Last week security researchers from FireEye discovered a new Java exploit that works against the latest versions of Java (version 6 update 41 and version 7 updated 15) making this a zero-day. The flaw is not just a proof of concept but has been spotted in the wild and it will be just a matter of time before it becomes more widely distributed in various Exploit Kits.
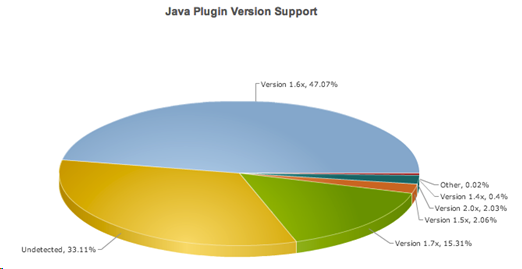
To make matters worse, Oracle had already announced end of life support for Java version 6 after February 2013 but the gravity of the situation forced the company to once again extend the date to mitigate some very serious security issues that would affect a large amount of consumers and enterprises. According to statowl.com, almost half of all users running Java are still using version 6.
Recent attacks against Apple, Facebook and Twitter all used Java zero days to penetrate the companies’ networks and install Remote Administration Trojans. What is important to realize is that no matter how up-to-date those systems were, and even with antivirus and firewall, they still got compromised. This shows just how dangerous web exploits and zero days are.
The bad guys keep on finding new ways to distribute their payload. It took many high profile companies that got hacked through spear phishing email attacks for people to become more aware and prudent when opening email attachments or clicking links, even when so-called emails were from ‘friends’ or ‘colleagues’. The most recent wave of attacks uses a technique known as “watering hole” in reference to jungle animals quenching their thirst in the rare pools of water they encounter. In other words, find out where your victims are hanging out and try to exploit them there. This is what happened to some Apple employees who frequently visited an iOS developer forum. The exploit was injected within the site itself so that visiting any page on there would trigger a drive-by download attack possibly exploiting an unknown Java vulnerability. The downloaded payload is believed to be a backdoor specially crafted for OS X and discussed in detail by security firm Intego.
The ‘beauty’ of Java is that it is cross platform compatible which makes it easy for software developers to write their program once and have it run on all sorts of devices. Add to that the fact that Java is used by consumers, enterprises, schools, etc. and you start to see why it is such an enticing target for malware authors.
The common advice we hear is to remove or disable Java. While it is a good idea, not everyone can or wants to get rid of it. Many applications depend on it and removing Java would just break them and cause just as much of a mess. There are a couple of things to keep in mind:
- Java can be run as a standalone desktop program
- Java can be run within the browser
The most serious issue is Java in the browser as this is how web exploits are delivered. That is why it is a sound practice to disable it or even remove it completely. For people that still require it for certain websites I recommend the two browsers approach:
- Use a browser without Java for your daily web surfing (i.e. Google Chrome)
- Use a different browser (i.e. Firefox) strictly for the site that requires Java. It may even be a good idea to bookmark that site so you go there directly without visiting any other page.
An even safer approach (and this makes more sense perhaps for enterprises), is to use dedicated Virtual Machines for web browsing with Java and other plugins for that matter.
Truth be told, zero days can make anyone paranoid about browsing the web. Sadly, there is no such thing as 100% security and even security companies themselves get hacked (remember RSA, or more recently Bit9?). The best thing one can do is to reduce their exposure and have an incident response plan. This does not necessarily only apply to companies: anybody keeps valuable data on their computers and should know what to do if something happened to it. Encrypting sensitive files, backing up data and having a quick way to get back on your feet will go a long way when (not if) you get hacked.










