Back in 2003 when Valve released its now well-known game distribution software called Steam, I wasn’t immediately sold on the idea. I figured a gaming platform that imposed more restrictions on the user (like DRM technology) and a required Internet connection would never really take off.
However, my feelings made a sharp change the following year, in 2004, when the blockbuster title Half-Life 2 was released to gamers abroad. As I inserted the game’s install CD into my PC I soon realized one thing: Valve developed both the game and Steam software, and it was therefore their prerogative to require Steam to play the long-awaited Freeman-filled shooter. And thus, after a series of long and painful mouse clicks, Steam was installed: I drank the Kool-Aid. Now you’ll find me saying “Loyalty until Underverse come” when asked my opinion on Steam.

OK, so maybe it wasn’t that big of a deal, but Steam really did change my gaming experience forever, and I’d say it’s mostly all been positive.
Nevertheless, as with anything that becomes popular on the web, bad guys pay attention too, and look to make a profit where they can. With that in mind, let’s take a quick look at some things you may want to watch out for when gaming with Steam.
Even today, almost a decade after Steam’s initial release, the digital game platform continues to improve selections, grow its user base, and expand its list of supported devices. Steam has gotten so popular that, at any given time, there are millions of gamers logged into Steam, browsing the store and playing games — but that just means more targets for the bad guys.
Many Steam key generators (keygens) are advertised on the web through social media and other channels. Steam keys are codes that users can enter to activate a game on Steam, much like a normal CD key is used to curb piracy. Once a game is activated on Steam, you can download and play it just as if you purchased it from the Steam store.

All of these keygens are fakes and usually lead to something you don’t want. I discovered one on Facebook for Bioshock Infinite (above), a game released just back in March. I went over to the advertised website and clicked on the download link—as expected, I found a scam used to collect my personal info or install arbitrary software. At least they gave me choices, right?

Similarly, I found the same “deal” offered for Dishonored on a similar website that used the same URL scheme. These two sites (which are Google Blogger sites) are likely created by the same guy.

This keygen led to the same scam, advertising the exact same products and surveys.
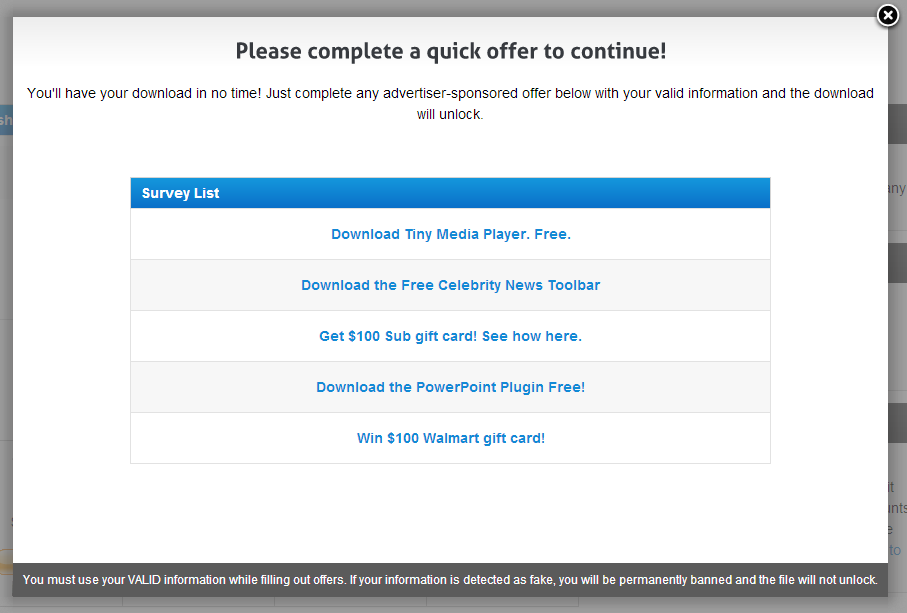
I tried a couple of these, including the Celebrity News Toolbar and PowerPoint Plugin, but neither installation got me a free game—instead, I was stuck with lame browser add-ons and the blinkx media player. As I mentioned on my blog about the Xbox One emulator, don’t fall for these tricks unless you’re looking for more adware and other potentially nasty software.
In addition to Steam key scams there are also several key resellers advertised online that will sell you a key activated on Steam.
There are some problems with this approach. First, the vast majority of these resellers are not authorized by Steam, and therefore you’re taking a big risk when buying a key from any of these vendors. If you purchase a key from one of these sites, Steam can do nothing to intervene on your behalf should the key not be delivered or you encounter a problem.
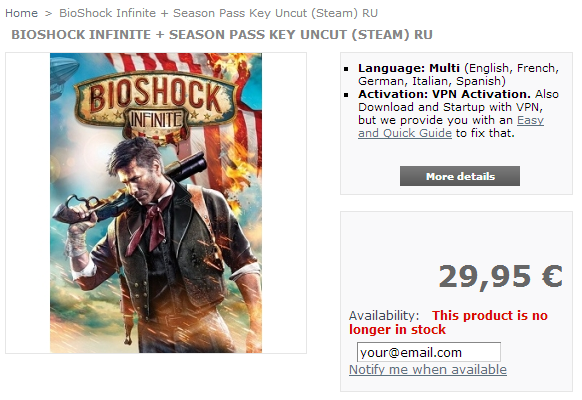
Also, most of the keys purchased through these resellers are for different regions (when you purchase a game on Steam, it is tied to a specific region). A lot of the keys found are for European regions, and most often Russia, offered for considerably less than U.S. keys.

