This morning, Michael Callahan of Juniper Networks posted an article on SecurityWeek.com about distributed denial of service, or DDOS, called “Take a Broader, Deeper, Wider Bite out of Cybercrime.”
A DDOS attack is when numerous client systems send massive amounts of network traffic to a single web server in the hopes of making it impossible for legitimate users to access the server and/or crash the server with the overwhelming amount of traffic. The attack consist of hundreds or thousands of systems knocking on the door of the web server but then running away when the server answers. Another good analogy is if you were going to shake someones hand and when they reached out, you move your hand away and run it through your hair. Now imagine that the server is the sucker reaching for the hand and 10,000 people are moving their hand away at the same time. The result is the server waiting for a response that will never come and being highly distracted in the process, so much that legitimate users who want to shake hands are unable to get the servers attention.

Callahan speaks about the history of DDOS in his article and makes a suggestion to the cyber security community of treating DDOS as a bigger threat than they have typically been seen. He mentions numerous examples of DDOS attacks being used not only for the denial of information or services but also as a distraction method; while network administrators are busy trying to keep their systems up during a DDOS attack, cyber criminals can sneak in back doors and steal information or money without anyone noticing. He addresses the problem by proposing a modifcation in where we rank DDOS attacks in comparison to other cyber attacks such as banker trojans or rootkits. In addition, he admits that DDOS attacks can’t be stopped by provides ample methods of mitigating the risk they pose to an organization.
LOIC
I thought that in addition to this doorbell ditch tactic being used by cyber criminals, it would be good to mention just how easy DDOS attacks are to deploy for your average disgruntled user. Many of you who spend a lot of time on the unofficial parts of the internet might recognize the Low Orbit Ion Cannon or (LOIC) a free tool developed by someone with intent and the desire to make a DDOS tool so simple that anyone who can point a mouse can launch an attack.
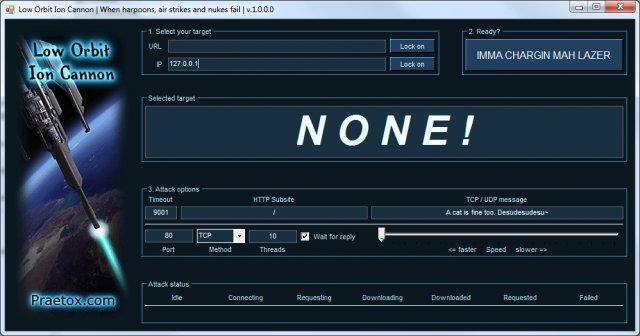
This tool is used particularly by the group “Anonymous” and in great numbers. The potential attacker simply enters the URL or IP of the server they want to attack, make some slight configurations based on the desired target and frequency of the attack and then just click a button and they are off. While individuals using this tool on their own will have little to no effect on any larger web targets, members of Anonymous pack a greater punch. When the Anonymous hive-mind decide to attack someone, they send out a message to all of their followers/members with instructions on downloading and using the LOIC and provide the address of the intended target. When you get thousands of users all launching our fake-out handshake attack a the same target, at the same time, the results are very effective.
The LOIC is not the only DDOS tool out there and not even the only one that cyber-activists and/or criminals use, just one example. I have seen threads urging users to essentially allow themselves to become part of a botnet in order to DDOS a target, all controlled by a central command and control and most of the time capable of not only attacking a common enemy but allowing the controller of the botnet to steal data from their willing cyber troops.
Coming back around, Callahan’s article really makes some good points about things we as a community need to consider when it comes to DDOS and is also a very amusing read, check it out to learn more.










