This morning I received an email claiming to be from KPN – a Dutch provider of internet, television, and phone – claiming an amount so high that it should raise questions or at least your blood pressure. We can safely assume that it is intended to peak the receivers curiosity enough to get them to click one of the links in the mail.
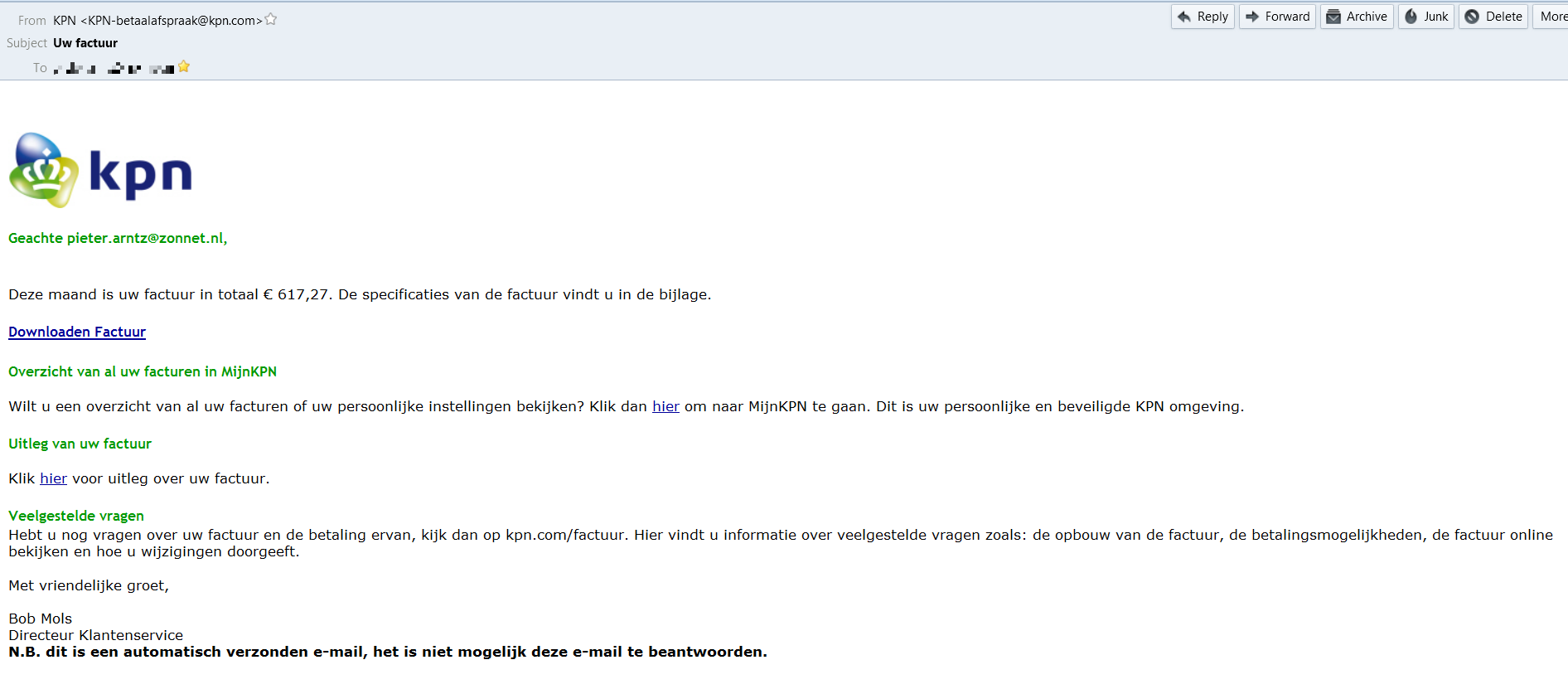
Translation of the relevant lines
Your invoice this month totals € 617,27 (roughly US$ 700). Download the invoice here. (link) Would you like an overview of your invoices or your personal settings? Click here (link) to go to MyKPN. This is your personal and secure environment. Explanation of your invoice Click here (link) for an explanation of your invoice.
And so forth. The spam template is an exact replica of mail KPN sends out to clients. But the “From” address is “KPN-betaalafspraak[AT]kpn[DOT]com” where real ones should come from : “Internetdiensten-noreply@kpn.com“.
The three links all point to the same web address www2[DOT]uebler-gmbh[DOT]de, which is a site that belongs to a German job coaching firm. We informed them of the fact that their site is being used for this, but haven’t heard back yet.
We have also informed the Dutch provider KPN through the normal channels, which probably means we will only get an automated response.
Clicking the links in the mail will result in the download of a zip file containing a file called “Factuur 00055783-63845853.PDF.exe” showing up with a PDF icon. This is a well-known trick to deceive users that have file extensions set to “Hide extensions for known file types” into thinking that they are about to open a (harmless) document.

