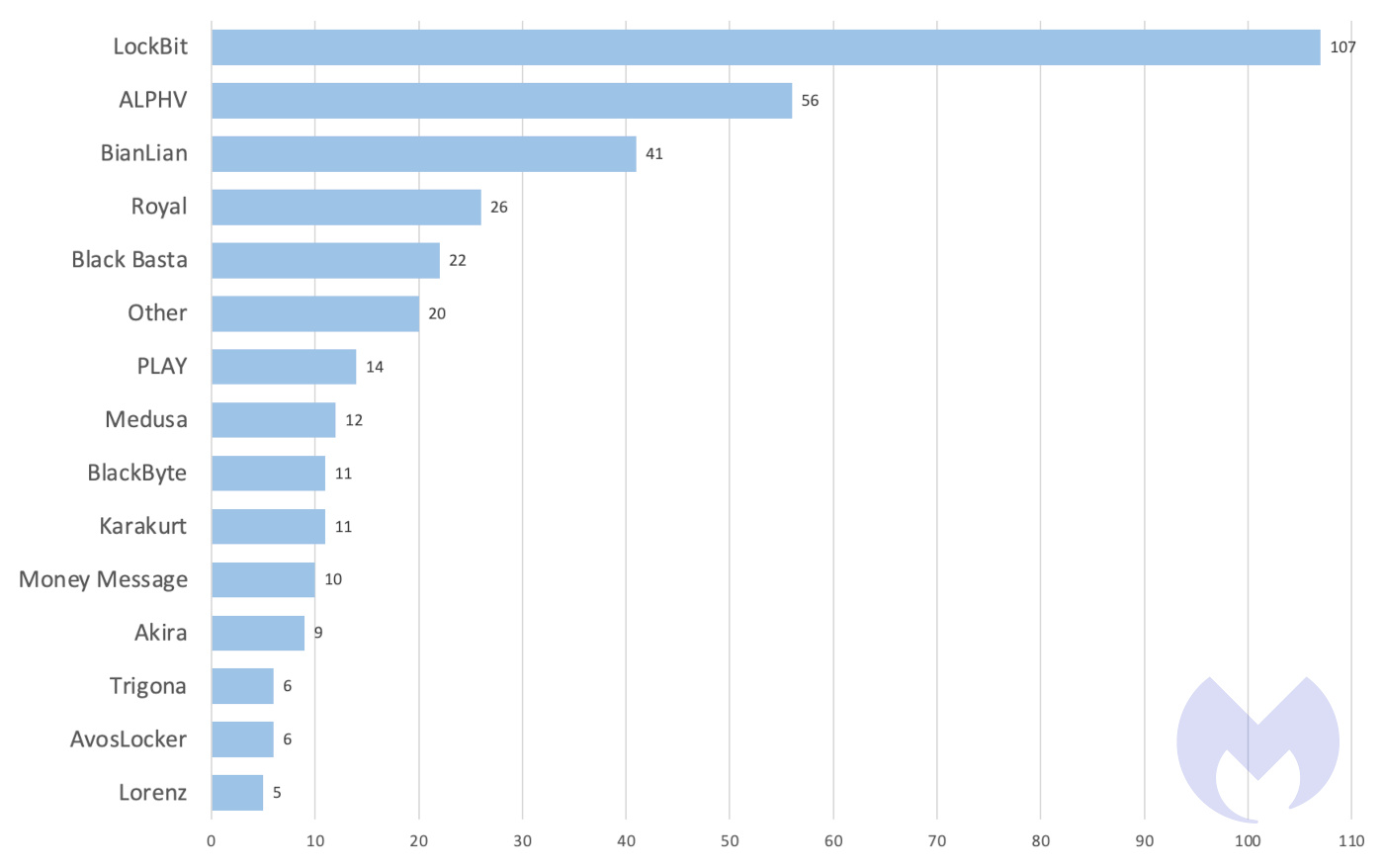
Known ransomware attacks by gang, April 2023
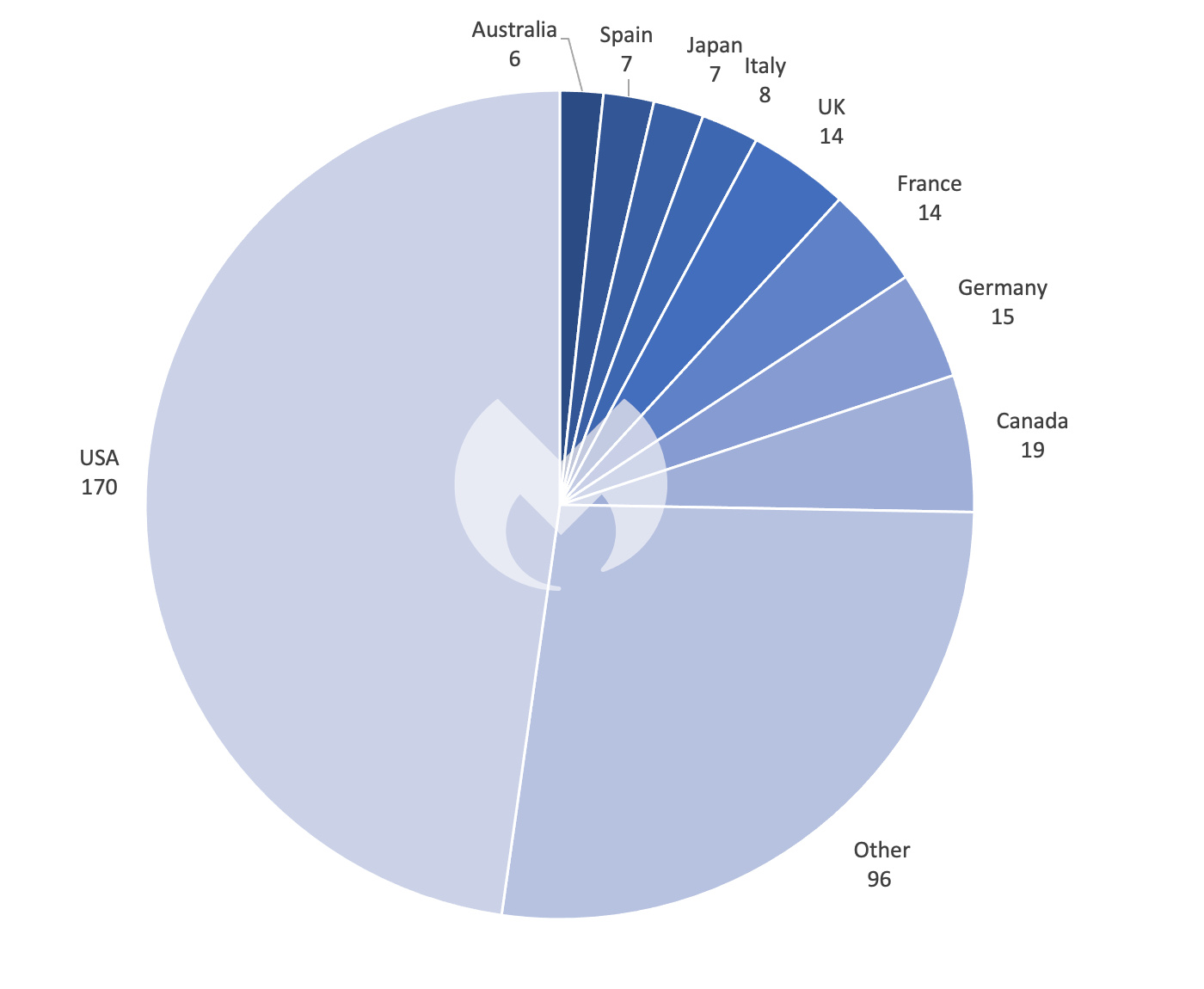
Known ransomware attacks by country, April 2023
