Finding software vulnerabilities is a full-time job for some people, but for another group, discovering a flaw in popular software can be like striking gold — either buy making victims pay up or getting paid via bounty hunter programs.
To better understand why discovering flaws is so popular, we’ll examine what a software vulnerability is and most importantly what can be done with it.
ITSEC defines a vulnerability as “the existence of a weakness, design, or implementation error that can lead to an unexpected, undesirable event compromising the security of the computer system, network, application, or protocol involved.”
Let’s take a simple example to illustrate a possible scenario: you browse to a particular webpage using Internet Explorer when all the sudden a specially crafted font cannot be rendered properly. Instead of displaying an error, the browser performs an authorized operation where malicious code is downloaded and executed.
Since our lives and economy are dependent on computers running software applications, you may get the idea why vulnerabilities can have disastrous consequences.
It could range from a power plant getting shutdown with millions of people left in the dark and cold, a plane crashing when the autopilot software reads instructions from a hacker, etc.
Not all vulnerabilities are equal, though. The Zero Day Initiative lists some key points to determine how severe a flaw is:
- Is the affected product widely deployed?
- Can exploiting the flaw lead to a server or client compromise? At what privilege level?
- Is the flaw exposed in default configurations/installations?
- Are the affected products high value (e.g. databases, e-commerce servers, DNS, routers, firewalls)?
- Does the attacker need to social engineer his victim? (e.g. clicking a link, visiting a site, connecting to a server, etc.)
Based on each of these factors, a ‘value’ will be given to a vulnerability. That value often (if not always) translates into money for the person who’s found it.
In a perfect world, vulnerabilities should be reported to the software vendor first and as soon as possible so that they can be fixed before they are exploited in the wild (i.e. before innocent people suffer the consequences). This is also known as “responsible disclosure”.
However, it doesn’t always happen that way. Some vendors have been known to ignore vulnerabilities reported to them and in some cases to have gone after the person that found them.
In the best of scenarios, a vendor will offer a reward to the researcher, patch the flaw and release it to the public in a timely fashion.
And then, you’ve got the bounty hunters who will only sell their discovery to the highest bidder (may it be legitimate or not).
A special kind of vulnerability known as a ‘zero day’ – meaning no patch exists at the time of its uncovering – has tremendous value for cyber criminals.
They can integrate it in their exploit kits and infect millions of innocent people or in specially crafted webpages and documents to target high value selected companies.
Zero days are the hottest commodities on the black market and can go for tens, sometimes hundreds of thousands dollars a piece.
A couple of weeks ago, rumours of a new zero day affecting Adobe Reader XI started to circulate:
Some people did question the validity of such a claim and for good reason. Very few details were available other than a YouTube video which showed several inconsistencies.
But since this is the only piece of evidence we have, it’s well worth watching it again in HD to get a closer look.
The exploit file:
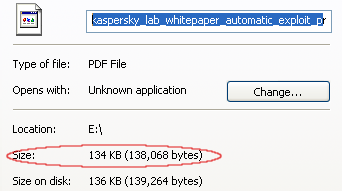
To perform the demonstration, a publicly available PDF from Kaspersky was used:
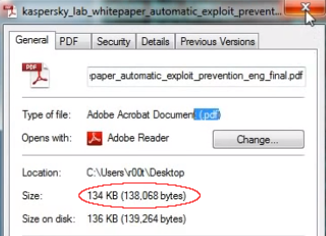
For the zero day to work, some malicious code must be injected, which would account for a different (most likely larger) size for that PDF.
You can download the file for yourself and note that the sizes are identical between a supposedly exploited and clean PDF:
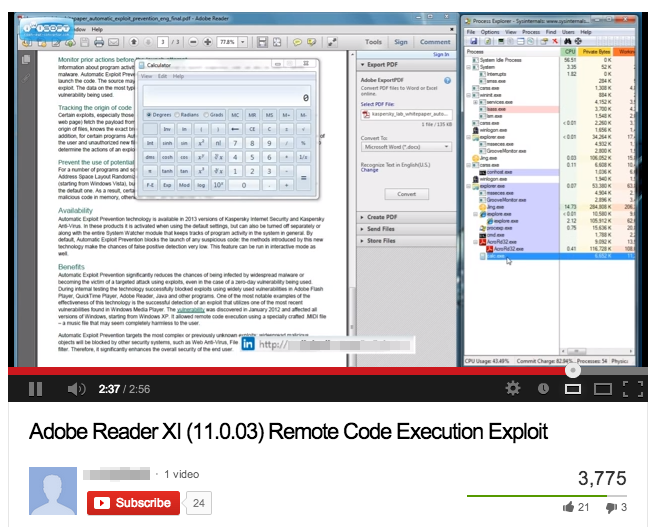
The invisible task bar:
In the YouTube video showing the exploit, one thing that is noticeable is the lack of a task bar showing. Maybe it’s not too big of a deal but in this case it may explain a lot of things.
