Ransom.Crysis
Short bio
Ransom.Crysis is Malwarebytes’ detection name for a family of ransomware also known as CrySis or Dharma that targets Windows systems.
Symptoms
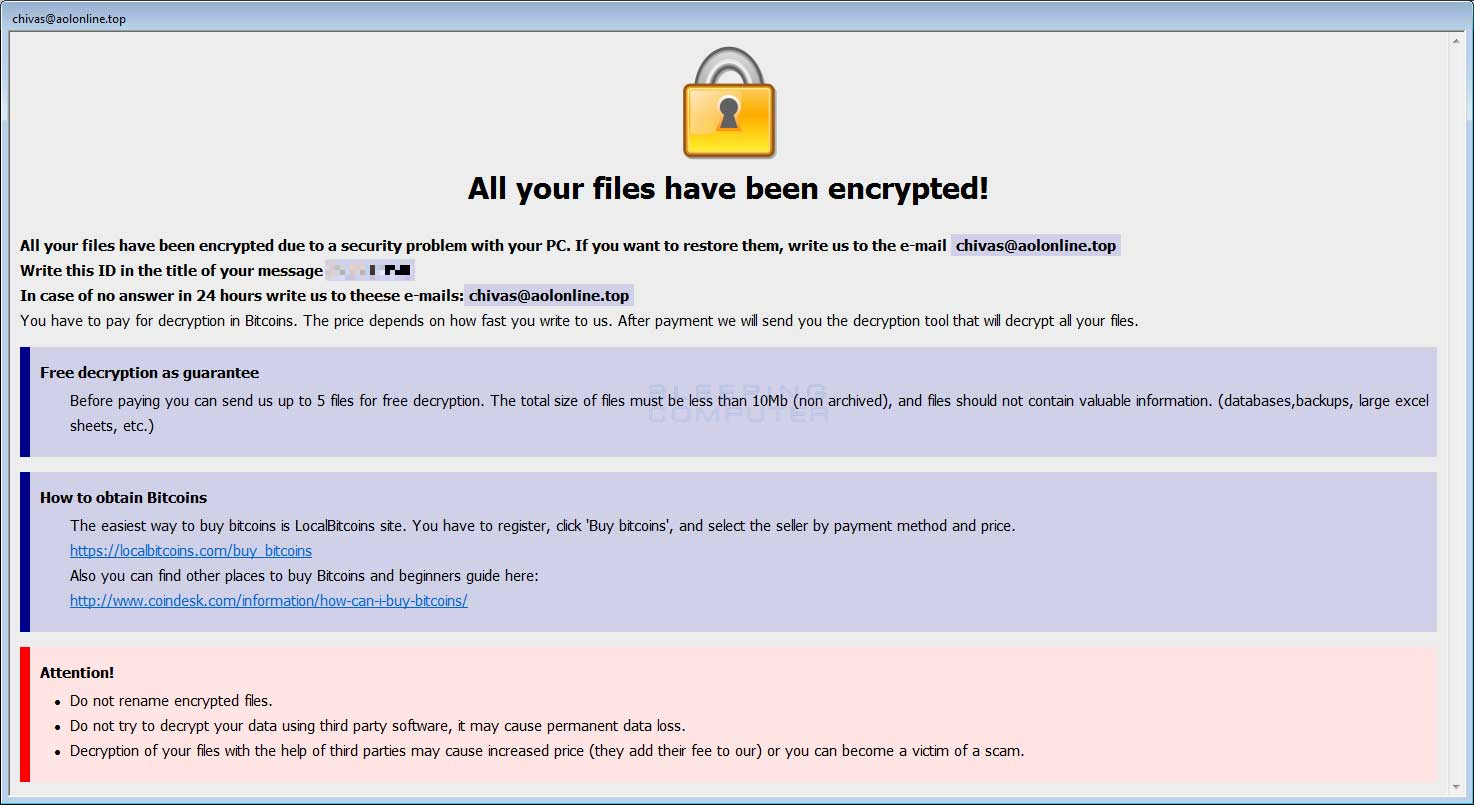
Users of infected systems will find a ransomnote on their desktop when the decryption routine has been completed. They may also notice that all their restore points are gone and that their files are no longer accessible because they have been encrypted and given a new extension.