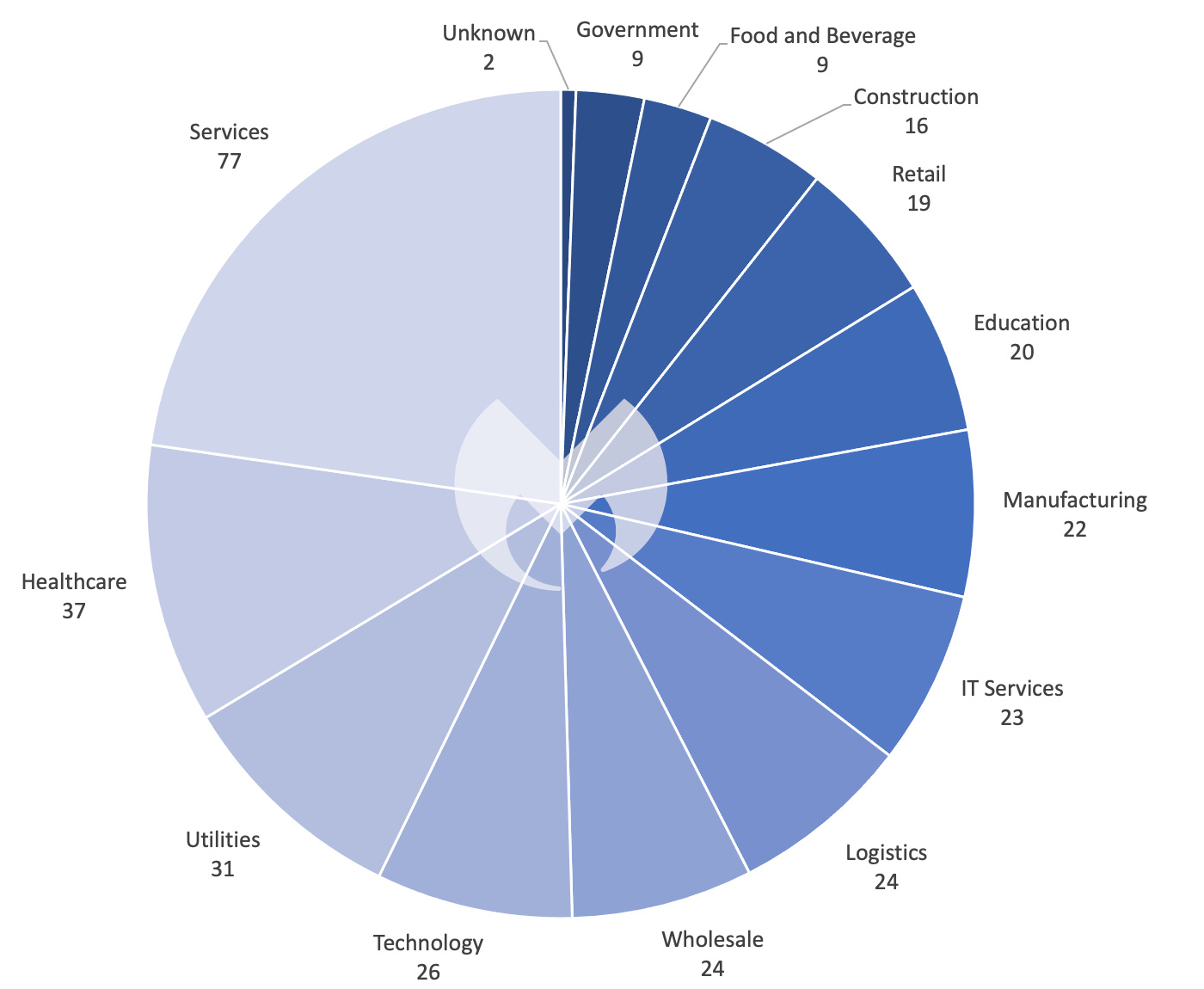
Known ransomware attacks by industry sector, April 2023
Cl0p ransomware, which gained prominence in March by exploiting a zero-day vulnerability in GoAnywhere MFT, went comparatively silent with just four attacks in April. Nevertheless, the gang was seen last month exploiting vulnerabilities in PaperCut servers to steal corporate data.
