An email service called VFEmail was essentially put out of business after a hack intended to delete everything in (and out of) sight.
“Yes, @VFEmail is effectively gone. It will likely not return. I never thought anyone would care about my labor of love so much that they’d want to completely and thoroughly destroy it.”
This wasn’t “just” a simple webpage compromise, or some sort of database dump. In fact, it was something altogether quite worse. Put simply, the total annihilation of a service and most, if not all, of its infrastructure.
What happened?
Users of VFEmail woke to the following message on the service’s website:
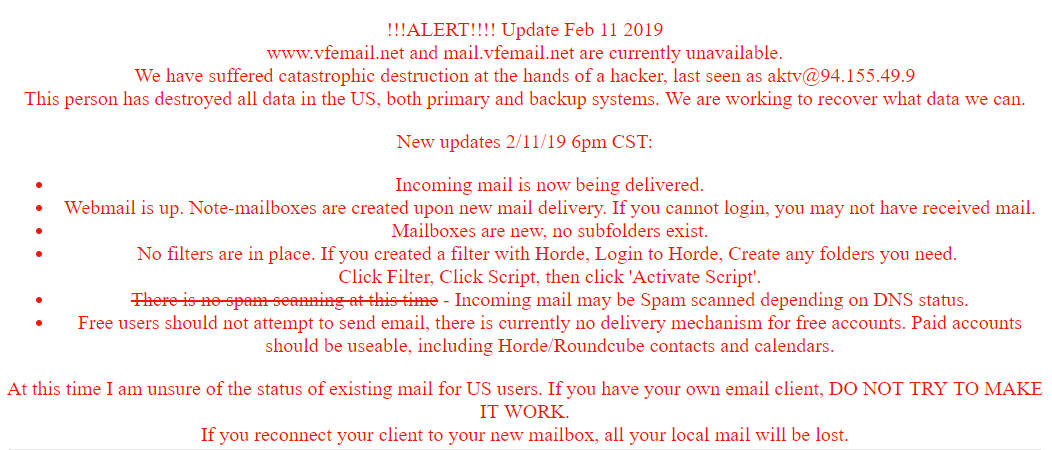
Click to enlarge
!!!ALERT!!!! Update Feb 11 2019vfemail(dot)net and mail(dot)vfemail(dot)net are currently unavailable.
We have suffered catastrophic destruction at the hands of a hacker, last seen as aktv[redacted]
This person has destroyed all data in the US, both primary and backup systems. We are working to recover what data we can.
New updates 2/11/19 6pm CST:
Incoming mail is now being delivered.
Webmail is up. Note-mailboxes are created upon new mail delivery. If you cannot login, you may not have received mail.
Mailboxes are new, no subfolders exist.
No filters are in place. If you created a filter with Horde, Login to Horde, Create any folders you need.
Click Filter, Click Script, then click ‘Activate Script’.
There is no spam scanning at this time – Incoming mail may be Spam scanned depending on DNS status.
Free users should not attempt to send email, there is currently no delivery mechanism for free accounts. Paid accounts should be useable, including Horde/Roundcube contacts and calendars.
At this time I am unsure of the status of existing mail for US users. If you have your own email client, DO NOT TRY TO MAKE IT WORK.
If you reconnect your client to your new mailbox, all your local mail will be lost.
Ouch.
Did they put word out on social media?
You bet they did, and the Tweets don’t make for pleasant reading:
https://twitter.com/VFEmail/status/1094987362931748867
https://twitter.com/VFEmail/status/1095021927972909056
It may sound a bit exciting to walk in on the scene of the crime, but I can assure you it’d only involve lots of “oh no” types of expression. If they’re already wiping your backups, the game is indeed over.
Did they recover?
Sadly things didn’t improve, and a few hours later the full damage report was available:
https://twitter.com/VFEmail/status/1095038701665746945
All data was encrypted at least, but said data basically vanished into thin air when it was scrubbed:
https://twitter.com/VFEmail/status/1095021577320755207
They also managed to destroy various VMs using different forms of authentication.
https://twitter.com/VFEmail/status/1095039092608385026
“Just attack and destroy”
Services and sites have been attacked severely in the past, some to the point of destruction. However, there’s almost always an overt reason given, or a ransom, or some other clue.
Here, it’s nothing but complete devastation and a service in existence since 2001 absolutely ruined in the bargain. There’s no indication as to how they got in, or if an important system had no multi-factor authentication. A number of commentators have suggested this flaw may have been a way in for the attacker.
Until detailed analysis is published, it’s hard to say why this happened. Did the owner of the service aggravate a talented hacker? Or could one of the service users have drawn attention from unwanted sources, and this is the end result? It’ll be fascinating to find out. But if you operate a similar service, you may wish to consider a decent offline backup system in the meantime.










