Ransom.Cryptomix
Short bio
Ransom.Cryptomix is a ransomware application that will encrypt files on a victim machine and demand payment to retrieve the information. The name Cryptomix is a combination of two separate ransomware families CryptXXX and CryptoWall and has been given this name due to similarities between the families. Ransom.Cryptomix was first spotted on March 2016 via malicious spam campaigns and exploit kits, such as Nuclear, Neutrino, and RIG.
Symptoms
Ransom.Cryptomix may run silently in the background during the encryption phase and not provide any indication of infection to the user. Ransom.Cryptomix may prevent the execution of Antivirus programs and other Microsoft Windows security features and may prevent system restoration as a means to solicit payment. Ransom.Cryptomix may display a warning after successful encryption of the victim machine.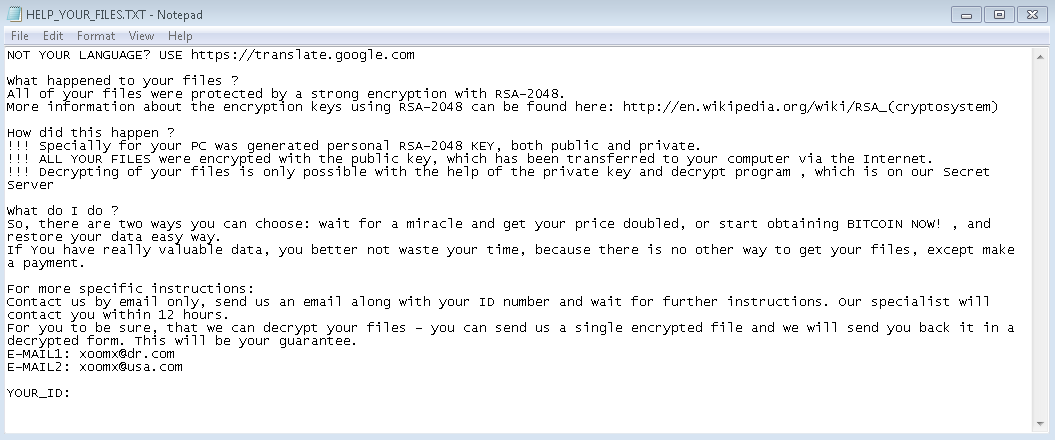
Type and source of infection
Ransom.Cryptomix may be distributed using various methods. This software may be packaged with free online software, or could be disguised as a harmless program and distributed by email. Alternatively, this software may be installed by websites using software vulnerabilities. Infections that occur in this manner are usually silent and happen without user knowledge or consent.
Aftermath
Systems affected by ransomware are rendered unusable due to files that are typically used for regular operations being encrypted.Affected users who choose to pay the threat actors behind ransomware campaigns in exchange for access to data may find that they don’t get their files back. There is also no sure way to know that threat actors will honor their end of the deal after paying the ransom.Affected users who chose to pay the threat actors may also find themselves likely targets for future ransomware campaigns.Data held hostage that wasn’t given back to users or deleted after the ransom has been paid can be used by threat actors either to (a) sell on the black market or (b) create a profile of the user they can use for fraud.
Protection
Malwarebytes protects users from the installation of Ransom.Cryptomix.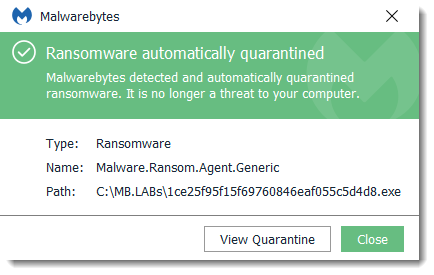
Home remediation
Malwarebytes can detect and remove Ransom.Cryptomix without further user interaction.
- Please download Malwarebytesto your desktop.
- Double-click MBSetup.exeand follow the prompts to install the program.
- When your Malwarebytes for Windowsinstallation completes, the program opens to the Welcome to Malwarebytes screen.
- Click on the Get started button.
- Click Scan to start a Threat Scan.
- Click Quarantineto remove the found threats.
- Reboot the system if prompted to complete the removal process.
Take note, however, that removing this ransomware does not decrypt your files. You can only get your files back from backups you made before the infection happened.
Business remediation
How to remove Ransom.Cryptomix with the Malwarebytes Nebula console
You can use the Malwarebytes Anti-Malware Nebula console to scan endpoints.

Nebula endpoint tasks menu
Choose the Scan + Quarantine option. Afterwards you can check the Detections pageto see which threats were found.