If you study the video frame by frame and focus on the cursor, you will notice something odd. The mouse is used to scroll all the way down the PDF:
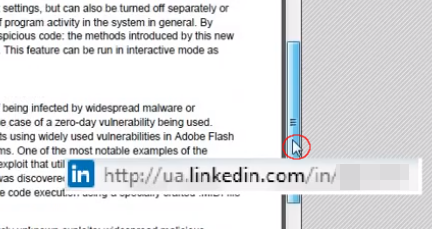
It keeps going down…
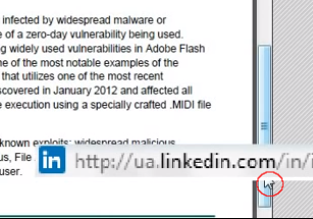
and then it disappears off the screen for a split second!
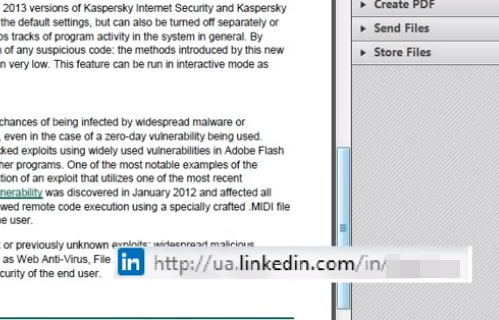
When the mouse finally re-appears, calc.exe is shown (as the proof the exploit happened)
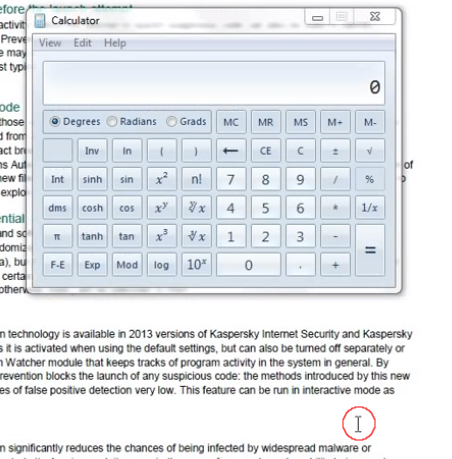
I wondered for a while just where and what that mouse was doing…
My theory is that there is a reason why the taskbar was not shown and that a shortcut to calc.exe may have been placed on it which would explain our last inconsistency.
The Process Explorer tree view:
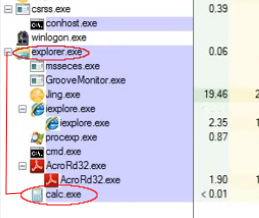
All the exploits I have seen from years of building honeypots always show the payload being a child process of the parent application. So if AcroRd32.exe is the parent application, the payload (calc.exe) should be its child process and show with an indentation.
This is not the case here. What we have is explorer.exe being the parent process. That would confirm my previous theory of clicking a shortcut to launch the calculator.
All in all, there are too many oddities to really take this claim seriously. I’m not sure what steps vulnerability research companies like VUPEN use to assess the trustworthiness of a report, but I would bet they would raise an eyebrow at this one.
Indeed, we are talking about giving a complete stranger tens of thousands of dollars. But then again, the zero day market is something of its own.
Software vendors, nation states, private companies, cyber-criminals all play in the same space, albeit with different budgets and intentions.
But regardless of who is selling what, it’s always good to take things with a grain of salt.
For all other real zero-day threats out there, as well as other drive-by downloads, Malwarebytes Anti-Exploit – the latest addition to our product line – will keep you safe.
It is a great complement to standalone malware protection and lets you browse the web with peace of mind.
Jerome Segura (@jeromesegura) is Senior Security Researcher at Malwarebytes.