PaperCut is a popular printing management software which was targeted by both Cl0p and LockBit in April using two gnarly vulnerabilities: one allowing remote code execution (CVE-2023-27350) and the other enabling information disclosure (CVE-2023-27351). Once gaining initial access, Cl0p members sneakily deploy the TrueBot malware and a Cobalt Strike beacon to creep through the network, grabbing data along the way.
Cl0p clearly has a history of exploiting platforms like Accellion FTA and GoAnywhere MFT, and now they’ve set their sights on PaperCut. So, if you’re using PaperCut MF or NG, upgrade pronto and patch these two vulnerabilities!
Vice Society, notorious for targeting the education sector, has recently advanced their operations by adopting a sneaky PowerShell script for automated data theft. Discovered by Palo Alto Networks Unit 42, the new data exfiltration tool cleverly employs “living off the land” (LOTL) techniques to avoid detection. For instance, the script employs system-native cmdlets to search and exfiltrate data, minimizing its footprint and maintaining a low profile.
Separately, the Play ransomware group has whipped up two fancy .NET tools, Grixba and VSS Copying Tool, to make their cyberattacks more effective.
Grixba checks for antivirus programs, EDR suites, backup tools to help them plan the next steps of the attack. VSS Copying Tool, meanwhile, tiptoes around the Windows Volume Shadow Copy Service (VSS) to steal files from system snapshots and backup copies. Both tools were cooked up with the Costura .NET development tool for easy deployment on their victims’ systems.
As Vice Society, Play, and other ransomware groups increasingly adopt advanced LOTL methods and sophisticated tools like Grixba, the capacity to proactively identify both malicious tools and the malicious use of legitimate tools within a network will undoubtedly become the deciding factor in an organization’s defense strategy moving forward.
As for other trends, the USA still tops the charts as the most affected country, with the services industry getting the brunt of the attacks, as both have been the case all year. The education sector has its highest number of attackers (21) since January. Meanwhile, the healthcare sector saw a huge surge in attacks (37) in April, the highest it’s been all year.
New players
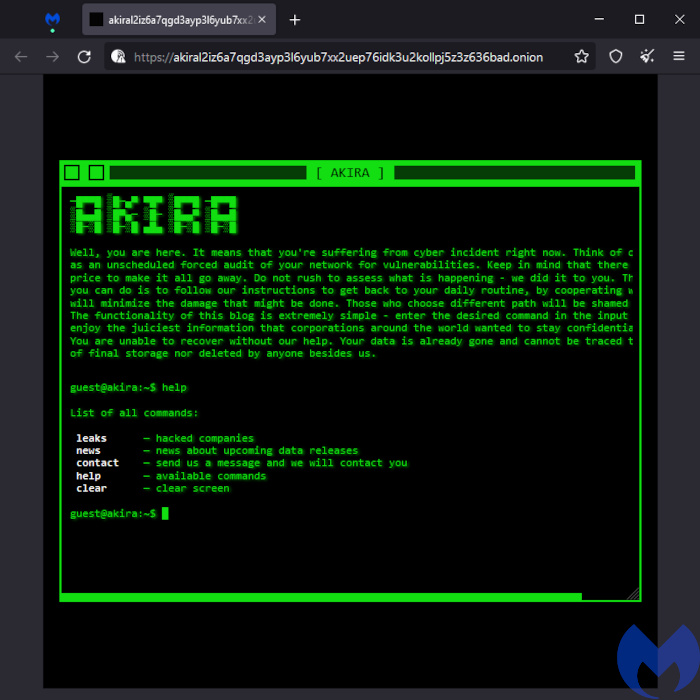
Akira
Akira is a fresh ransomware hitting enterprises globally since March 2023, having already published in April the data of nine companies across different sectors like education, finance, and manufacturing. When executed, the ransomware deletes Windows Shadow Volume Copies, encrypts files with specific extensions, and appends the .akira extension to the encrypted files.