Type and source of infection
Ransom.Crysis is ransomware that encrypts files on an infected system. Ransomware in general is a type of malware that prevents users from accessing their system or personal files and demands a ransom payment in order to regain access. Ransom.Crysis uses several methods to infect a system, it can be done manually by use of weak or leaked RDP passwords, by malicious mail attachments, and sometimes it is offered for download as an installer for a game or other legitimate software.
Aftermath
Ransom.Crysis deletes restore points by running the vssadmin delete shadows /all /quiet command. So if these restore points were part of your backup plan they could be lost if the ransomware has been running.
Protection
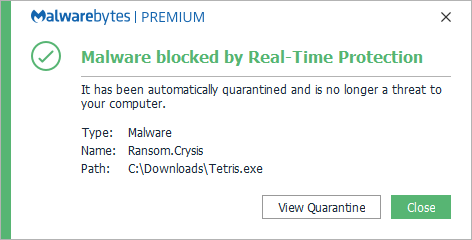
Malwarebytes blocks Ransom.Crysis
Business remediation
Malwarebytes can detect and remove Ransom.Crysis on business machines without further user interaction. To remove Ransom.Crysis using Malwarebytes business products, follow the instructions below.
How to remove Ransom.Crysis with Malwarebytes Endpoint Protection
- Go to the Malwarebytes Cloud console.
- To allow you to invoke a scan while the machine is off the network, go to Settings > Policies > your policy > General.
- Under Endpoint Interface Options, turn ON:
- Show Malwarebytes icon in notification area
- Allow users to run a Threat Scan (all threats will be quarantined automatically)
- Log into your My Account page and copy your license key. The key is needed to activate MBBR tool.
- Open your Cloud console.
- From a clean and safe machine, go to Endpoints > Add > Malwarebytes Breach Remediation. This will download the MBBR zip package.
- Unzip the package.
- Access a Windows command line prompt and issue the following commands: mbbr register –key:
mbbr update Note: You must substitute your license key for . - Copy the MBBR folder to a flash drive.
- From an infected, offline machine, copy the MBBR folder from the flash drive.
- Start a scan using the following command: mbbr scan –full –ark –remove –noreboot
- Refer to the Malwarebytes Breach Remediation Windows Administrator Guide for all supported scanning commands.
After removal it is imperative to find the source of infection to prevent it from being used again. If the ransomware has run briefly before being stopped by our behavioral detection methods, check for the presence of created Restore points and use our roll-back technology to recover any encrypted files.
Home remediation
Malwarebytes can detect and remove Ransom.Crysis without further user interaction.
- Please download Malwarebytes to your desktop.
- Double-click MBSetup.exe and follow the prompts to install the program.
- When your Malwarebytes for Windows installation completes, the program opens to the Welcome to Malwarebytes screen.
- Click on the Get started button.
- Click Scan to start a Threat Scan.
- Click Quarantine to remove the found threats.
- Reboot the system if prompted to complete the removal process.
Take note, however, that removing this ransomware does not decrypt your files. You can only get your files back from backups you made before the infection happened or when you are using roll-back technology.
Traces/IOCs
Extensions
Ransom.Crysis has been known to append these extensions for encrypted files: .crysis, .dharma, wallet, .java, .adobe, .viper1, .write, .bip, .zzzzz, .viper2, .arrow, .gif, .xtbl, .onion, .bip, .cezar, .combo, .cesar, .cmb, .AUF, .arena, .brrr, .btc, .cobra, .gamma, .heets, .java, .monro, .USA, .bkp, .xwx, .btc, .best, .bgtx, .boost, .heets, .waifu, .qwe, .gamma, .ETH, .bet, ta, .air, .vanss, . 888, .FUNNY, .amber, .gdb, .frend, .like, .KARLS, .xxxxx, .aqva, .lock, .korea, .plomb, .tron, .NWA, .AUDIT, .com, .cccmn, .azero, .Bear, .bk666, .fire, .stun, .myjob, .ms13, .war, .carcn, .risk, .btix, .bkpx, .he, .ets, .santa, .gate, .bizer, .LOVE, .LDPR, .MERS, .bat, .qbix, .aa1, and .wal
The following ransom note names have been found: • README.txt • HOW TO DECRYPT YOUR DATA.txt • Readme to restore your files.txt • Decryption instructions.txt • FILES ENCRYPTED.txt • Files encrypted!!.txt • Info.hta
Some common file hashes: • 0aaad9fd6d9de6a189e89709e052f06b • bd3e58a09341d6f40bf9178940ef6603 • 38dd369ddf045d1b9e1bfbb15a463d4c