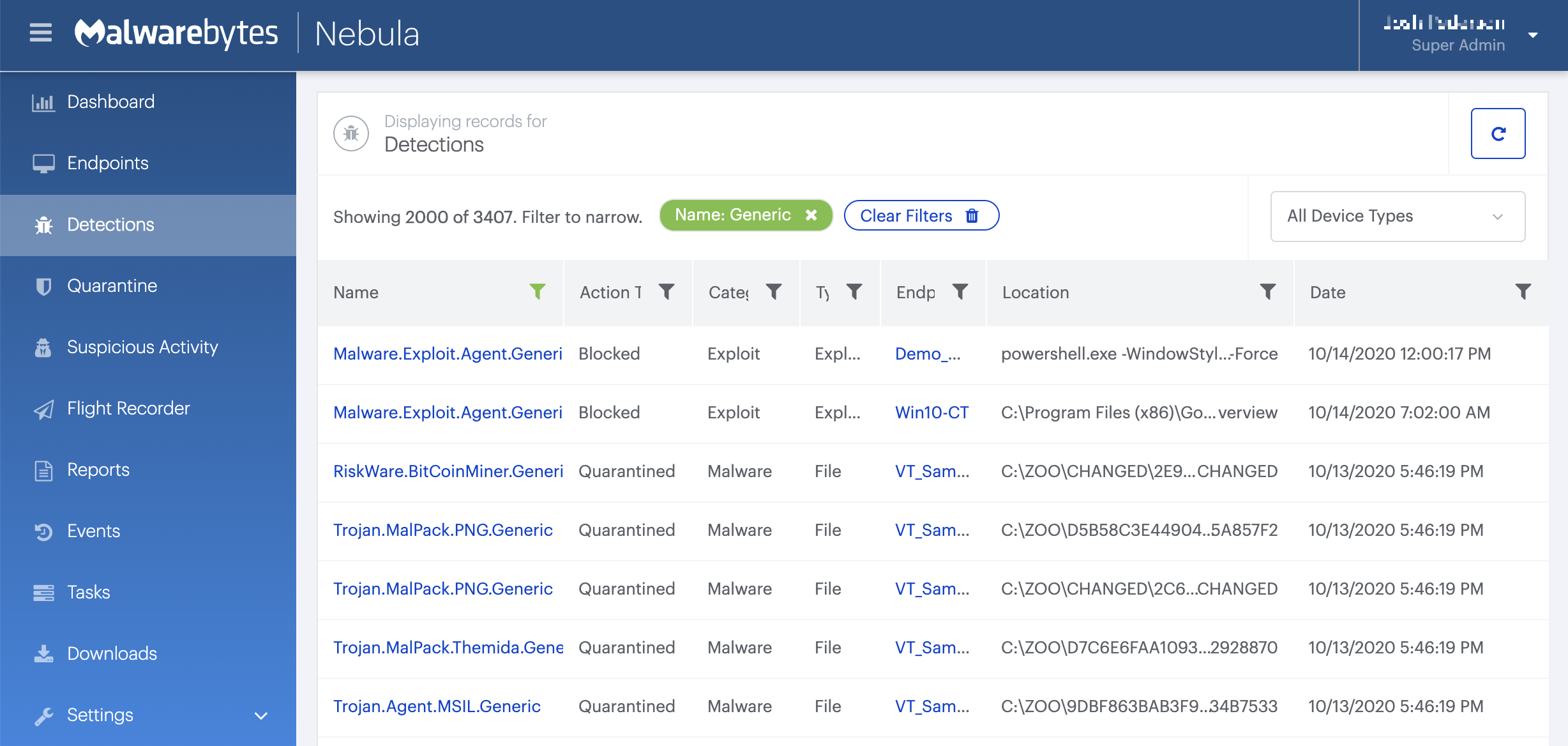
On the Quarantine pageyou can see which threats were quarantined and restore them if necessary.
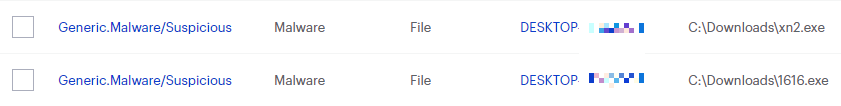
All component/technology detections are passed to the remediation engine for complete removal from infected systems. This industry leading technology uses patented techniques in identifying all cohorts or associated files for a single threat and removes them all together to prevent malware from resuscitating itself. If you are using Malwarebytes Ransomware Rollback technology, it allows you to wind back the clock to negate the impact of ransomware by leveraging just-in-time backups.
Traces/IOCs
Ransom file extensions
| .AZER | .MOLE | .rmd |
| .CK | .mole00 | .rscl |
| .CNC | .mole02 | .scl |
| .code | .mole03 | .SHARK |
| .CRYPTOSHIELD | .NOOB | .WALLET |
| .ERROR | .OGONIA | .x1881 |
| .EXTE | .PIRATE | .ZAYKA |
| .lesli | .rdmk | .ZERO |





