It’s difficult to say if the below defacement (spotted in the wild by the awesome Techhelplist) was intentionally targeted, or a case of “an insecure site just happened to be there”, but a URL suggesting some form of Yahoo verification met with disaster in the last couple of days.
verified-yahoo(dot)com
Above is the anonymously registered domain in question, and instead of the fake login you’d have expected to see, it was actually sporting more of a CSI style “Deal with it” vibe, complete with what sounded like a K-pop tune playing in the background.
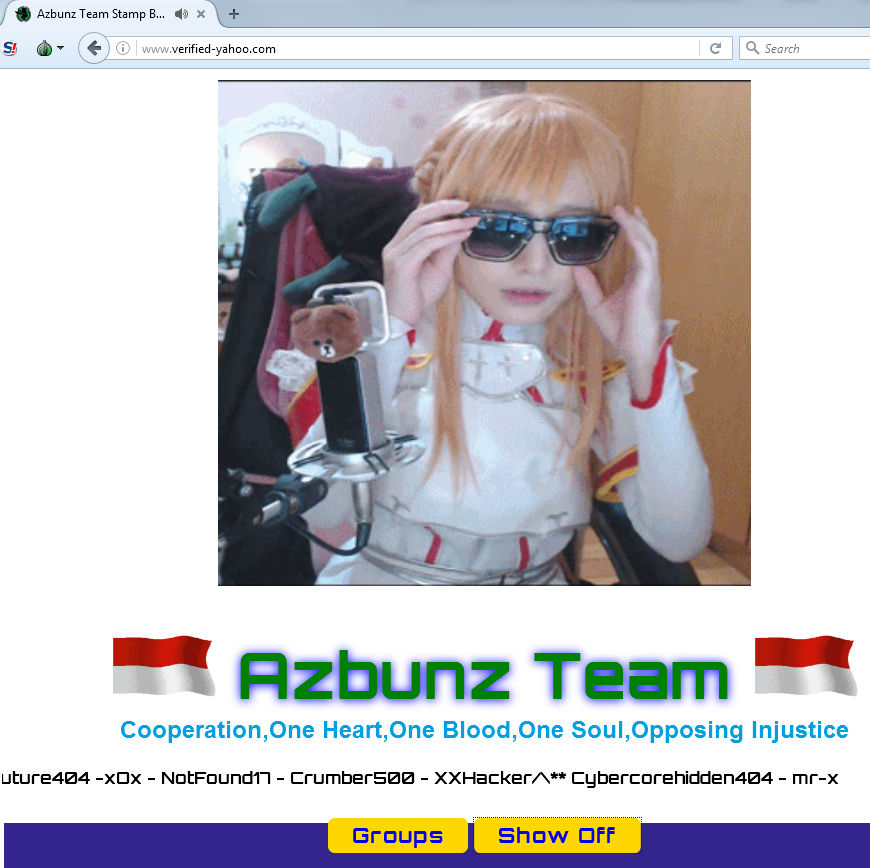
Accurate assessment: (•_•) ( •_•)>⌐■-■ (⌐■_■)
Phishing URL compromise is surprisingly common, as many phish pages are fully expected to have a short shelf life. Either the webhost will notice quickly, or someone will report it – so that whole “lock it down” side of things tends to fall by the wayside. No point defending your little phishing turf when there’s another twenty URLs sitting in a reserve stash should anything happen to it – easily guessed passwords and insecure setups are rife.
Of course, having a site taken down isn’t the only thing making life difficult for phishers. As you’ll see below, it’s often the least of their worries given the surprisingly plentiful ways people want to celebrate International Give a Phisher a Headache Day.
Common mishaps for phishers include the following:
1. The reverse heel turn
Understandably, lots of individuals become rather annoyed by phishing. Even the most malware obsessed forum lurker is probably endlessly annoyed by the steady dripfeed of phish spam in their mailbox every morning. Anybody wanting to take up phishing needs to understand that they’re likely going to sit in their little corner of the net surrounded by a plethora of people who don’t like them very much. Whether we’re talking disgruntled malware author or a random internet dweller about to turn into Detective Brian Mills, there’s a threat around every corner.
As an example of this: surprise! Your lovely scam page has been turned into a PSA on the dangers of phishing. This doesn’t happen often, but a quickfire burst of hilarity is guaranteed to take place when it does. The phisher probably doesn’t take it personally given they have other domains to hand, but it’s certainly an amusing end to a potentially harmful website.
2. Web-based Whalers
These are websites which would give off the appearance of a search engine, except it’s only searching for one thing – data dumps.
Many phish kits – and phishers, for that matter – are rather unimaginative where URLs are concerned. For example, their stolen credentials will typically be sent to
/phished
/logins
/passwords
/data
/credentials
and so on. Whaling tools will search a specific websites, checking for all the common credential dumping grounds before sending them back to our whaling opportunist. This is a fast, easy way for people to have someone else do all the hard work then swipe the (already stolen) credentials at the last minute. Whaling tools can be web-based or downloadable programs, and it’s likely that they’ve prompted both phishers and kits to mix things up where their URLs are concerned.
