Update (1/14/2013)
Oracle has issued an emergency patch to be shipped with version 7 update 11. While we are pleased to see a quick turnaround time, we stand by our initial recommendations to disable Java in your browser. This is still the most exploited piece of software and whether it is patched or not still unnecessarily puts you at risk. Also, despite this patch the consensus among security researchers is that Java is still riddled with potential security holes and it’s only a matter of time until we hear about yet another zero day.
Original post:
As mentioned in our security advisory, a new exploit is affecting the latest version (version 7 update 10) of Oracle Java. Since there is no patch available (0 day) at the time of writing, all Windows computers running Java are exposed to malware infections. If you need a refresher in what a drive-by exploit is, it is an attack against an application that allows the execution of arbitrary code, meaning it can download and install malware on your system without you knowing. It is composed of three parts:
- Application Code Execution
- Exploit Code Execution
- Payload Execution
The Bait
An important piece that isn’t necessarily part of the drive-by exploit process is what we like to call the ‘bait’. What that means is how exactly you would get a user to navigate to the web page that included the exploit code. The usual method of baiting a user could be one or more of the following:
- Advertising the links as something else, like a video, a coupon or just something of unique interest to the user
- Including code in a Malicious Advertisement or Malvertisement that redirects the user to the exploit page without their consent
- Hijacking a previously well visited legitimate site and secretly embedding the exploit code within its web pages
We suspect that the ways in which the exploit code was spread followed one of the above methods. The below screenshot shows a previous example of baiting a user by using malware that hijacked Skype accounts and sent messages to the user:
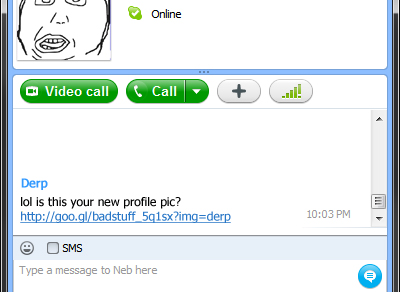
As for which sites are hosting this malware or being used to redirect users, what we have seen so far are nothing new, many of the web servers used are ones that have been used before for botnet spreading and scamming users in a variety of ways. Clearly it was important for cyber-criminals to get their exploits out as fast as they could before patches came out and/or people got wise.
Application Code
Once the user falls for the ‘bait’ and clicks on the link or is redirected to the exploit page, in order to execute the exploit code the web page must first execute JavaScript code embedded in the web page. This code usually involves seemingly harmless commands that appear to tell the browser to execute a long and nonsensical string of characters. In reality, the string of characters is actually the encrypted exploit code, and the JavaScript code will decrypt this string by modifying the characters, rearranging them and adding new ones that make what was previously nothing into harmful code.
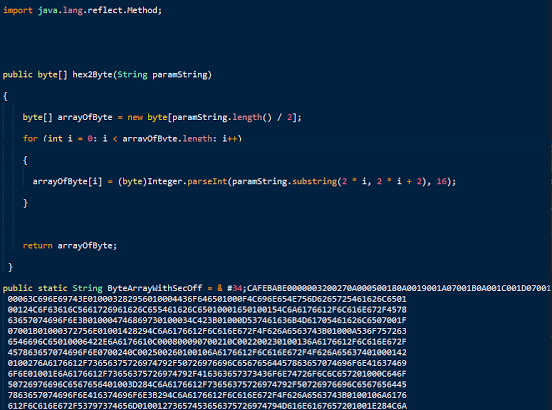
The above screenshot is a snippet of the code used in the 0 day exploit we are talking about. As you can see the string at the bottom of the snipped is the encrypted exploit code and a few lines up you can see mathematical operations being done that will assist in the decrypting and eventual execution of this code.
Exploit Code
The most important aspect of this blog post is the actual exploit, not so much how it got where it got or what it delivers but what the exploit itself does that makes it so dangerous. The decrypted exploit will run an attack a code vulnerability in the Java application that gives the exploit code the ability to execute code on the victim machine and eventually infect it with malware. At this time there is no protection against this attack unless the user has disabled the browser integrated Java application. To make matters worse, this vulnerability is being used in multiple Exploit Packs. French researcher ‘Kafeine’ has spotted it in:
- Cool Exploit Kit
- Nuclear Pack
- Redkit
- Backhole
- Sakura
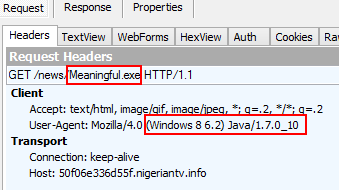
We managed to infect a fully up-to-date Windows 8 machine also running Microsoft Windows Defender.
