You can hardly browse any website without encountering some type of advertisement along the way, typically in the shape of a top or side banner.
While you may be slightly annoyed to see the same products being pushed, the last thing you might probably imagine is that some of those adverts could actually carry the seeds of a malware infection. This is known as malvertising.
Compromising websites that have high traffic by finding a vulnerability in their underlying software requires more efforts than simply attacking their ad network(s) whose security practices might not be on the same level.
In fact, many advertisers contract out to third parties, which in turn may outsource to others, thus creating an insecure chain of intermediaries where one weak link can take everybody down.
Case in point, I found a malicious advertisement involving a popular ad network known as Propeller Ads Media:

One common misconception with malvertising is that you must click the ad in order to get infected. Although it can be true, we will see in this example that the simple fact of the ad loading up in the browser can be enough to infect your PC.
To better understand how malvertising works, let’s take a look at a typical ad:

The underlying structure usually consists of:
- an image
- a destination URL
- a banner, affiliate or campaign ID (for tracking purposes)
All this information is visible in the page’s source code:
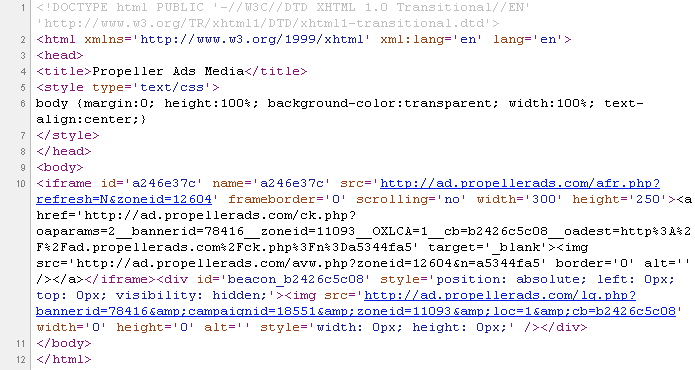
Now let’s take a slightly different ad that directly links to a third-party affiliate URL (instead of the major ad network itself). This is an example where the major ad network (here Propeller Ads Media) is taking a risk because it no longer is in full control.
So here, the ad calls to etoroaffiliate.com to retrieve the additional content:
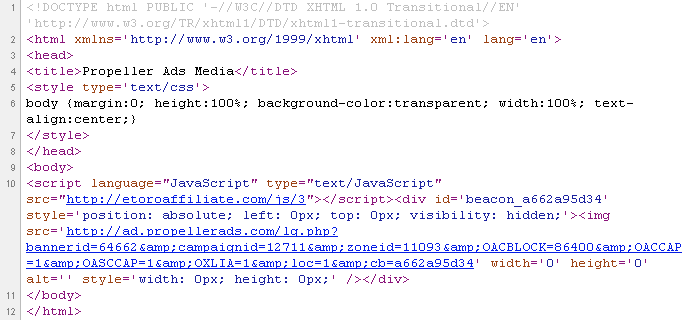
etoroaffiliate[dot]com/check.js is a piece of JavaScript that determines the user’s configuration before redirecting to the ad itself:

The source for this is:
Here comes the malvertising
In our case, instead of the regular ad (as shown above), a malicious iframe to a .biz URL is inserted:
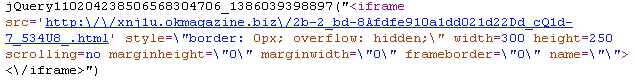
You may have been browsing your favourite site when all of the sudden one of the ads is going to cause mayhem in your computer and you most likely won’t know how this happened.
The insidious thing about malvertising is that an ad can turn naughty for a few minutes and then get back to being benign. Or, along the same lines, malvertising can affect certain users in a particular country and only during the week-end. You now understand why this is such a tricky thing to deal with.
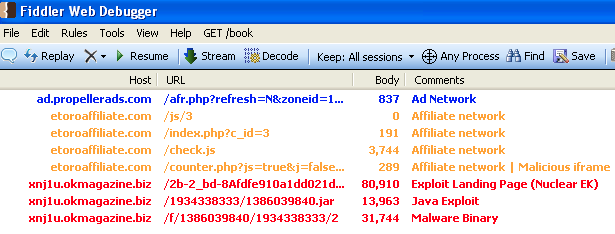
This story does not end well if your computer isn’t up to date. In our example, a Java exploit is served quickly followed by a malware binary.
The malware is detected by Malwarebytes Anti-Malware as Trojan.Agent.
Despite being surreptitious, malvertising can often be traced back in traffic captures and therefore shines light on high-profile websites and big ad networks. This type of publicity is not good (New York Times hit by malvertising) for either of them but when it comes to identifying what exactly happened (was it a rogue affiliate advertiser?) things can get tedious.
The very nature of the ad business is that everything moves fast with a myriad of affiliates that come and go. Certainly, not all ad networks are the same and some do a better job at blocking the bad guys.
But when you see YouTube itself being affected by malvertising, you know that this is a difficult problem to tackle and that there will always be some bad apples in the mix.
Once again, endpoint protection remains crucial to block these attacks. Malwarebytes catalogs notorious ad networks involved malvertising. Additionally, our Anti-Exploit product is an effective solution against malvertising as it will block malicious code that attempts to load malware on your machine.
For those who truly despise ads, there are web browser plugins such as AdBlock or AdBlock Plus that will prevent ads altogether, which by the same token would block malicious ads. That is so long as AdBlock’s policy on “acceptable ads” doesn’t become too lax!
However, your web browsing experience might be quite different if you chose to block ads. For many website owners, ad revenue is their bread-and-butter and they see such visitors as cheaters or stealers.
In fact there is even a WordPress plugin (No Adblock) that will prevent those that have AdBlock enabled to be able to view those website running that plugin.
While malvertising is the bigger threat, some ads are notoriously misleading end users into downloading bundlers and other Potentially Unwanted Programs. (You can read our policy about PUPs here).
The following ad from Propeller Ads Media shows a blatantly false message: “Your system does not support fast downloads and streaming”:

Downloading the “free-plugin” results in an overdose of pop-ups, registry cleaners, system optimizers and even more scary warnings:
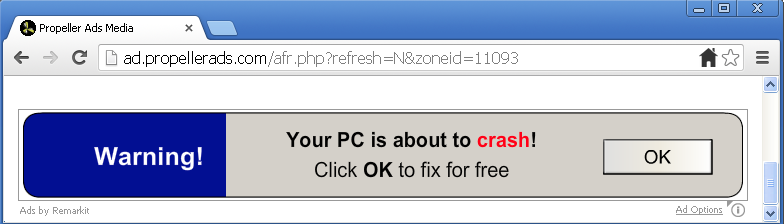
Malwarebytes Anti-Malware detects the Setup.exe file as PUP.Optional.DomalIQ.A and will thoroughly clean-up your system of all the other junk that may have come along.
One the one side you have the silent infection (malvertising) and on the other you have the social engineering (scare tactics). If you didn’t like ads before, you now have some more reasons to despise them!
_________________________________________________________________
Jerome Segura (@jeromesegura) is a senior security researcher at Malwarebytes.










