URGENT: Despite a recent critical patch to Java SE, Polish security firm Security Explorations released details of yet another Java vulnerability. Adam Gowdiak, a researcher from the firm provides a full disclosure of the exploit here.
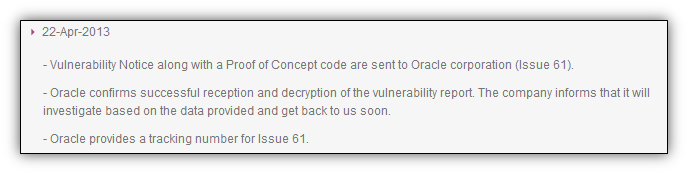
Submission of Issue 61 to Oracle
ACTION: Same routine here, users should disable java in their browsers using the following instructions (courtesy of Sophos):