Click below to watch the video capture:
Here is the summary:
Exploit kit launches malicious Java file which downloads and runs the malware payload (application/x-msdownload):
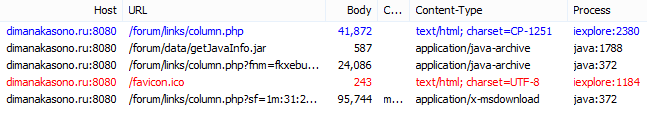
In more and more cases, we are seeing encryption of the malware binary and on-the-fly decryption by the Java process. This is an attempt at hiding the malicious payload while it is in transit (being downloaded).
A typical malware binary would look like this:
An encrypted one might look like that:
The following screenshot shows a portion of the malicious Java applet referring to AES encryption:
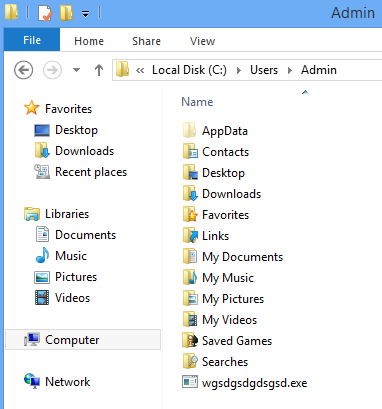
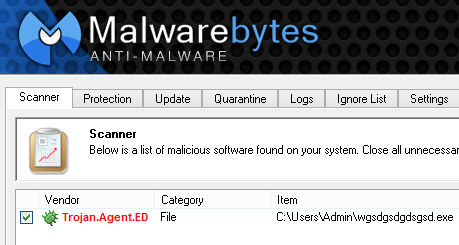
Once the file is downloaded, it is decrypted and then run on the system from a folder like the one identified below where wgsdgsdgdsgsd.exe is the malicious file:
At the time of writing the above malware has a detection ratio of (5/45) on VirusTotal. Our Malwarebytes Anti-Malware detects it as Trojan.Agent.ED:
The Payload
The above referenced malware is only one of the many different kinds that have been infecting systems by using this exploit. Since the exploit is being used within Exploit Kits, like Blackhole, it is available to all cyber-criminals employing the use of said Exploit Kit and can use it to infect victims with whatever malware they want. In this case we have so far seen two very different types of malware being spread with this exploit.
- Rootkits
- Ransomware
The difference between the two is immense however it is also a great example of how the exploit has been brought to the attention of all types of cyber criminals. We can see this because Rootkit malware is almost always used for information stealing, like credit card numbers or usernames and passwords. It is meant to be stealthy, hidden and effective and will stay on a system as long as it wants without the user ever knowing it. Ransomware, however, uses tactics in the opposite direction from Rootkits because it is loud, obvious and out for only one thing, money.
The Ransomware we have seen being spread is the Reveton ransomware, which is a fairly well known Ransomware style malware and one of the ones we have discussed in the past.
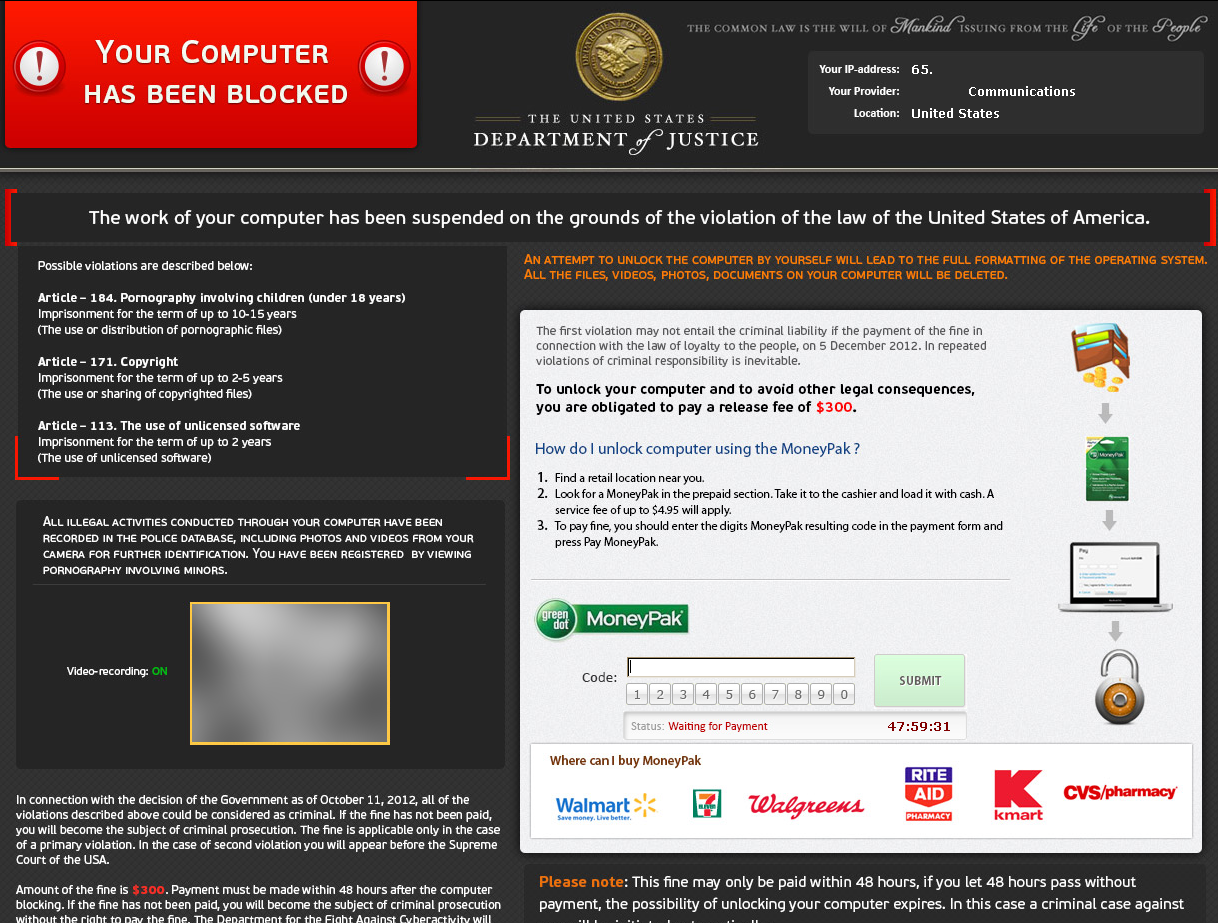
An interesting observation about this variant of Reveton is that the ransom price has gone up by $100 than it was only a couple of months ago! This is indicative of greedy cyber-criminals whom either want to get as much money out of people while this scam is still effective, or actually believe that people will pay anything to get their system back. Based on the increased level of detail we have seen in the evolution of the Reveton ransomware, we think its pretty obvious why people keep falling for this scam.
