If you use your debit or credit card to buy groceries or get cash out of an ATM you might want to know that the bad guys could have a piece of it.
Researchers at Russian security firm Group-IB say that customers from some of the largest US banks have been affected by malware that steals credit card data directly from ATMs as well as point-of-sale (POS) terminals found at regular retailers. Cyber-crooks are infecting the Operating System that powers ATMs and point-of-sale terminals with malware capable of stealing financial data.
The business model behind going directly to the source is efficient because criminals only need to compromise a few ATMs to collect hundreds, if not thousands, of credit card numbers which can immediately be sold on the black market.

Historically, the bad guys have used many methods to carry out credit card or online banking fraud. Let’s review a few:
Phishing Sites
Phishing is the act of requesting personal information from the user under false pretenses. Phishing and spam often go hand in hand as victims tend to be lured via emails asking them to update their banking details or review recent transactions. Once they enter their information into the fraudulent site, those usernames and passwords are sent to cyber criminals who quickly proceed to empty the accounts.
Keyloggers
There are two forms of keyloggers: hardware and software ones. The former come as devices that hook on the victim’s machine or are embedded in the hardware itself. Of course, physical access is required in order to plant hardware keyloggers. Much more common are software keyloggers, which are delivered through infected programs or when someone browses to a compromised website and gets hit with a drive-by download.
Skimmers
Skimming consists of stealing card details during a legitimate transaction. One way it is done is by placing an innocuous chip reader on an existing ATM. When the victim inserts his or her card, it is read by both the rogue device and the ATM. The transaction goes through as normal, but the card’s details have also been stolen.
ATMs and Point-of-Sale Terminals Are Vulnerable Too…
Let’s not forget that ATMs and POS terminals run computers, with the traditional CPU, RAM and HDD and Operating System (Windows/Linux). If that makes you cringe, some are still running old and unpatched Microsoft Windows XP versions.
Those systems are wired to other networks and the Internet (for some cool but risky remote login features), so it’s not big surprise that they can be probed by doing network scans as well as using brute force techniques to login externally. Given that many people (re)use weak passwords this is like stealing candy from a baby.
The POS’s software itself is not immune against bugs and can be exploited by hackers remotely. To learn more about vulnerabilities in POS software you can read this article by Tracy Kitten of BankInfoSecurity.
VegaPos: a POS program made by a Turkish company
I obtained an ATM/POS malware sample and even a video tutorial on how this works and it looks just too easy.

well.exe (malware) along with other POS software
well.exe is the name of the malware file. which, when executed, copies itself to the current user’s directory under the name svhst.exe and adds a registry entry to ensure persistence (it will run again when the terminal is rebooted). It collects credit card numbers from the ATM or POS and sends them back via FTP to a remote server hosted by a Russian-based ISP. The cyber criminals then log into a web interface to view the collected credit card details.

Web control panel to collect credit card data
To check whether the cards are valid as well as which bank they are from, carders use free services like BIN Checker. “BIN” stands for bank identification number and consists of the first six digits on the card.
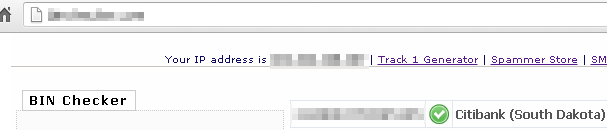
Website to check credit card numbers by bank/country.
You might be surprised to find out that this service is…

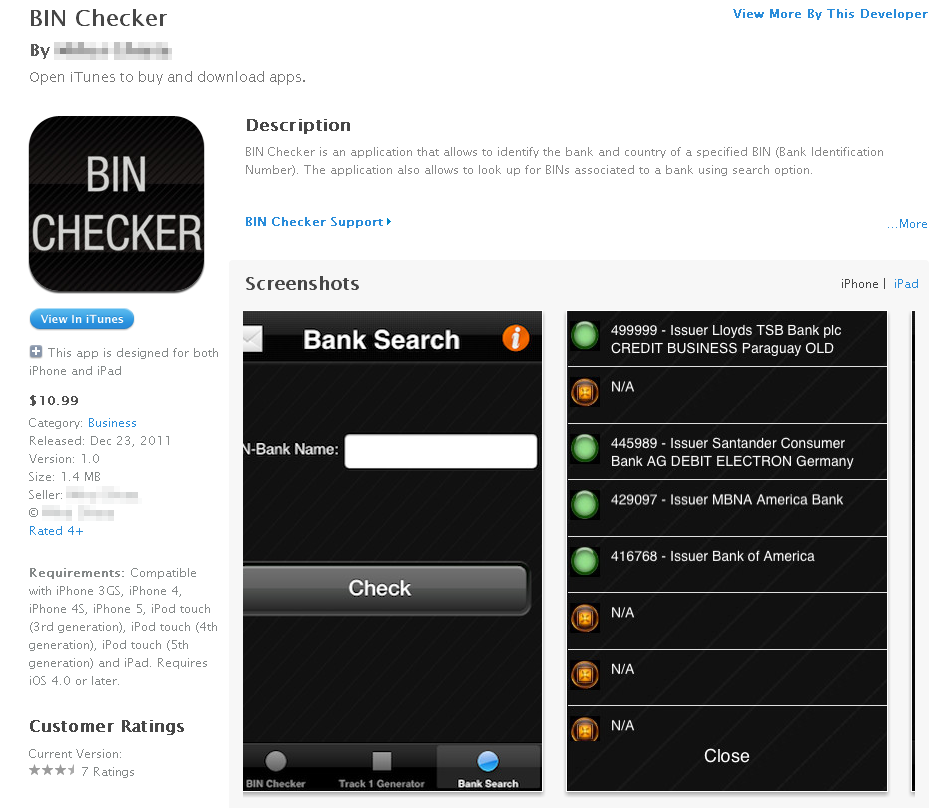
The iPhone/iPad app of the above website
Although checking BIN numbers is not illegal, this app’s website links to another site that sells email lists for spam as well as hacking tools:
Email list for spamming purposes
A famous backdoor/shell used in website compromises
I’m baffled to see the social networking integration (“Like this on Facebook”). I guess there must be no shame in doing these sorts of things nowadays and being public about it?
When I recently traveled for business to San Francisco my credit card got compromised. I assumed it was probably from a skimming device at a local grocery store or the like. The credit card company notified me that someone had attempted to purchase $800 worth of goods at a Walmart in a different state. I always look for a padlock on the card reader and sometimes for that sticker that shows it has not been counterfeited, but honestly there are times when you’ve had a long day and you just don’t want to have the cashier look at you like you’re a weirdo.
Well, given this ATM/POS malware should I bring my own anti-malware solution and do a full system scan before doing my transaction? This is getting ridiculous. It makes me wonder if the credit card firms treat fraud as a “business expense” and raise the interest rate every now and again to cover it. Either way, some individuals are making a boatload of money and causing major annoyances to everyday consumers, and that should not go unnoticed.









