Endpoint Protection
Recognized for award-winning protection, ThreatDown Endpoint Protection prevents threats from getting into your environment with next-gen antivirus
Companies face growing cybersecurity challenges
Attacks are evolving
71%
Companies impacted by ransomware last year1
Agent sprawl = complexity
55
Average number of cybersecurity tools deployed at a company2
Lack of budget and resources
30%
security alerts ignored3
1 2023 Malwarebytes State of Malware Report. 2 Anomali’s Cybersecurity Insights Report 2021. 3 IDC May 2021
ThreatDown makes it easy to protect endpoints
Neutralize threats to your organization’s workstations, servers and more, all without adding complexity

Award-Winning
Next-Gen Antivirus Protection
Consistent top ranking of Level 1 certification in MRG Effitas 360 degree testing and #1 Endpoint Security Suite by G2.
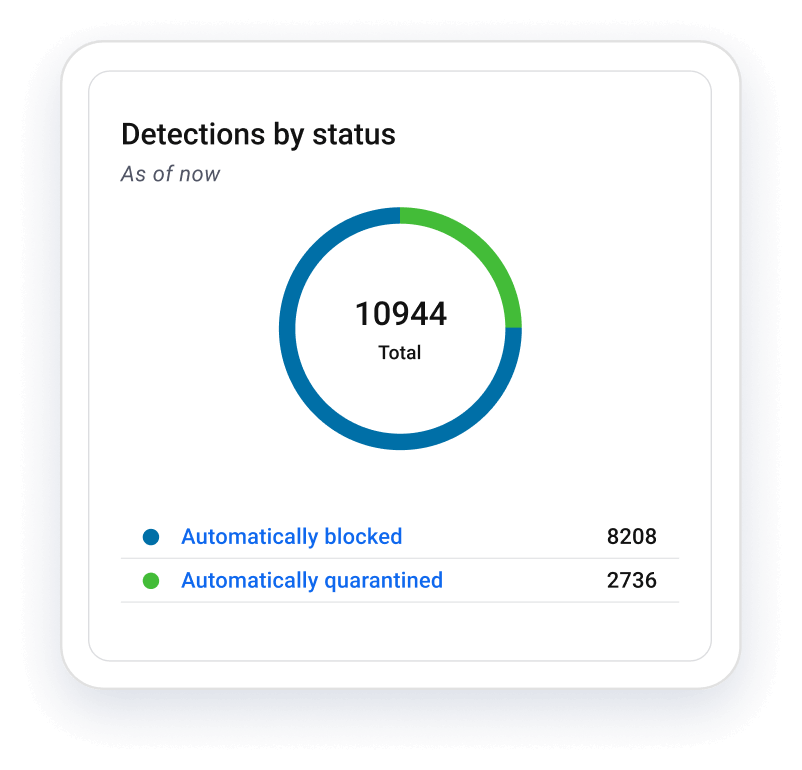
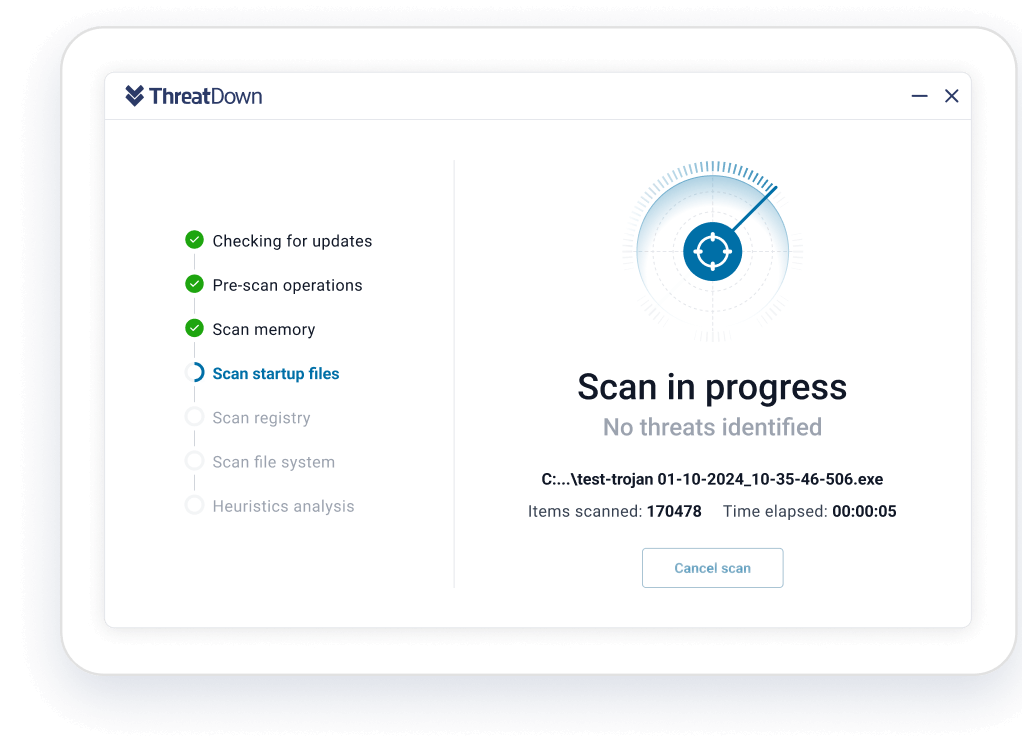
AI-Powered Endpoint Protection
Multiple integrated prevention technologies, built on AI, provide defense-in-depth to stop threats before they get into your environment.
