U.S. Federal authorities arrested Ross William Ulbricht–the alleged leader behind the Silk Road criminal marketplace–in San Francisco yesterday, reported multiple news outlets.
Authorities have also seized the Silk Road domain, which is estimated to have done $1.2 billion in illegal sales.

” height=”244″ width=”449″ class=”aligncenter wp-image-2076″>
The Silk Road was only accessible over the TOR network (silkroadvb5piz3r.onion), so navigating to the site in a normal browser wouldn’t work.
This is one instance where TOR is truly a two-edged sword; while it may guarantee user privacy, it can also act as a safe haven for criminal activities and malware operations.
The Silk Road distributed various illegal items and dabbled heavily in drugs.
Transactions on the website took place using Bitcoins, a popular form of digital currency that’s sometimes used in the underground.
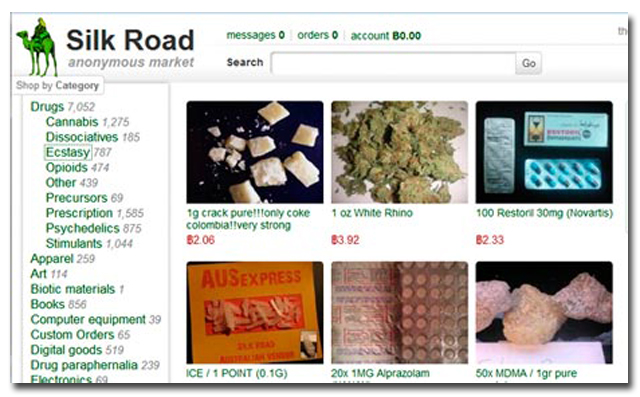
Image: The Guardian
Some types of malware will even use infected computers to harvest Bitcoins–our own Adam Kujawa recently spoke about a new Reveton ransomware sample that harvested the currency.
The Silk Road is also reported to have even sold malware to customers, particularly Remote Access Tools.
At the time of Ulbricht’s arrest, about $3.6 million dollars in Bitcoins were seized.
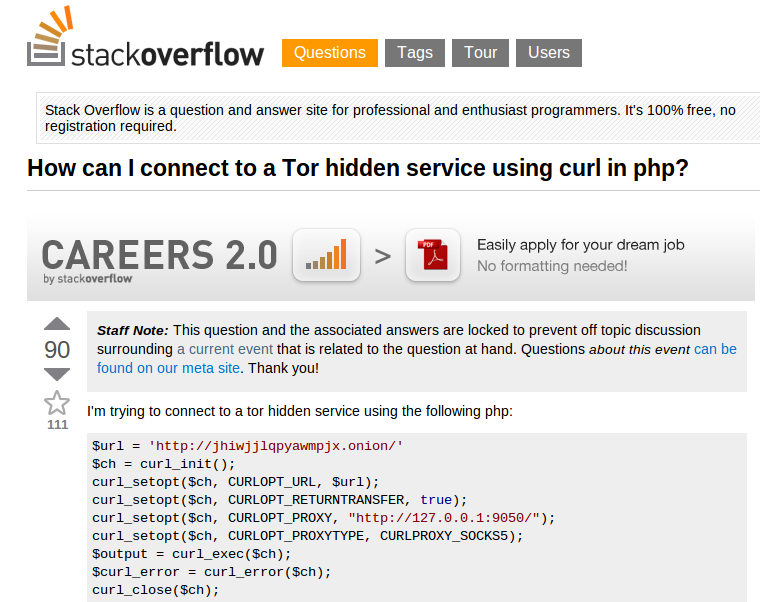
Ulbricht’s arrest was to his own carelessness, accidentally revealing his identify through online communities, one of which was Stack Overflow.
According to Slate, Ulbricht had asked a question on the website using an account under his real name, only to realize the mistake later and change his name to ‘Frosty’.
Ulbricht can also be found on several websites, including LinkedIn, where he’s mentioned as an “Investment Adviser and Entrepreneur “.
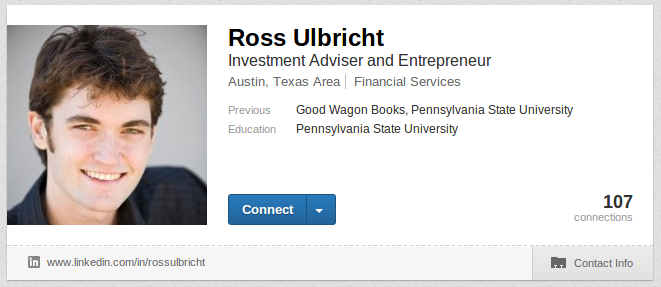
Seemingly natural, Ulbricht’s family and friends suggest these accusations are absurd.
“He’s an exceptionally bright and smart kid,” said his half-brother Travis Ulbricht. “He’s always been upstanding and never had any trouble with the law that I knew of.”
Ulbricht’s widespread social media presence is questionable, having profiles on Google+, Facebook and many more.
This seems rather odd for a leader in an online black market.
Could he have been set up?
Ulbricht is currently being held without bail in San Francisco pending a hearing tomorrow.
_______________________________________________________________________________
Joshua Cannell is a Malware Intelligence Analyst at Malwarebytes where he performs research and in-depth analysis on current malware threats. He has over 5 years of experience working with US defense intelligence agencies where he analyzed malware and developed defense strategies through reverse engineering techniques. His articles on the Unpacked blog feature the latest news in malware as well as full-length technical analysis. Follow him on Twitter @joshcannell









