ThreatDown Portfolio
Our solutions combine award-winning technology and the skilled services needed to simplify protection from today's most evasive threats.
Bundles
Core
Next-gen AV and threat surface reduction.
Annual pricing
/ per endpoint
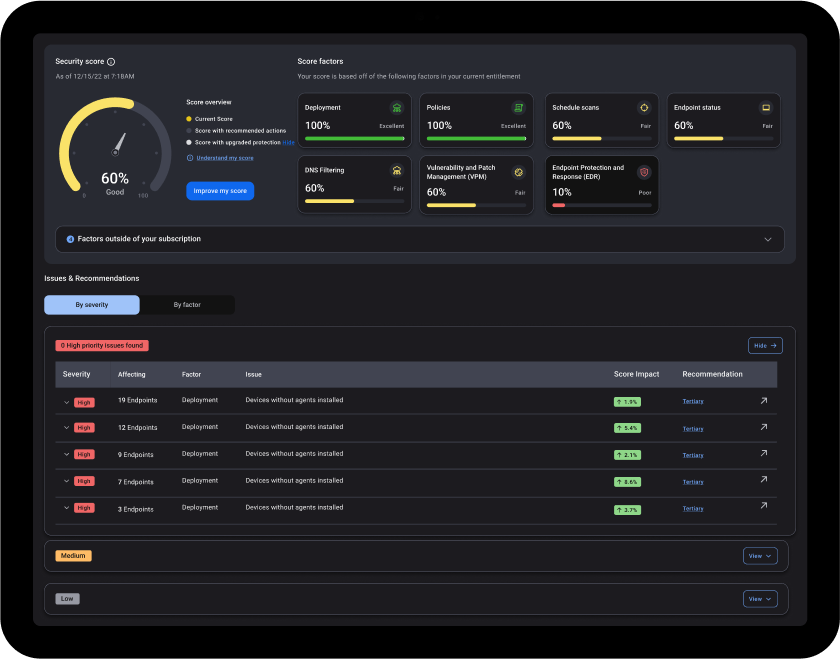
What you get:
-
Incident response
-
Next-gen AV
-
Device control
-
Application Block
-
Vulnerability Assessment
Optional add-ons:
-
Core for Servers /
-
Mobile Security / $10
Advanced
Everything in Core plus expanded threat surface protection.
Annual pricing
/ per endpoint
What you get:
-
Incident response
-
Next-gen AV
-
Device control
-
Application Block
-
Vulnerability Assessment
-
Ransomware Rollback
-
Endpoint Detection & Response
-
Patch Management
-
Managed Threat Hunting
Optional add-ons:
-
Advanced for Servers /
-
Mobile Security / $10
Elite
Everything in Advanced plus fully managed detection and response.
Annual pricing
/ per endpoint
What you get:
-
Incident response
-
Next-gen AV
-
Device control
-
Application Block
-
Vulnerability Assessment
-
Ransomware Rollback
-
Endpoint Detection & Response
-
Patch Management
-
Managed Detection & Response (includes Threat Hunting)
Optional add-ons:
-
Elite for Servers /
-
Mobile Security / $10
Ultimate
Everything in Elite plus protection against malicious websites.
Annual pricing
/ per endpoint
What you get:
-
Incident response
-
Next-gen AV
-
Device control
-
Application Block
-
Vulnerability Assessment
-
Ransomware Rollback
-
Endpoint Detection & Response
-
Patch Management
-
Managed Detection & Response (includes Threat Hunting)
-
DNS (Web Content) Filtering
Optional add-ons:
-
Ultimate for Servers /
-
Mobile Security / $10
Services
Products
Get started today
Let us take care of your endpoint security. Deploy the solution that delivers superior defense, easiest to use management, and the best value for your security investment.
Get a quote