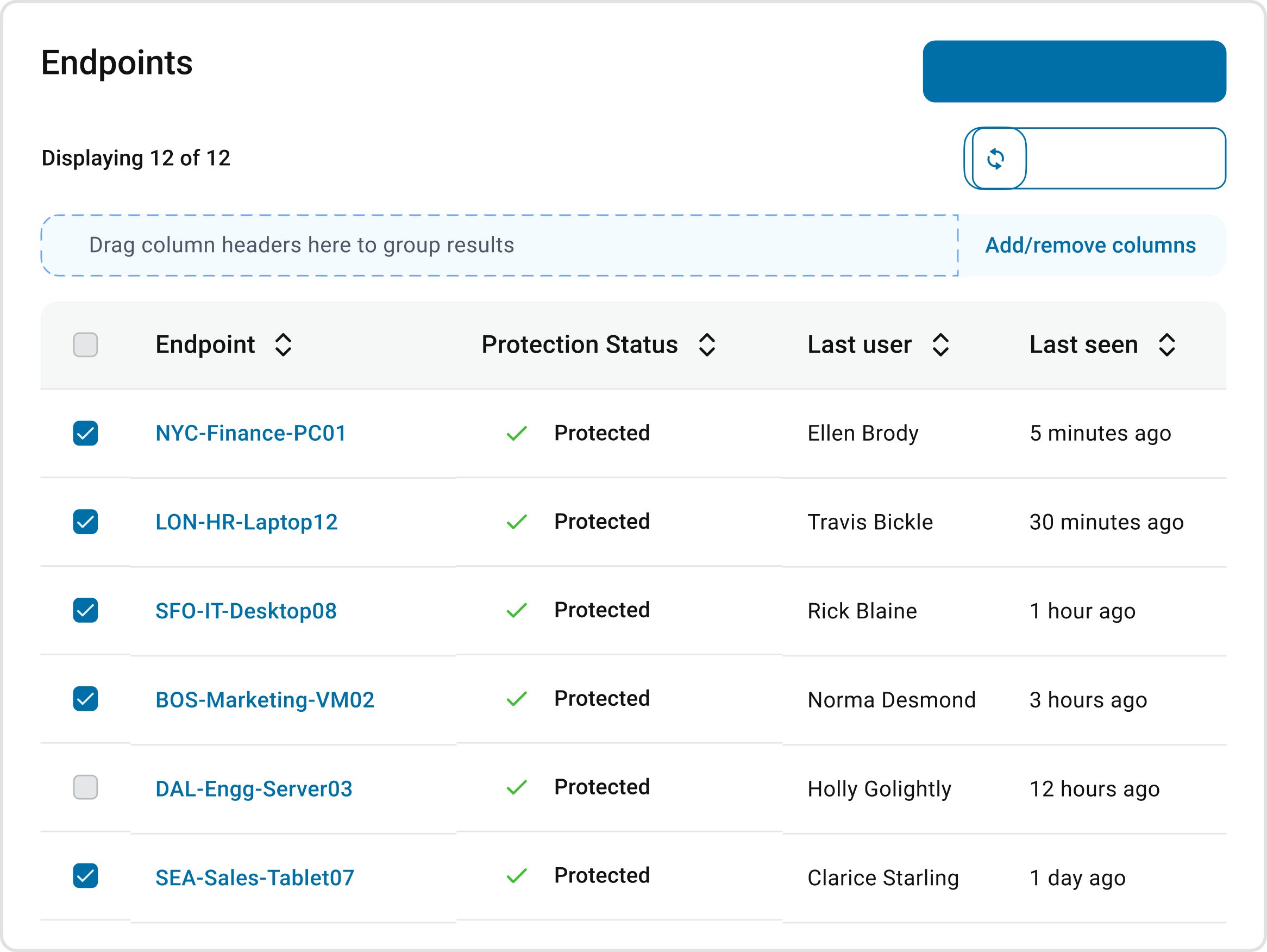
Simplified Management
View threats, take action and get robust reporting, all from a straightforward, easy to use dashboard.
