The criminals behind the infamous CryptoLocker ransomware that encrypts all your personal files are now offering a late payment option, albeit at a higher cost.
Originally, if you did not pay the initial $ 300 ransom within three days, the private key necessary to retrieve the encrypted files would be deleted forever.
Apparently not. The news was first reported on the Bleeping Computer forums early last Saturday.
Perhaps to also thwart AV companies that remove the malware but by doing so break the payment chain, the bad guys have set up an independent online “CryptoLocker Decryption Service”:
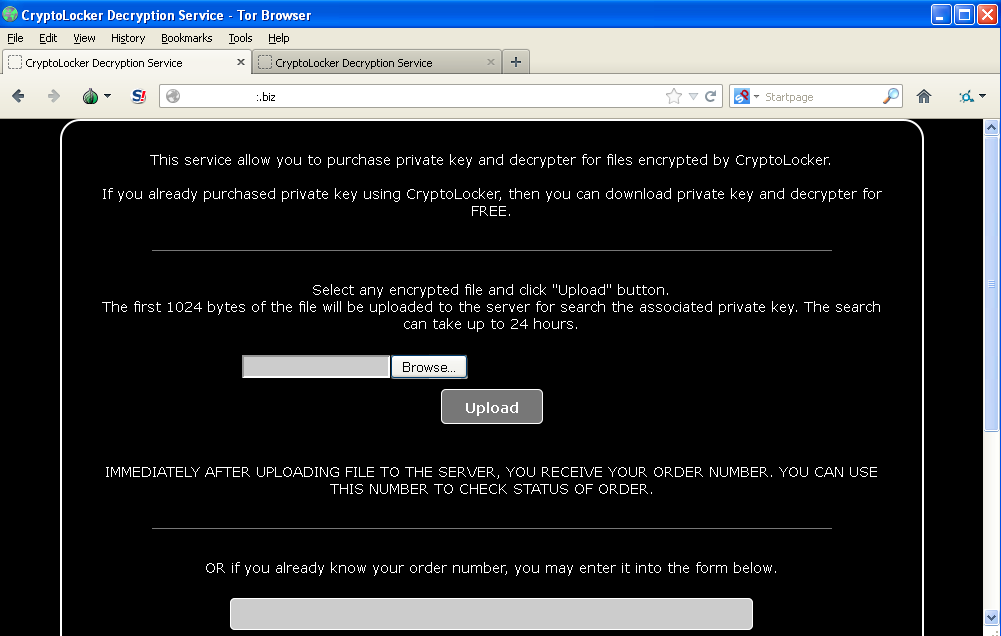
The webpage is hosted on one of the command and control server’s IP address. There is one that belong to AS42655 BESTHOSTING, a web hosting company in the Ukraine well-known for its associations with malware.
In addition, this online “service” page can also be accessed through the ‘anonymous’ Tor network on a “.onion” address, guaranteeing a longer lifespan and protection against DNS sinkholes.
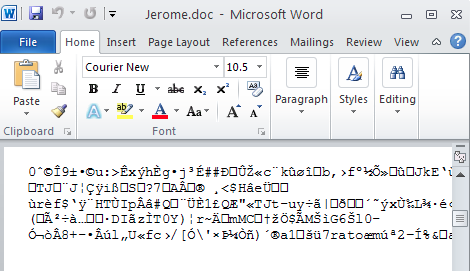
The victims can upload one of their encrypted files in order to find the corresponding private decryption key. The service only accepts files that are encrypted:

Here’s a Word document that had been specifically encrypted by CryptoLocker:
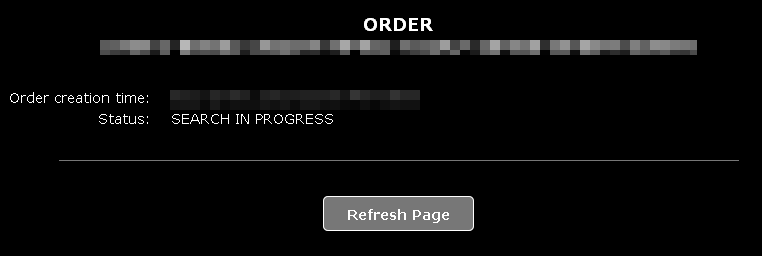
Shortly after the upload, the system starts to look for the decryption key:
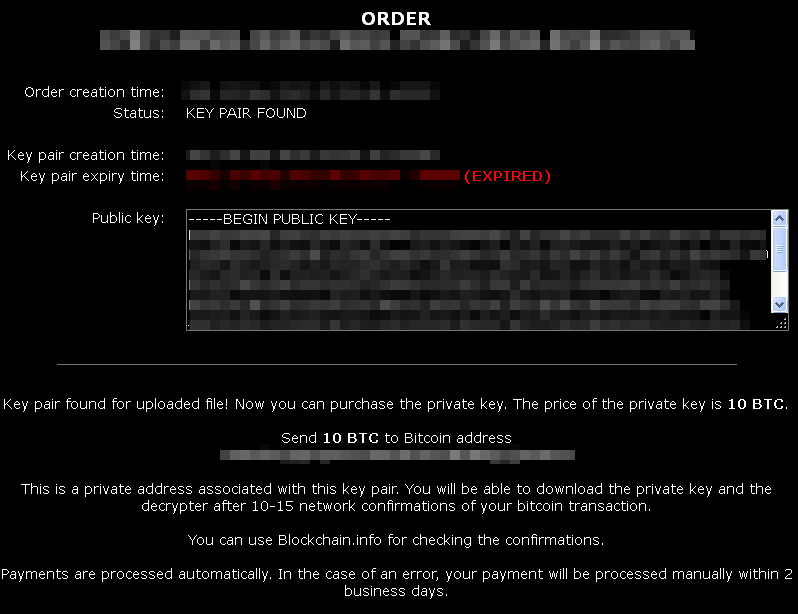
When a match is found, a confirmation page is displayed, along with the payment information: 10 Bitcoins which is roughly over USD$2,000 (the value of 1 Bitcoin being about USD $200).
