In an article posted today by Mohit Kumar of the Hacker News, a proof of concept was reported that proves the technology exists for malware to actually communicate between non-connected systems via inaudible signals sent from one system and received by the other.
The PoC, written by German Researchers Michael Hanspach and Michael Goetz, was originally published in the Journal of Communications last month.
This concept has most recently been brought into the light due to the controversy behind “BadBIOS”, a highly advanced and dangerous malware, currently only encountered by one highly regarded researcher.
In the paper, the researchers describe using a system’s built-in sound card and microphone to transmit information from one end (the client or application installed on the target system) to the other (the server), if both systems are infected and are within 60 ft. of each other.
The purpose of this type of research was to determine if systems that are completely severed from the internet or any other public facing systems (i.e. airgapped) are susceptible to attacks.
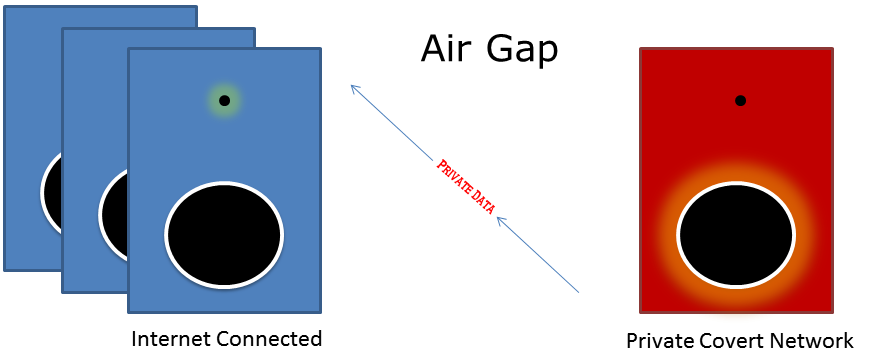
While I personally don’t think remote infection would be possible using this method, if an attacker were to use something like an infected USB that was plugged into an airgapped system, it could automatically install the malware and begin sending or receiving data.
Researchers measured the transmission speed to be roughly 20 bits per second (bps), which averages out to two keyed in characters transmitted every second. The scenario postulated by the researchers involved a keylogger sending data back to a remote attacker, at 20 bps, the entirety of this blog post would take 20 minutes to send.
However, that doesn’t take into consideration data reliability. With all types of potential interference factors, like cell phones, televisions and other electronic emissions, I think that expecting a clear and reliable feed of data outside of a lab is unlikely.
My theory is that this technology could be used to provide targeted malware a means of external communication for contact with a command and control server. The infected system would receive commands from the server and assuming that the initial infection on the covert system was via USB drive, perhaps the malware could store stolen data on the USB.
That data would be sent out later once the USB is able to plugged into an outward facing system. This is similar to how Flame worked when extracting sensitive data from closed off networks.
This scenario is entirely based on having previous intelligence gathered, therefore it would be highly targeted and every command sent from the control server would need to follow a previously created plan. In other words, it’s unlikely that the average user will ever need to worry about this type of threat.
None the less, it’s pretty interesting.
Thanks for reading and safe surfing! DFTBA!
——————————————————————————————————–
Follow Adam Kujawa and all of his zany opinions on Twitter @Kujman5000