Key Pickup area for customers at CDKey Warehouse (https://cdkeys.com.au/)
Since you naturally can’t play Steam games for a region you’re not physically located in, many of these resellers offer a VPN workaround to activate, download, and play the games. In order to play the Dishonored key (above), a user would need to download the reseller’s VPN client, which for this vendor is in the form of a Microsoft phonebook file (.pbk) filled with VPN connection info for several countries.
Just to be sure about all of this, I emailed Steam support to clarify. Here is the response I got after asking about one specific vendor (http://www.gamekeys4u.net/).
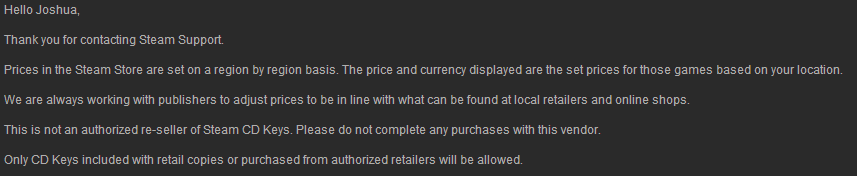
There’s really no telling where the keys from these vendors come from, or even if they’re stolen or not. Also, the key may just not work, and you’re definitely not getting your money back from Steam since the vendors aren’t authorized.
Let’s be honest: most of us are looking at third-party vendors and key giveaways because we’re disgruntled about the price we see at the Steam store. So, what do you do to get the best price?
I know this may sound old-fashioned, but patience proves to be the best choice when looking for a Steam bargain. Price drops will come with time, but waiting for that “right price” usually isn’t an attractive option when a new hit title is just released.
That’s what sales are for. Steam is littered with sales that occur every week, and even bigger sales happen around the holidays. As a matter of fact, I think I bought a game almost every day around Christmas last year, and I never had to resort to a reseller for keys. Steam sales are really where you’re going to get the most out of your money, and the peace of mind knowing your purchases are backed by Steam.

Lastly, if you’re looking for a safe alternative to buying a game on Steam, you can always buy a copy of the game from your favorite retailer if you find the price cheaper. Once you purchase the game, there’s a chance you can use the CD key to activate the product on Steam, and then download the game just as if you bought it from the Steam store. For a list of retail keys that are accepted on Steam, click here.
_______________________________________________________________________________
Joshua Cannell is a Malware Intelligence Analyst at Malwarebytes where he performs research and in-depth analysis on current malware threats. He has over 5 years of experience working with US defense intelligence agencies where he analyzed malware and developed defense strategies through reverse engineering techniques. His articles on the Unpacked blog feature the latest news in malware as well as full-length technical analysis. Follow him on Twitter @joshcannell









