I suppose we all saw this coming, ransomware authors are now posing as the NSA, claiming to be using the PRISM system to identify users performing illegal activities and demanding payment for their system to be unlocked.
This new discovery was found by security researcher Kafeine on his blog, an article labeled “Prism themed ransomware – Kovter evolution.”
The ransomware appears after a user has either executed the malware (via trickery no doubt) or by being hit by a drive-by exploit. After some time, the malware covers the screen and makes it impossible for the user to get around the ransom notice by disabling the Task Manager and forcing the notice to the front of the screen; typical ransomware stuff.
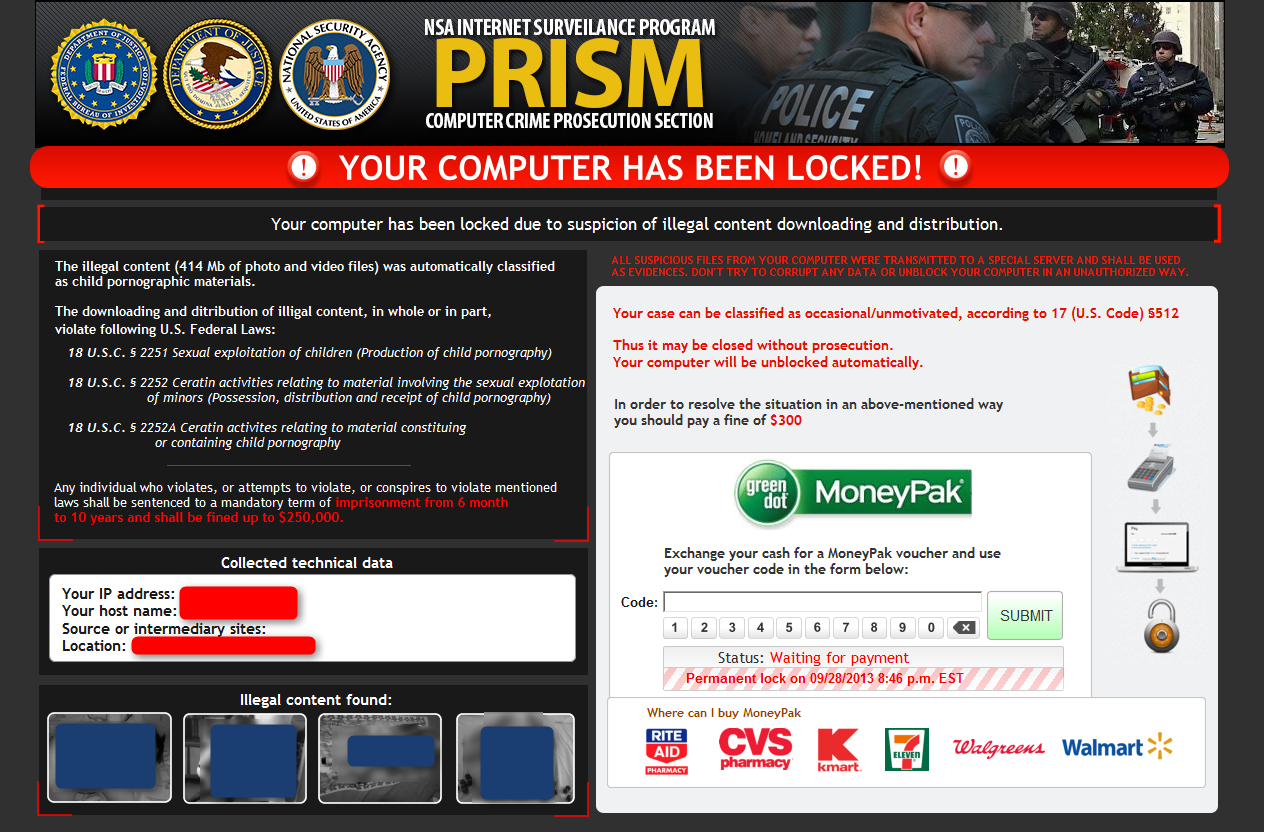
There are a few unique aspects to this Ransomware however, the first being that it claims to be from the NSA and has, in big yellow letters at the top, the label PRISM. Utilizing the recent NSA leaks to their advantage, the attackers use false guilt and current events to fool the user into paying the $300 fine.
The second and third unique aspects (while one isn’t so unique, it is quite disturbing) is the inclusion of child pornography images at the bottom of the notice and the “Source or Intermediary Sites” that is a new feature of the Kovter ransom family.
Kovter searches the users browsing history for a suitable site to blame for the images found on the system. The malware searches through the users browser history and checks against a remote list of sites (porn sites) that the attackers have previously setup. If the user has visited one of these sites recently, it will show up on the notice, if not, the “Source or intermediary sites” field is blank.
The evolution of ransom malware is fascinating in that the attackers keep finding new ways to trick, scam and otherwise guilt users into paying their fine, here is a checklist of methods used by the attackers in this case:
- Notice uses name of government organization that has been in the news lately and the average person is not entirely aware of the reach and ability of said organization
- Notice includes legal looking text, listing laws broken as well as details on specific law being broken (i.e. File sizes, domain of web site obtained from)
- Notice actually shows child pornography, which accomplishes:
- A) There is actually CP on the users system
- B) Shames the user into not seeking help for fear of being accused of looking at CP.
- Notice provides the logos of various legitimate stores where you can buy “MoneyPak” vouchers to pay the fine.
I am, however, surprised that this scam is even still going, some security experts expected ransomware to be a thing of the past at this point, clearly not enough people are aware. So here is my homework to all of you, go out and tell your friends and your family about this, tell them to tell their friends and so on, make it an old fashioned chain letter or game of telephone. Even if the end result is “There is software that let’s PRISM watch your system and it costs $300, it’s bad” that is good enough for people to be aware of the threat and hopefully not pay the fine and encourage these guys to continue with this style of thievery.
If you happen to know someone who has been infected with this particular scam go ahead and check out our Forums for support.
Malwarebytes Anti-Malware detects this threat at “Malware.Packer.PDX”
Thanks for reading and safe surfing!










