Results for 'Nuclear'
Nuclear
Short bio Exploit kits are efficient and effective tools for cybercriminals to distribute malware. Exploit kits include exploits for multiple vulnerabilities...
Russia’s APT28 uses fear of nuclear war to spread Follina docs in Ukraine
June 13, 2022 - This blog post was authored by Hossein Jazi and Roberto Santos. In a recent campaign, APT28, an advanced persistent threat actor...
WordPress Compromise Campaign: From Nuclear EK To Angler EK
February 17, 2016 - A couple of weeks ago we blogged about an attack against WordPress sites initially discovered by Denis Sinegubko over at Sucuri....
Gate To Nuclear EK Uses Fake CloudFlare DDoS Check
February 8, 2016 - There has been a lot of talk about Nuclear EK recently, following Sucuri’s discovery about a large number of WordPress sites...
Nuclear EK Leveraged In Large WordPress Compromise Campaign
February 3, 2016 - Security company Sucuri recently noted a spike in WordPress infections, with a large number of sites getting injected with the same malicious scripts....
Spike in Malvertising Attacks Via Nuclear EK Pushes Ransomware
December 11, 2015 - We’ve been monitoring a malvertising campaign very closely as it really soared during the past week. The actors involved seem to be...
A history lesson brought to you by the Nuclear exploit kit
April 10, 2015 - During our malware investigations, we are often learning about new techniques or ways the bad guys try to bypass us. But sometimes,...
Nuclear EK leverages recently patched Flash vulnerability
March 19, 2015 - Back in October 2014, we wrote an article about a particular malware campaign we nicknamed ‘EITest’. The actors behind it were...
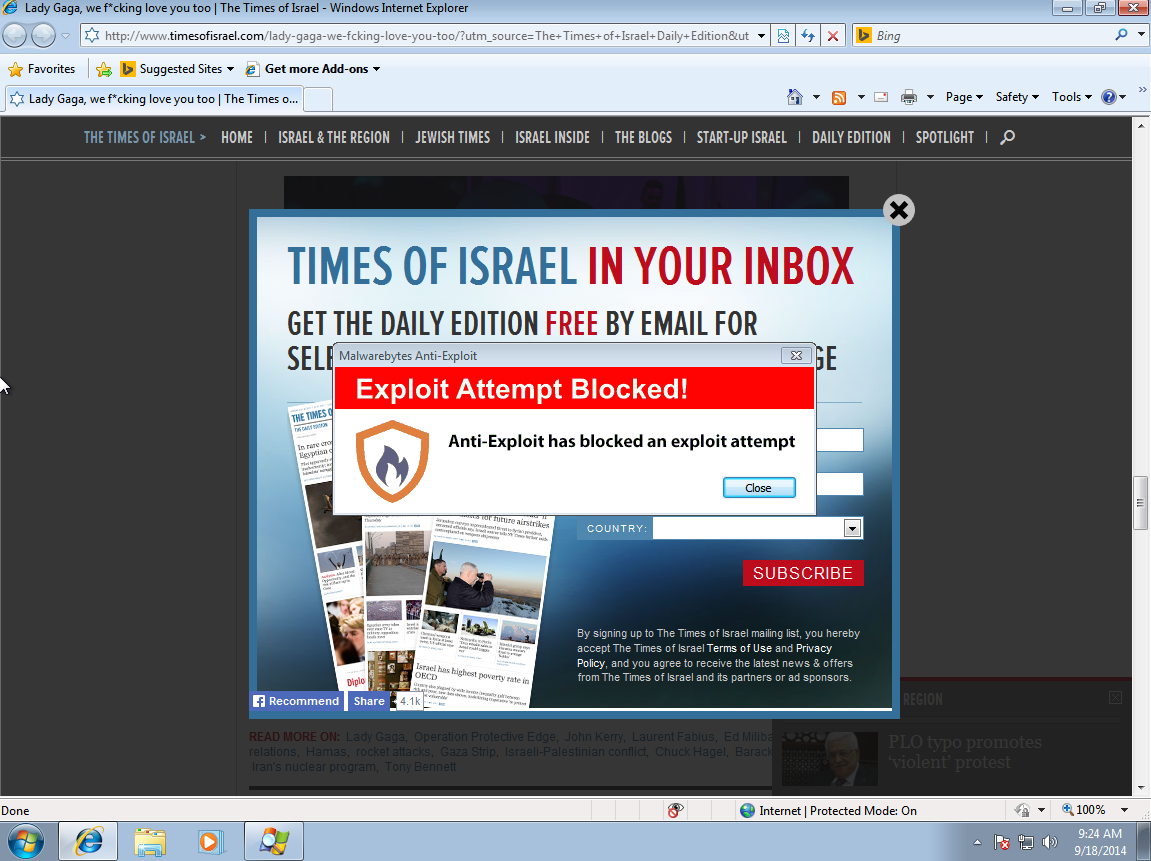
Malvertising hits ‘The Times of Israel’ and ‘The Jerusalem Post’, redirects to Nuclear Exploit Kit
September 18, 2014 - The Times of Israel is a popular online newspaper available in several different languages with a majority of readers from the...
SocialBlade.com compromised, starts redirection chain to Nuclear Pack exploit kit
July 29, 2014 - Update (07/29/2014): Following our notification, the developers in charge of SocialBlade.com have investigated and identified the source of the compromise. The...