Nearly all of the malware we have seen been used in the operations of the 0 day exploit are already well detected by the major antivirus and anti-malware companies, a few of them had very low detection rates but expect them to rise over the next few days. An interesting question to ask of the kind of malware being spread by this ‘Brand New’ exploit is, “Why was it wasted?” We don’t think it was, in fact there is a very large possibility that this exploit has been available, deep in the underground parts of the cyber-crime organizations for a little while and already been used a few times to attack users with malware that is just as stealthy an unknown. Maybe we will see something like that popup in the next few days as deeper analysis is done on this exploit and even more efforts are made to track down even more attack servers.
Conclusion
Exploit code is very dangerous, it always has been and it always will be. The purpose for its existence is to take advantage of flawed coding done by (more than likely) overworked programmers and turn it into an attack vector before anyone can stop it or do anything about it. Even though this particular exploit is more dangerous than others we have seen in its ability to infect people who have been following good security practices, the biggest audience that exploits attack are users who do the opposite. Users who fail to update their software are still vulnerable to exploit attacks that had been patched years before. These users are the perfect candidates for the cyber criminals and while it seems like only a simple person could fail to protect themselves against an old threat, it happens to everyone who might just of forgotten or turned off their update notices or automatic updates because it annoyed them in some way.
When looking at the exploit payload, in this case it isn’t important at all what malware is being used because every type of malware will use this exploit and will probably use it for at least another year before the market of vulnerable users has dwindled so much that it isn’t worth the investment. That is why it is so imperative to pay attention to the warnings of the security community and if we say you should update, then update and if we say you should disable, disable. It hopefully will not take more than a few days to find the vulnerability being exploited by the cyber-criminals and patch it so that the next update of Java will be immune. When that happens, be sure to look out for the community to say its all clear. Thanks for reading and stay safe!
Thanks to Adam Kujawa for additional research material.










