What is it? A website offering up fake browser updates that take an end user down different roads they wouldn’t travel with a genuine browser update.
Why is it a problem? Any message asking end users to update browsers to ward off security issues can cause problems both at home and in the workplace. Neither “Relative who knows about computers” or the stressed IT guy from the fourth floor wants to waste time rolling back / uninstalling / deleting things from the target PC.
Do we detect it? Yes, as PUP.Optional.iBryte
I came across a fake browser update site doing the rounds located at
newbrowserversion(dot)org
which has pages for Chrome (C), Firefox (F) and IE (I) users.
Interestingly, it seems we may have wandered onto the scene in the middle of somebody setting things up, as opposed a “finished” distribution. Almost everything is in place, apart from the bit where the people behind it can seemingly make any money from any installs.
Here’s what you can expect to see on each of the three pages.
Chrome:
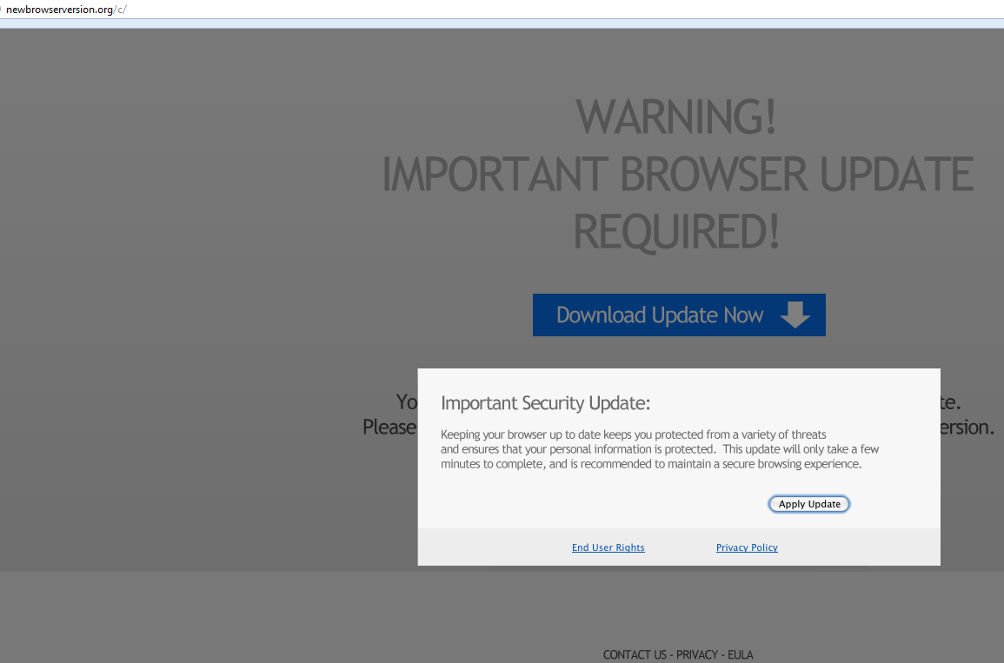
Firefox:
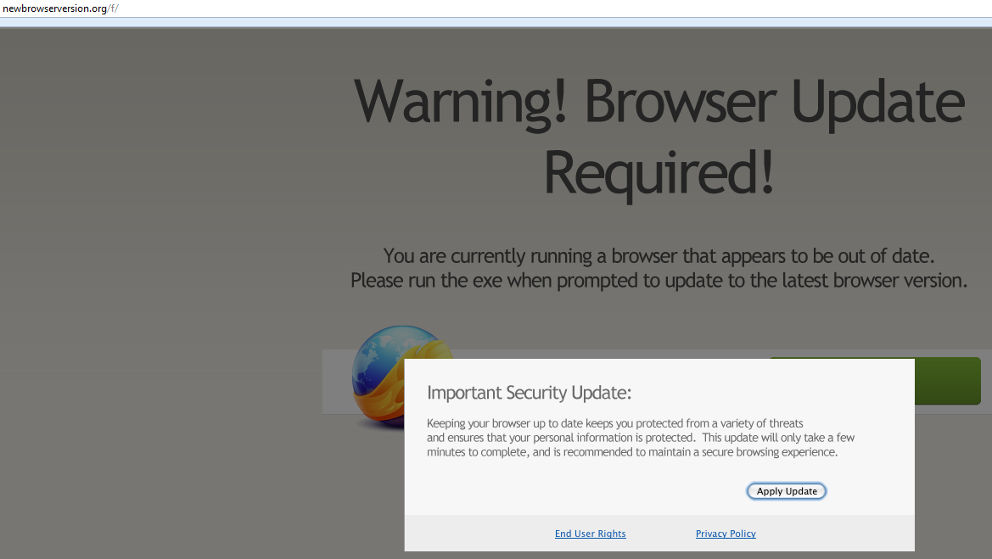
IE:
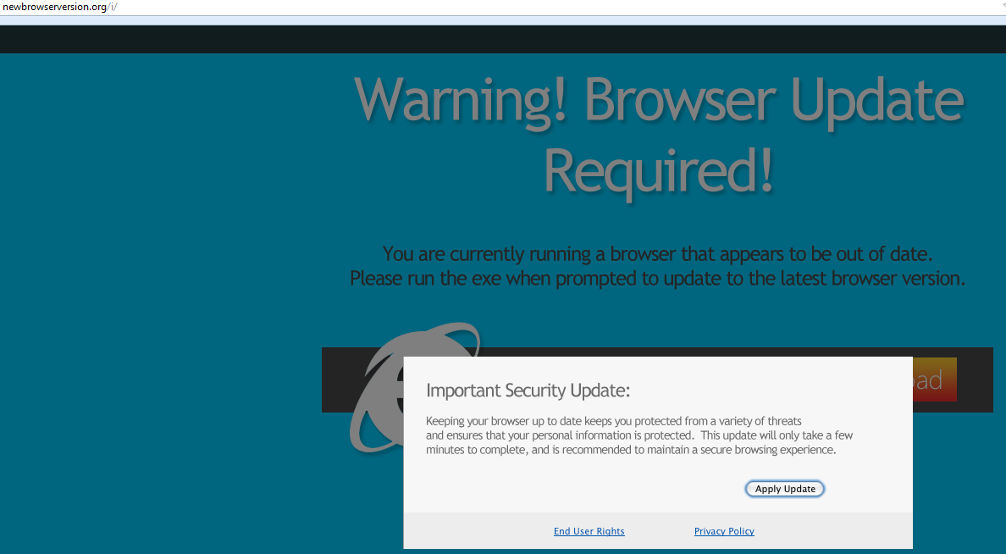
Regardless of page viewed, they all say the same thing:
“Warning! Browser update required!
You are currently running a browser that appears to be out of date, please run the exe when prompted to update to the latest browser version. Keeping your browser up to date keeps you protected from a variety of threats and ensures that your personal information is protected. This update will only take a few minutes to complete and is recommended to ensure a secure browsing experience”
Despite having notifications on the box which reads “End User Rights” and “Privacy Policy”, clicking anywhere on the box will result in triggering a download. Should the end-user run the executable file (and all three have a different MD5) the install procedure kicks into gear.
Sort of.
We’re presented with the standard splash screen, and one would expect to see various offers, programs, maybe the odd toolbar.
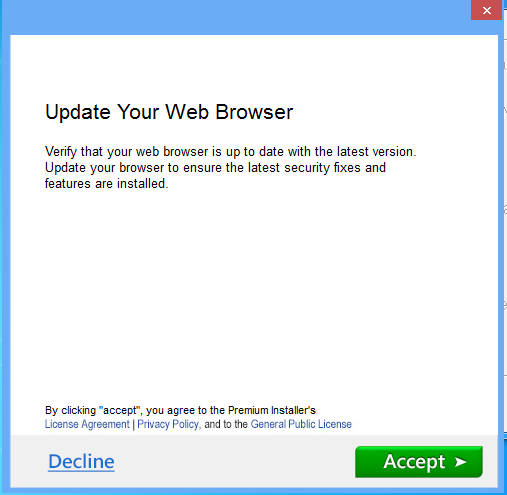
Except…
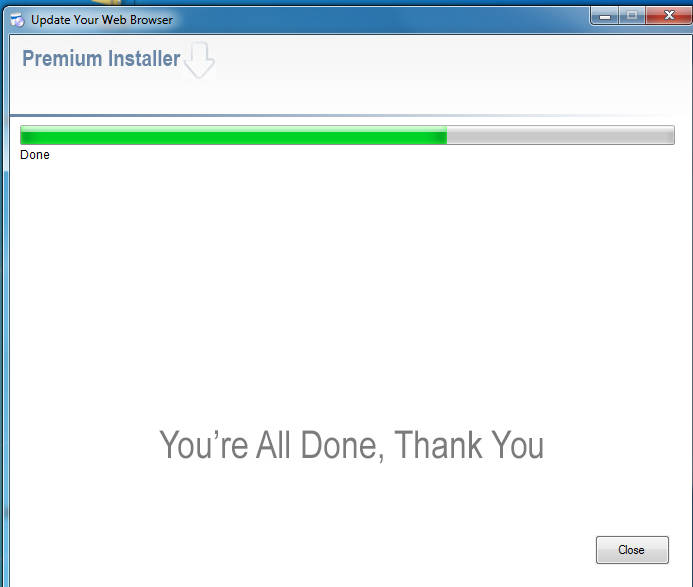
Nothing. No offers mentioned during the install, nothing of note once you’re told that everything is finished.