Like most ransomware gangs these days, the Akira gang steals corporate data before encrypting files for the purposes of double-extortion. So far, the leaked info published on their leak site—which looks retro and lets you navigate with typed commands—ranges from 5.9 GB to a whopping 259 GB.
Akira demands ransoms from $200,000 to millions of dollars, and it seems they are willing to lower ransom demands for companies that only want to prevent the leaking of stolen data without needing a decryptor.
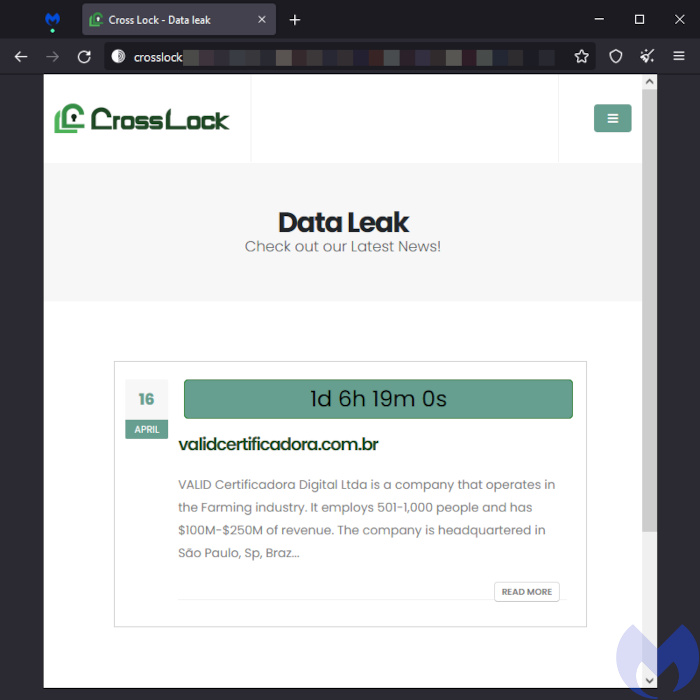
CrossLock
CrossLock is a new ransomware strain using the Go programming language, which makes it more difficult to reverse engineer and boosts its compatibility across platforms.
The ransomware employs tactics to avoid analysis, such as looking for the WINE environment (to determine if their ransomware is being executed within an analysis or sandbox environment) and tweaking Event Tracing for Windows (ETW) functions (to disrupt the flow of information that security tools and analysts rely on to identify suspicious behavior).
In April, the CrossLock Ransomware Group said they targeted Valid Certificadora, a Brazilian IT & ITES company.
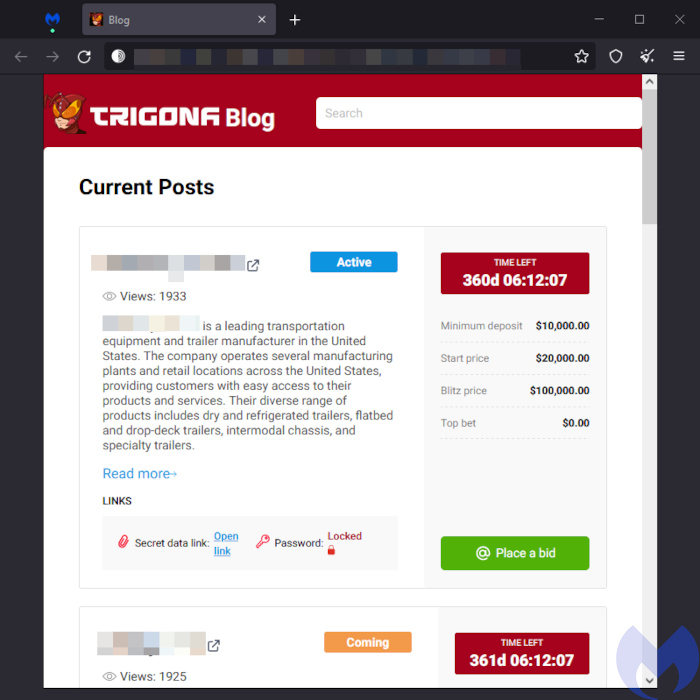
Trigona
Trigona ransomware emerged in October 2022 and has targeted various sectors worldwide, including six in April. Operators use tools like NetScan, Splashtop, and Mimikatz to gain access, perform reconnaissance, and gather sensitive information from target systems. They also employ batch scripts to create new user accounts, disable security features, and cover their tracks.
