Ransom.binADS
Short bio
Ransom.binADS is Malwarebytes’ detection name for a ransomware family that is used in targeted attacks. This family is also known under the name WastedLocker.
Type and source of infection
Ransom.binADS is ransomware of the type that encrypts files and then asks for a ransom to decrypt them. Ransom.binADS is delivered onto a compromised system inside the network of the targeted organization. The initial infection is often done through websites that push fake updates.
Aftermath
Because of the targeted nature of this ransomware, it is advised to do a full network scan to find any backdoors or other tools that the threat actors may have left behind, and which may enable them to regain access to the network.
Protection
Malwarebytes detects WastedLocker ransomware as Ransom.BinADS.
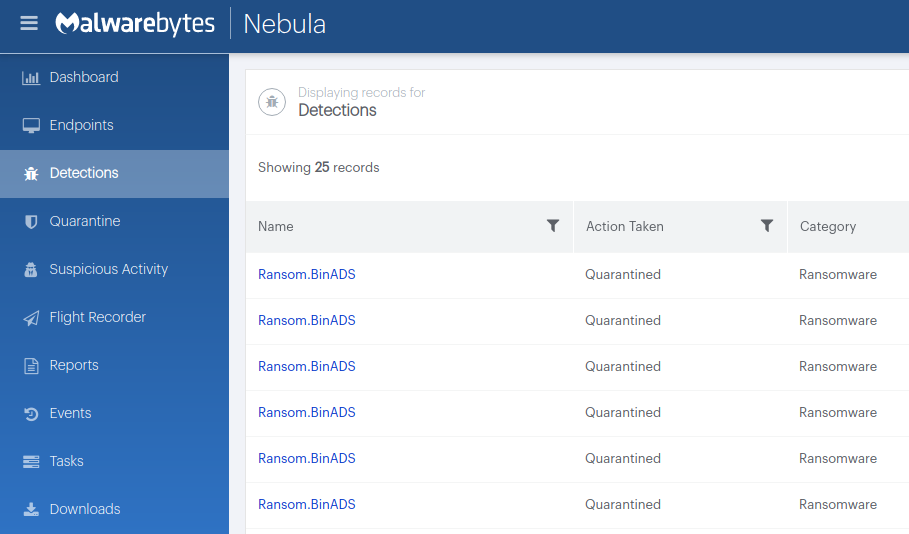
Business remediation
How to remove Ransom.binADS with the Malwarebytes Nebula console
You can use the Malwarebytes Anti-Malware Nebula console to scan endpoints.

Choose the Scan + Quarantine option. Afterwards you can check the Detections page to see which threats were found.
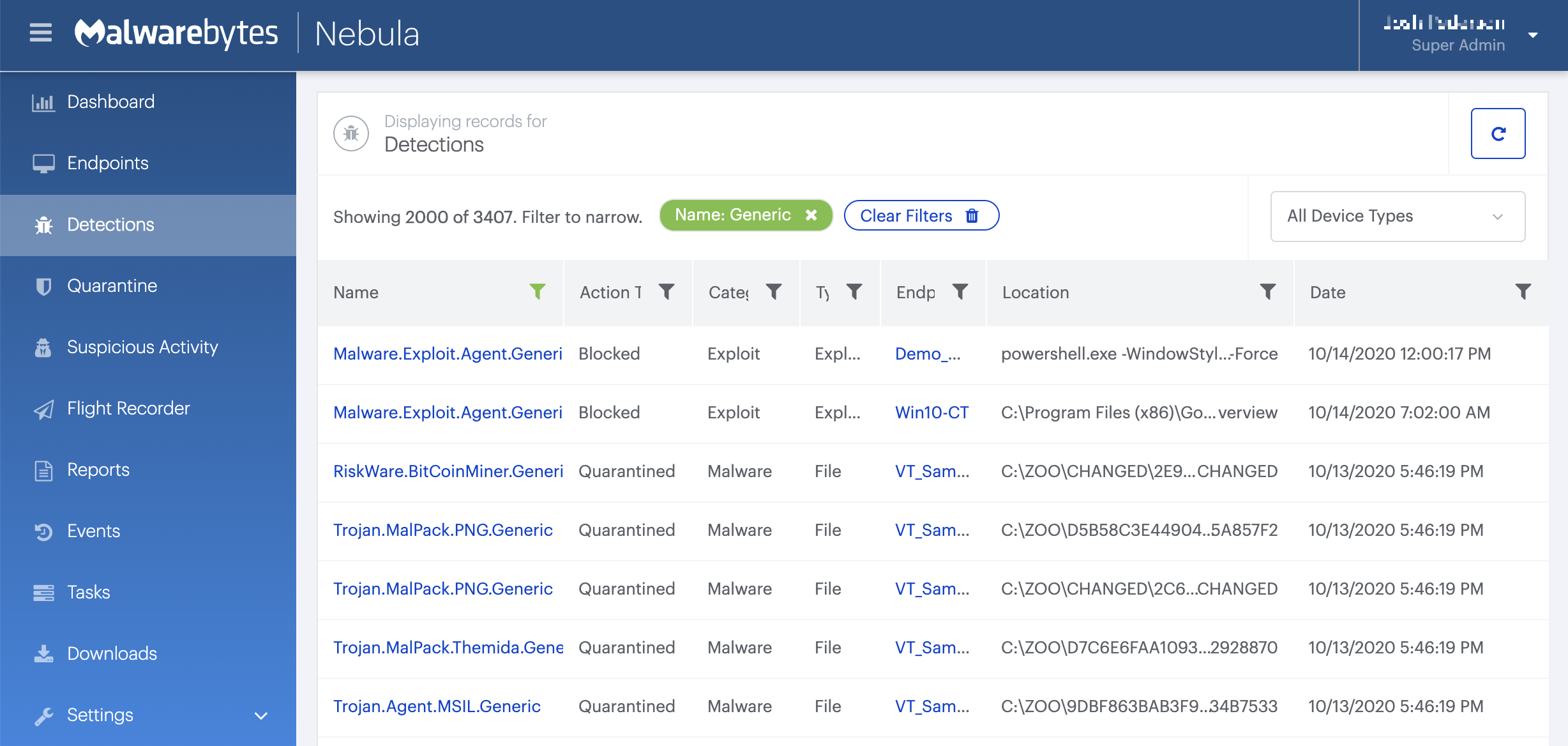
On the Quarantine page you can see which threats were quarantined and restore them if necessary.
All component/technology detections are passed to the remediation engine for complete removal from infected systems. This industry leading technology uses patented techniques in identifying all cohorts or associated files for a single threat and removes them all together to prevent malware from resuscitating itself. If you are using Malwarebytes Ransomware Rollback technology, it allows you to wind back the clock to negate the impact of ransomware by leveraging just-in-time backups.
IOCs
A ransom note will be created for each encrypted file with *wasted and *wasted_info filenames for encrypted files and the ransom notes.
Layout of the ransom note:
*ORGANIZATION_NAME* YOUR NETWORK IS ENCRYPTED NOW USE *EMAIL1* | *EMAIL2* TO GET THE PRICE FOR YOUR DATA DO NOT GIVE THIS EMAIL TO 3RD PARTIES DO NOT RENAME OR MOVE THE FILE THE FILE IS ENCRYPTED WITH THE FOLLOWING KEY: [begin_key]*[end_key] KEEP IT
On systems with a suitable file-system an Alternate Data Stream (ADS) is used as a means to run the ransomware processes. On others the ransomware binary is copied file to %windir%system32 and the attacker will take ownership of it (takeown.exe /F filepath) and reset the ACL permissions.