This is a sharp increase from the original two Bitcoin ransom. However, if the victim has already paid the ransom, the private key will be given “free of extra charge”.
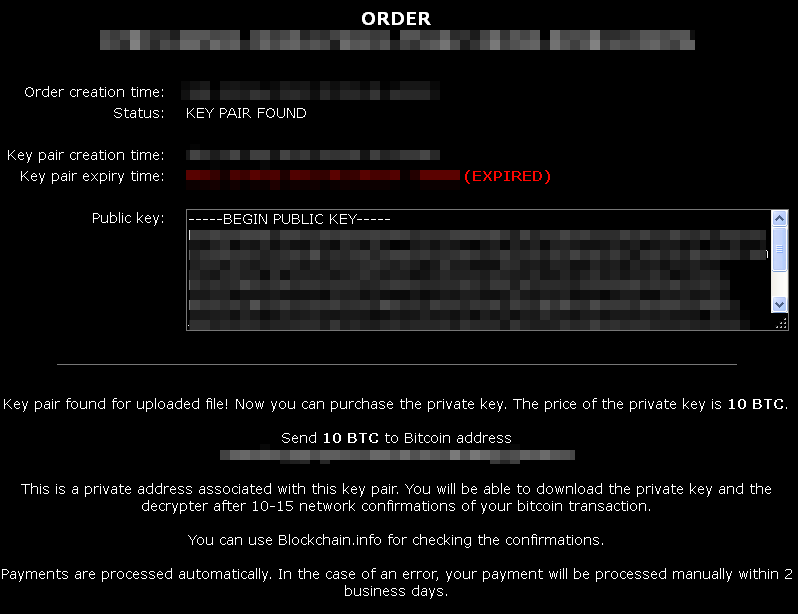
“Payments are processed automatically. In the case of an error, your payment will be processed manually within two business days”.
Where does the money go?
For each victim, a unique Bitcoin address (where the money will be sent) is generated. In fact, even if you upload the same encrypted file twice, you will receive a new Bitcoin address:
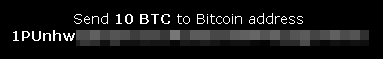
First upload
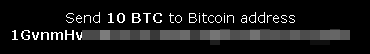
Second upload
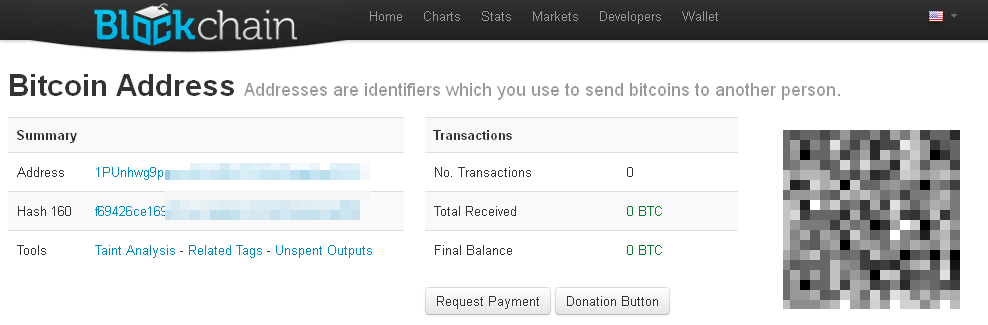
There are online services that offer some form of tracking for a particular Bitcoin address, in particular to see how much money was moved:
This new development is certainly alarming and shows the bad guys are confident that despite the price increase, some people will in fact pay.
Last week, I heard the story of an accounting firm that had been hit by CryptoLocker and found itself in a really bad situation. They either had the choice to pay the ransom or essentially had to shutdown their entire business because their entire customers’ data would be lost.
But even for individuals, the thought of losing something like your family pictures can be heart-breaking.
CryptoLocker is easier and cheaper to block than to heal.
Please exercise extreme caution before opening email attachments (one of the main infection vectors), keep your PC up-to-date, and make sure you have antivirus and anti-malware protection with real-time detection installed.
Also, backing up your important data can be a life-saver. Cloud backups are a good idea because there is less chance of them being affected by CryptoLocker (as opposed to local USB drives you could accidentally plug into an infected machine).
[Edit]: Cloud backups could get compromised if your files are automatically synced; the encrypted files would overwrite the clean ones. You could disable automating syncing and force it to always prompt you: a trade off for convenience but a necessary evil against this threat.
Jerome Segura (@jeromesegura) is Senior Security Researcher at Malwarebytes.