Single, Lightweight Agent
To simplify security and reduce costs, Endpoint Protection deploys easily in minutes using the same agent and cloud-based console that powers all ThreatDown endpoint security technologies.

“ThreatDown EDR’s ransomware rollback and automated malware remediation capabilities are a great sales point. If we have a detection, we can go into that machine and hit the rollback, and we basically go back in time to before there was an infection.”
Logan Evans, Director of Information Systems
Coffee County School District
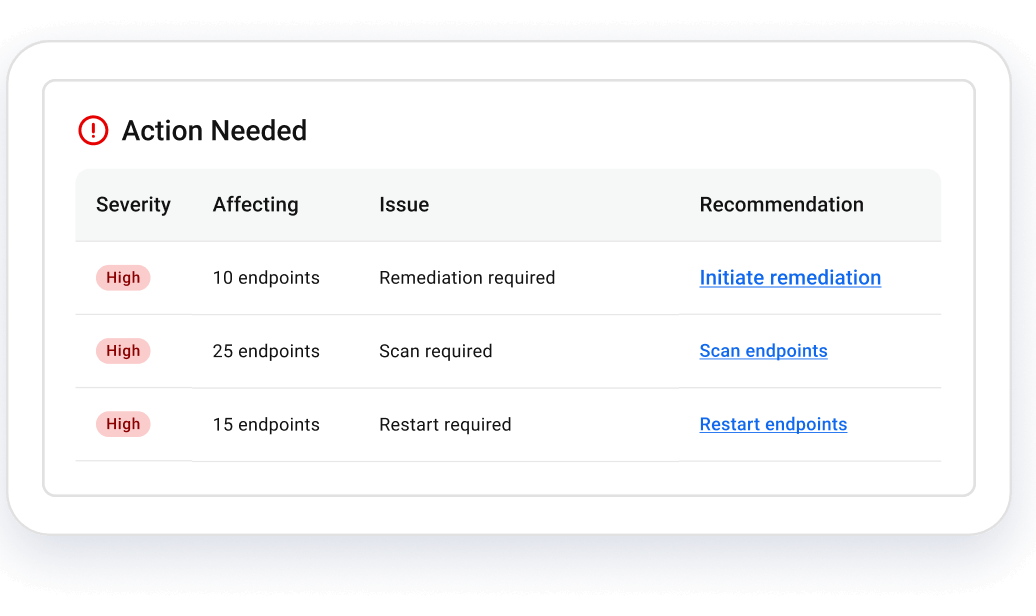
Bring your threat levels down with Security Advisor
Visualize and optimize your security posture in just minutes.
- At-a-glance security score
- Issue prioritization
- Instant advice & action
EP’s Next-gen AV technology is included in all ThreatDown Bundles
Core
Next-gen AV and threat surface reduction.
Annual pricing
/ per endpoint
What you get:
-
Incident response
-
Next-gen AV
-
Device control
-
Application Block
-
Vulnerability Assessment
Optional add-ons:
-
Core for Servers /
-
Mobile Security / $10
Advanced
Everything in Core plus expanded threat surface protection.
Annual pricing
/ per endpoint
What you get:
-
Incident response
-
Next-gen AV
-
Device control
-
Application Block
-
Vulnerability Assessment
-
Ransomware Rollback
-
Endpoint Detection & Response
-
Patch Management
-
Managed Threat Hunting
Optional add-ons:
-
Advanced for Servers /
-
Mobile Security / $10
Elite
Everything in Advanced plus fully managed detection and response.
Annual pricing
/ per endpoint
What you get:
-
Incident response
-
Next-gen AV
-
Device control
-
Application Block
-
Vulnerability Assessment
-
Ransomware Rollback
-
Endpoint Detection & Response
-
Patch Management
-
Managed Detection & Response (includes Threat Hunting)
Optional add-ons:
-
Elite for Servers /
-
Mobile Security / $10
Ultimate
Everything in Elite plus protection against malicious websites.
Annual pricing
/ per endpoint
What you get:
-
Incident response
-
Next-gen AV
-
Device control
-
Application Block
-
Vulnerability Assessment
-
Ransomware Rollback
-
Endpoint Detection & Response
-
Patch Management
-
Managed Detection & Response (includes Threat Hunting)
-
DNS (Web Content) Filtering
Optional add-ons:
-
Ultimate for Servers /
-
Mobile Security / $10


