We’ve covered the browser-based ransomware several times before on this blog, ever since it appeared back in July and again each time it evolved.
- FBI Ransomware Now Targeting Apple’s Mac OS X Users
- Ransomware demands additional payment to delete ‘criminal records’
- “Buy $500 antivirus from us,” say cyber-criminals
A tip from security researcher Malekal today got us to look at it again. The main novelty with this one is that instead of using the typical algorithmically generated domain names (i.e. http://fbi.gov.id396126511-5382106440[dot]r0172.com, http://fbi.gov.id517256300-7218768350.z6629.com), it is now hiding behind the anonymous CloudFlare service.
This is not the first time cyber-criminals abuse CloudFlare. The free service not only offers better loading times for websites but also masks their actual IP address, thus making them harder to block.
alert.police-agent-secure[dot]com
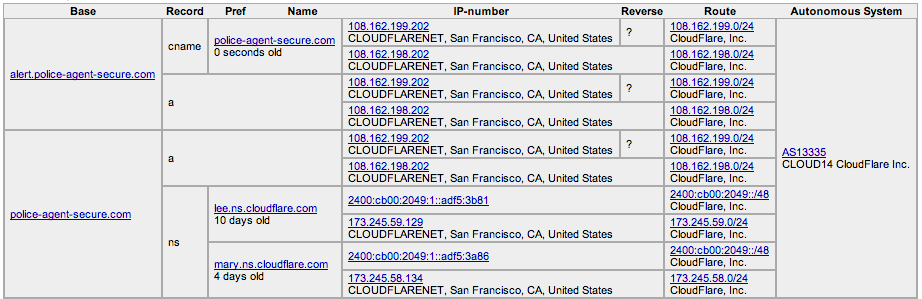
Screenshot courtesy of Robtex.com
Another interesting thing about it is the payment process. Contrary to its old cousin where you could enter the same voucher number multiple times, this version actually logs them into a database.
Before submitting the voucher’s number, a quick validation is done locally with some JavaScript and regular expressions:
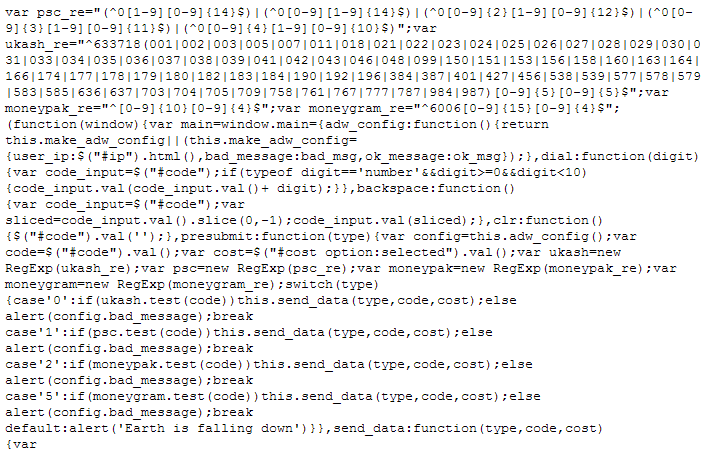
The previous version of the brower-based ransomware had a much more simplistic check. For example, it only made sure that the voucher’s number was 14 digit long.
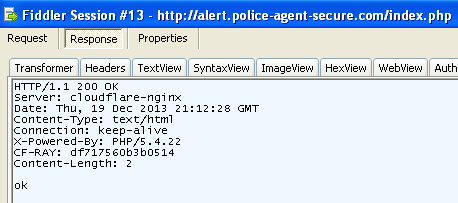
If everything looks good, a POST request with the user’s voucher ID, IP address and the type of payment (MoneyPack or MoneyGram) is sent to the server:
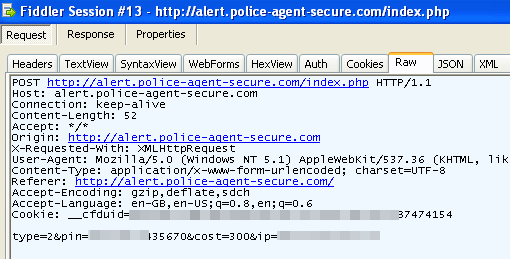
The server validates the voucher and sends back the response to the browser.