Speaking of whaling…
3. Fake Whaling tools
The act of stealing other phisher’s swiped credentials – is fairly common, but automating the process with a fake Whaling tool which actually just steals the phisher’s personal information due to it being malware? Ouch. Fake Whalers tend to be aimed at non-professional phishers – kids on forums, wannabes, ransom scammers looking to dip their toes in a particularly phishy tool, and so on. Quite the heavy price to pay for curiosity.
4. Hunt the phisher
Individuals and companies alike are always coming up with ways to track, catalogue, and drive offline phishers up to no good – with varying degrees of success [1], [2], [3].
5. Phish tool turnaround
This works in a similar way to [1], except in this case the phisher has their program turned against them instead of their fake login portal. Many phishers make programs which claim to offer up free Xbox points, Steam codes, PokemonGo coins, and pretty much anything else you’d ever have to otherwise pay for.
Some of these programs simply pop survey offers, while others may be entirely malicious and infect a computer. Where phishers are concerned, their tools will often ask for a login/password combination before beaming the data back to base – more often than not, via the phisher’s email login.
Can you see where this is going yet?
In cases where the login credentials for the email account are hardcoded into the tool and it isn’t encrypted, all someone has to do is open up the program in a tool which lets you explore text in a file, then hunt for the phisher’s email account details.
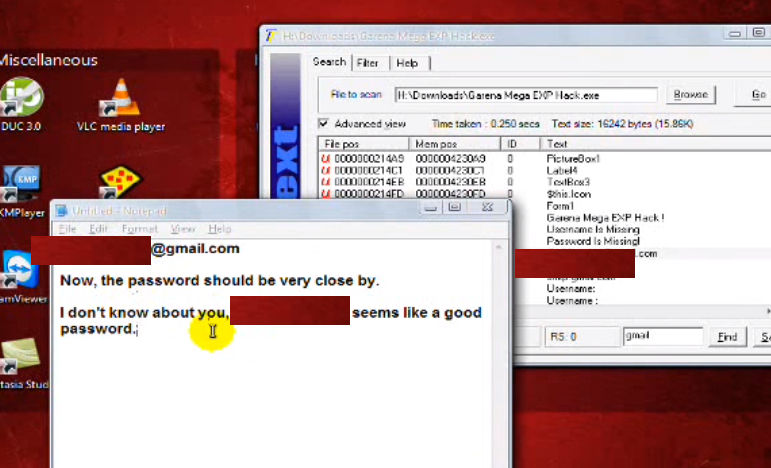
From there, they can attempt to log into their email address. At this point, all the stolen credentials are there for the taking, assuming the person doing the compromising is a rival phisher. This also means everything else in there is up for grabs too, assuming the phisher was foolish enough to use their data dump account for anything else (and if they reused passwords on other services, all your base are belong to us springs to mind).
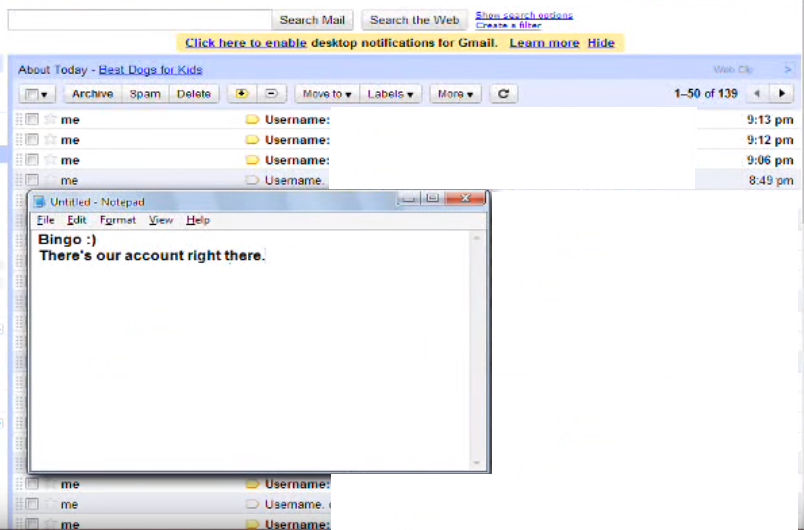
In the above example, the person doing the compromising hands their viewers information about the phisher’s social media accounts so they can be thoroughly mocked online. Not only will they lose their sweet phish stash, they’ll be called a noob by 12 year olds until the end of time.
Truly, there can be no more ignominious an end for a phisher than that. While phishing is nowhere near going out of business – much less phishers themselves being placed on an endangered species list – there’s certainly a lot of ways for them to take a fall. After looking at all of the above, if I was involved in phishing myself I’d probably be feeling a little bit nervous…
Christopher Boyd










