Ransom.Conti
Short bio
Ransom.Conti is Malwarebytes’ detection name for a ransomware family operated by the Wizard Spider group.
Symptoms
Ransom.Conti deletes the local shadow copies via the Windows Volume Shadow Copy Service (VSS), preventing the victim from restoring data. After encryption of the files it shows the victim the ransom note.
Type and source of infection
Ransom.Conti is a ransomware that encrypts files on infected computers while disabling several backup programs. Ransom.Conti may be distributed using various methods. The most common one is by email, with a URL in the body that downloads a malicious document which in turn delivers the Bazar backdoor. This backdoor is used to further compromise the infected system.
Aftermath
Recovering from a ransomware attack can be a painstaking process even if the victim decides to pay it can take a considerable time to recover without adequate, recent, and organized backups, or a roll-back technology.
Not paying the Conti ransom can lead to exposure of exfiltrated data on the dark web.
Protection
Malwarebytes blocks Ransom.Conti
Home remediation
Malwarebytes can detect and remove Ransom.Conti without further user interaction.
- Please download Malwarebytes to your desktop.
- Double-click MBSetup.exe and follow the prompts to install the program.
- When your Malwarebytes for Windows installation completes, the program opens to the Welcome to Malwarebytes screen.
- Click on the Get started button.
- Click Scan to start a Threat Scan.
- Click Quarantine to remove the found threats.
- Reboot the system if prompted to complete the removal process.
Take note, however, that removing this ransomware does not decrypt your files. You can only get your files back from backups you made before the infection happened.
Business remediation

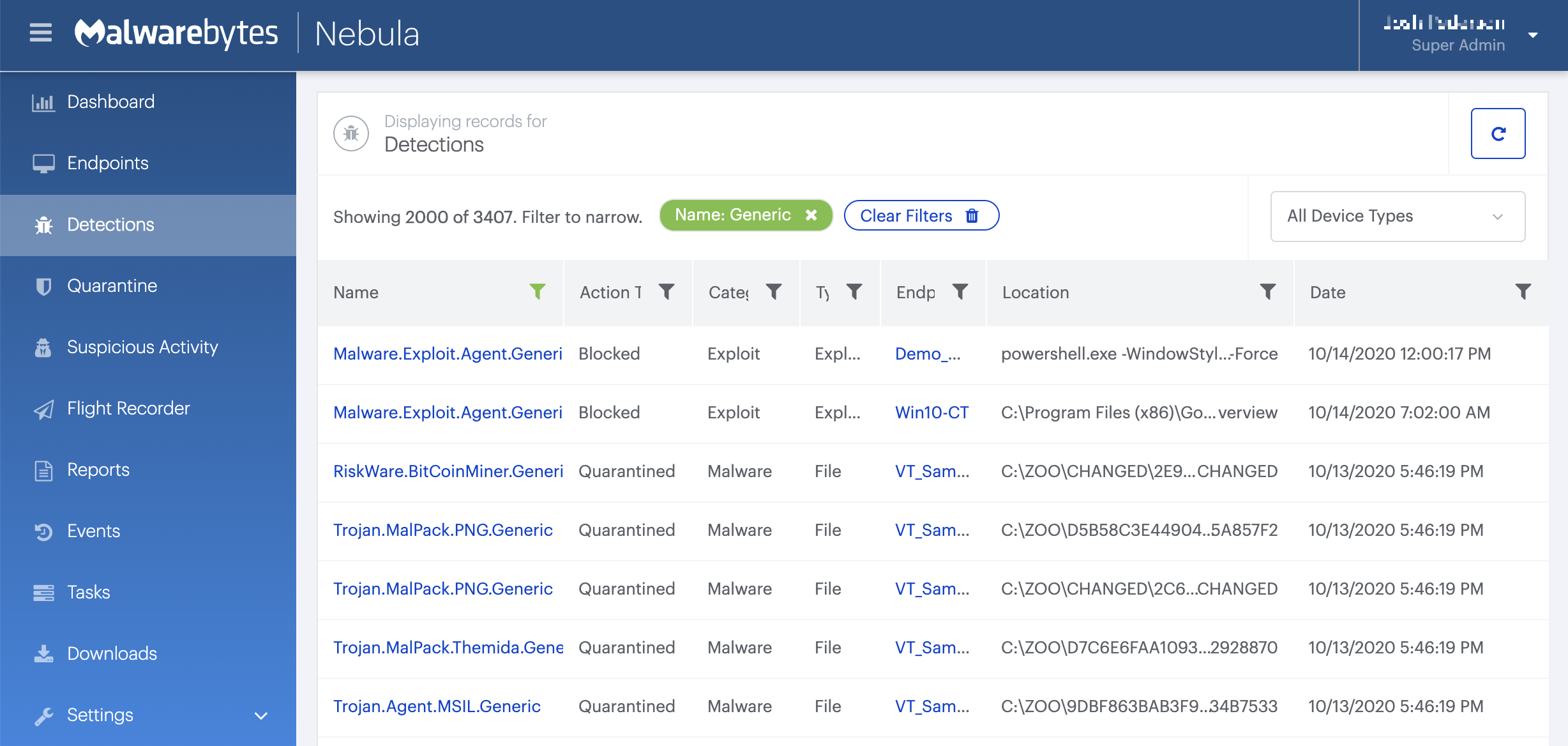
Nebula endpoint tasks menu
Choose the Scan + Quarantine option. Afterwards you can check the Detections page to see which threats were found.
On the Quarantine page you can see which threats were quarantined and restore them if necessary.
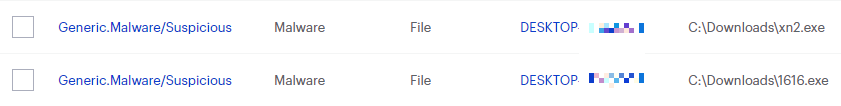
All component/technology detections are passed to the remediation engine for complete removal from infected systems. This industry leading technology uses patented techniques in identifying all cohorts or associated files for a single threat and removes them all together to prevent malware from resuscitating itself. If you are using Malwarebytes Ransomware Rollback technology, it allows you to wind back the clock to negate the impact of ransomware by leveraging just-in-time backups.
Traces/IOCs
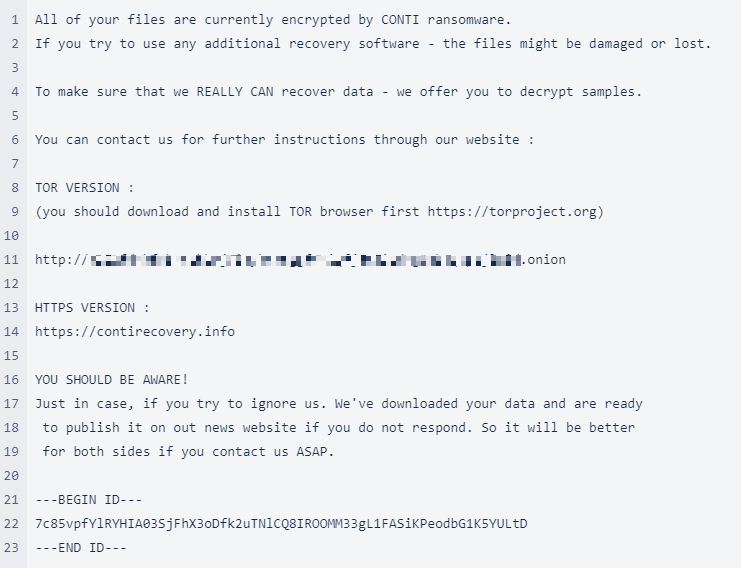
Ransom note:
- CONTI.txt
- R3ADM3.txt
- readme.txt
- CONTI_README.txt
Extension: .CONTI
New variants now append random 5 character file extensions (e.g. .RHMLM, .UAKXC, etc.)