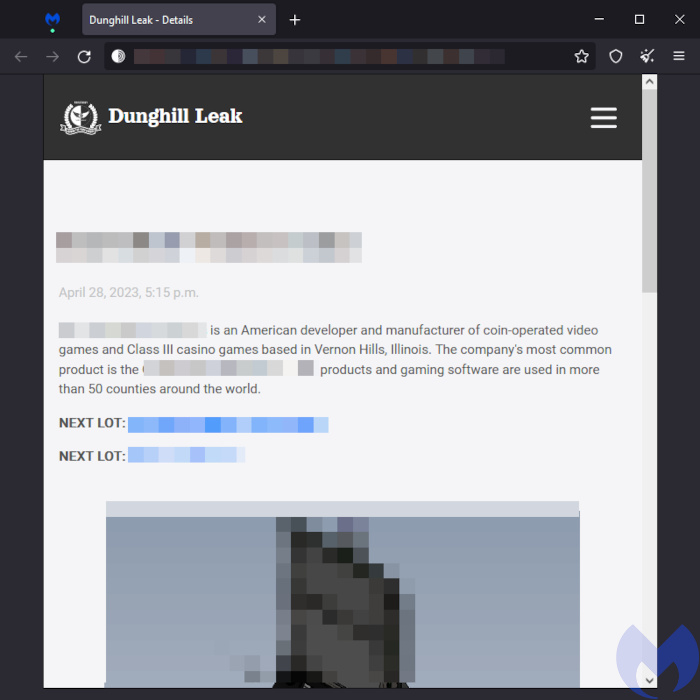
Dunghill Leak
Dunghill Leak is a new ransomware that evolved from the Dark Angels ransomware, which itself came from Babuk ransomware. In April it published the data of two companies, including Incredible Technologies, an American developer and manufacturer of coin-operated video games. The Dunghill Leak gang claims they have access to 500 GB of the company’s data, including game files and tax payment reports. Researchers think Dunghill Leak is just a rebranded Dark Angels.
Money Message
Money Message is a new ransomware which targets both Windows and Linux systems. In April, criminals used Money Message to hit at least 10 victims, mostly in the US and from various industries. The gang also targeted some big-time companies worth billions of dollars, such as Taiwanese PC parts maker MSI (Micro-Star International).
Money Message uses advanced encryption techniques and leaves a ransom note called “money_message.log.”
Our Ransomware Emergency Kit contains the information you need to defend against ransomware-as-a-service (RaaS) gangs.
How to avoid ransomware
- Block common forms of entry. Create a plan for patching vulnerabilities in internet-facing systems quickly; and disable or harden remote access like RDP and VPNs.
- Prevent intrusions. Stop threats early before they can even infiltrate or infect your endpoints. Use endpoint security software that can prevent exploits and malware used to deliver ransomware.
- Detect intrusions. Make it harder for intruders to operate inside your organization by segmenting networks and assigning access rights prudently. Use EDR or MDR to detect unusual activity before an attack occurs.
- Stop malicious encryption. Deploy Endpoint Detection and Response software like Malwarebytes EDR that uses multiple different detection techniques to identify ransomware, and ransomware rollback to restore damaged system files.
- Create offsite, offline backups. Keep backups offsite and offline, beyond the reach of attackers. Test them regularly to make sure you can restore essential business functions swiftly.
- Don’t get attacked twice. Once you’ve isolated the outbreak and stopped the first attack, you must remove every trace of the attackers, their malware, their tools, and their methods of entry, to avoid being attacked again.
Malwarebytes removes all remnants of ransomware and prevents you from getting reinfected. Want to learn more about how we can help protect your business? Get a free trial below.