What does happen, is that you end up with a program in a temp IE directory that launches a browser window after install.
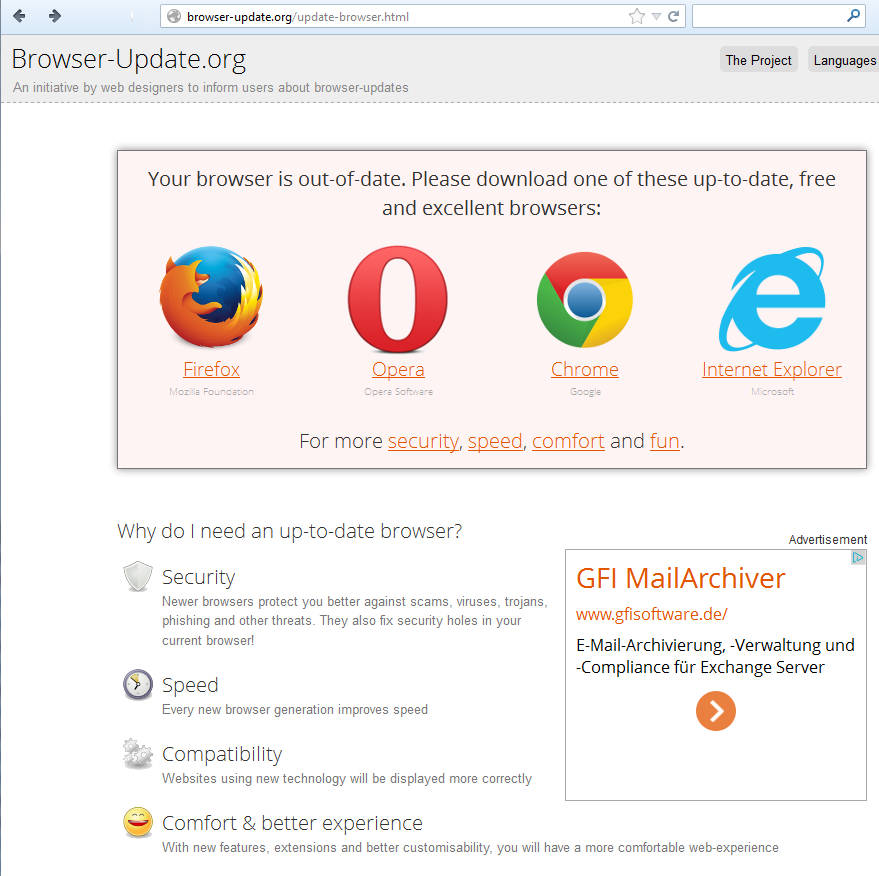
The above site doesn’t do anything other than provide four links to the (legitimate) websites / download locations of the four browsers listed.
In a nutshell, at time of writing the end user has visited a fake browser update website, installed a fake browser update, gone through an install routine and finished off by being presented with…a website telling them to go to places they could have reached without all of the above.
What this is clearly missing, is the affiliate generating cash for the creator. That would be provided by what one assumes is the currently MIA installs which the end-user would have witnessed during installation. Whether something else is added to this remains to be seen, but the starting point for all of this – a website claiming that an “Important browser update” is required – is something that can be ignored.
If you want to check the update status of your browser, rely on the browser itself rather than third-party websites offering up random downloads. More often than not, your browser will tell you about updates by clicking into “Help” and / or “About this browser” options in the various settings menus.
Warnings about browser updates should always be taken seriously, but we need to get into the habit of taking this warnings from the browser itself and not whatever randomly passing content happens to drift by inside the browser window.
Christopher Boyd (Thanks to Adam @Kujman5000 for additional testing)