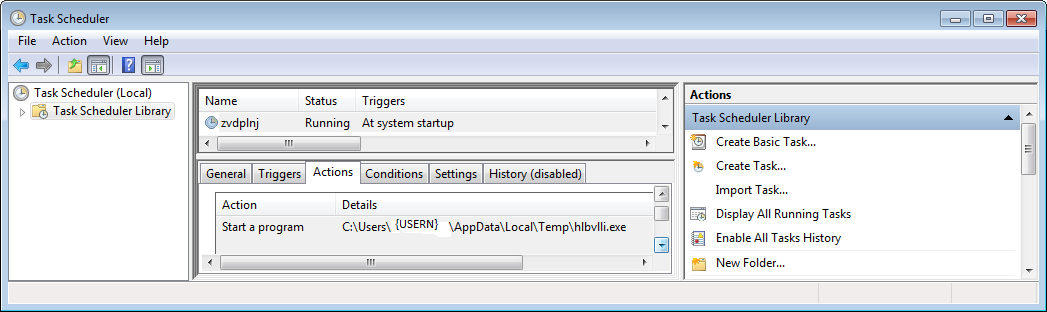
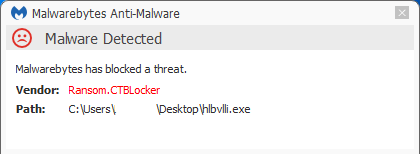
Double-clicking the file will result in the start of the CTB locker ransomware. It creates a copy of the executable with a different name (here hlbvlli.exe) in the %Temp% folder and the creation of a Scheduled Task that will trigger that copied file every time the compromised system boots.
“The encrypted files have an extra extension that is 6 or 7 characters long consisting of random alphabets (in this case, it’s “xanhsmj”). After encryption, users are presented with the below ransom note:
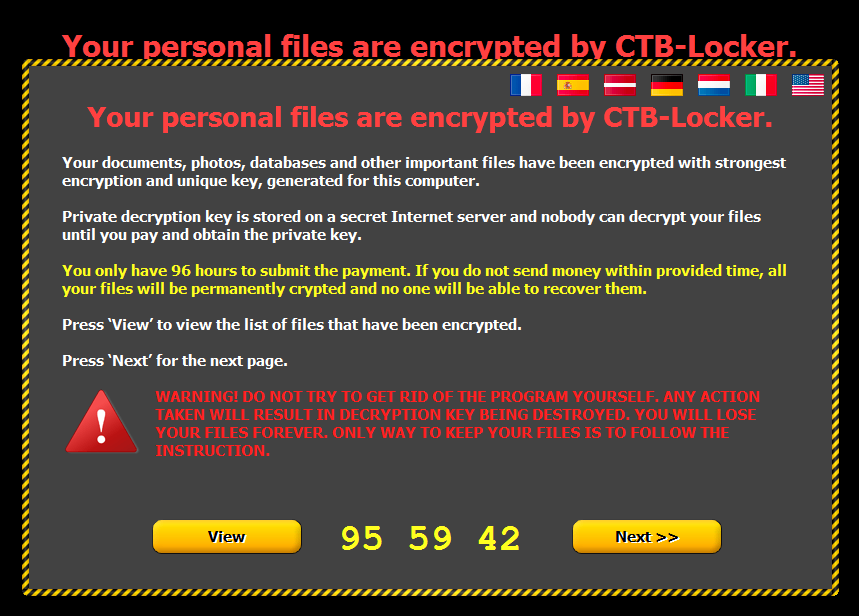
We can’t warn you enough about these tricks as ransomware is becoming a bigger and more prevalent threat every day.
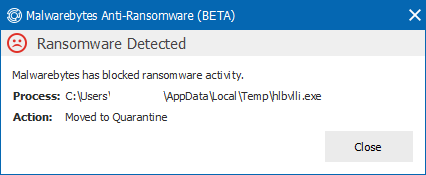
For those interested we do have an Anti-Ransomware solution available for beta testing. It was able to stop this one from encrypting my documents.
Summary
We showed you a step by step infection process from spam mail to the files being held ransom.
Extra file information
Md5 “Factuur 00055783-63845853.PDF.exe” f67a2c2ec4427fba6cccf14c691b5d29
The files are detected by Malwarebytes Anti-Malware as Ransom.CTBLocker.
[Update] KPN notified me that sending an automated response does not mean that they don’t take our phishing notifications seriously. It is the sheer volume that does not allow them to answer every report personally.
Pieter Arntz
![[Updated] KPN spam results in CTB-Locker infection](https://www.malwarebytes.com/wp-content/uploads/sites/2/2016/05/kpn.jpg?w=768)