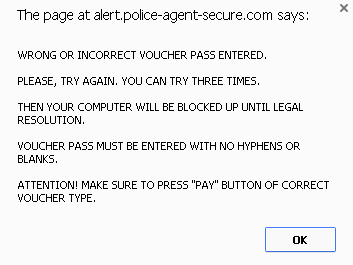
Case #1: bad voucher
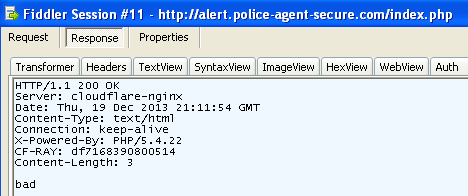
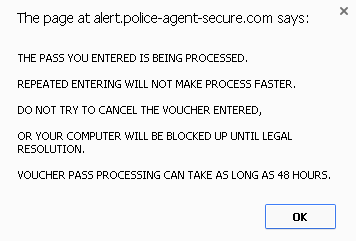
Case #2: good voucher
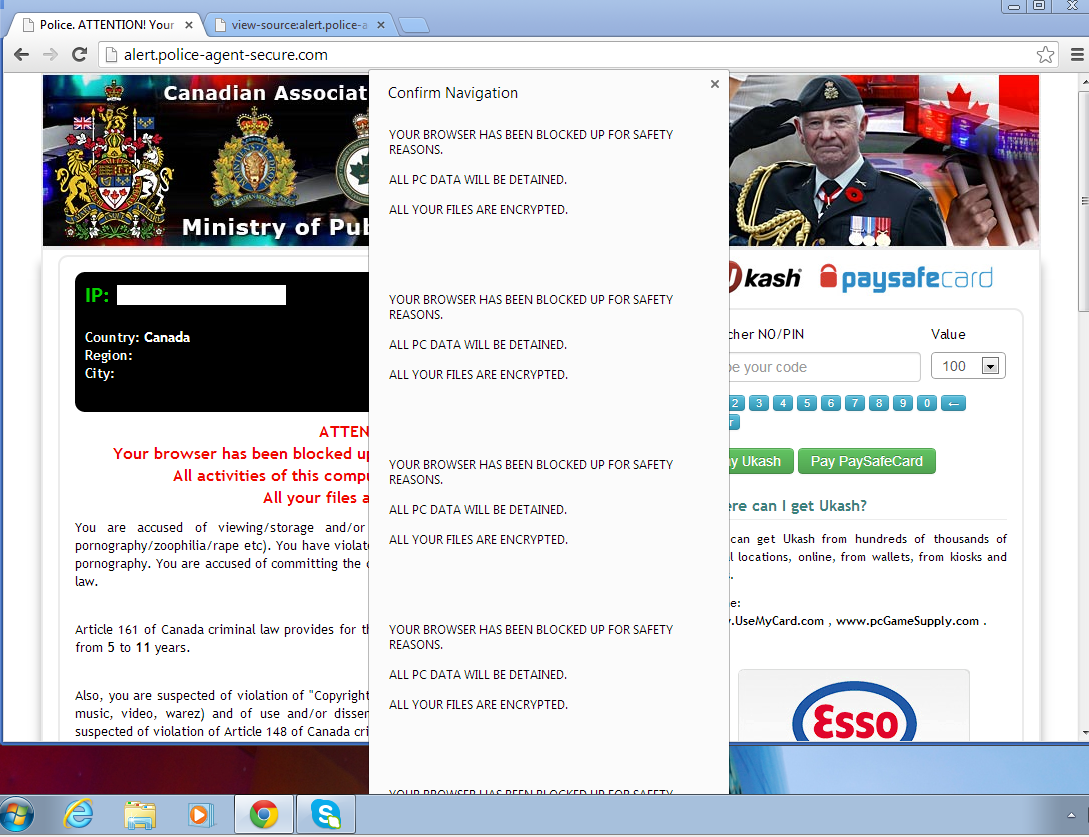
Most browsers are capable of exiting the fake “lock-down” but yet the bad guys are still using all sorts of tricks to annoy the end-user such as an extra-long alert window:
We’ll keep an eye on this developing story.
Hat tip to Steven Burn for passing on the information.
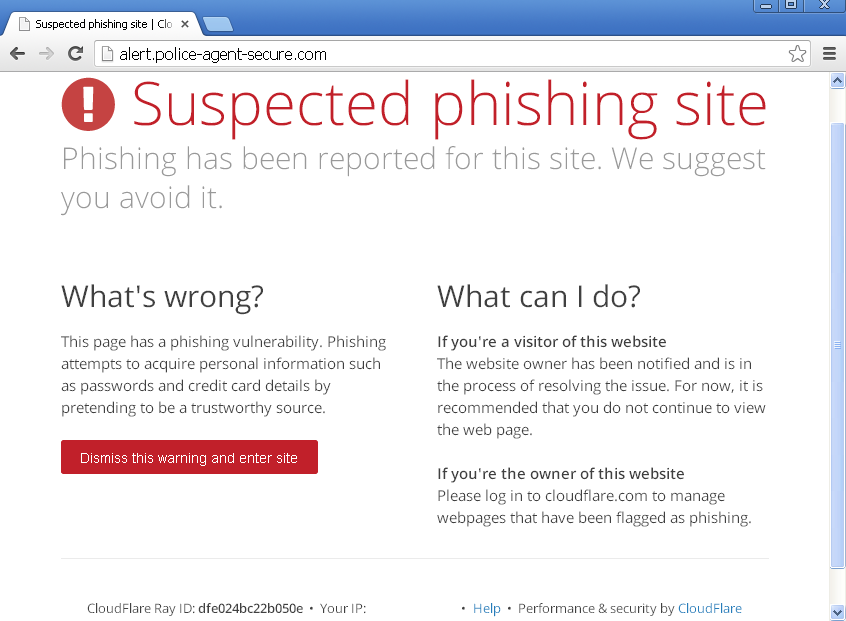
Update: we’re pleased to see that CloudFlare has taken prompt action and is flagging this domain as a phishing site:
—
Jerome Segura (@jeromesegura) is a senior security researcher at Malwarebytes.










