It’s not uncommon for the malware of today to include some type of built-in virtual machine detection.
Virtual Machines (VMs) are an essential part of a malware analyst’s work environment. After all, we wouldn’t want to infect our physical–or “bare-metal” computers–to all the nasty things that malware can do. Instead, we can place the malware in a VM environment (VME) and easily “refresh” our VM after an infection as occurred.
Since malware writers are well aware of this, they often target virtual machines using various techniques. Some of these techniques are primitive or simplistic, and only read registry key values. However, there are other techniques that operate at the machine-language level, and are more difficult to detect.
Let’s observe a practical example. Below is code from an unpacked Dll Ransomware that looks for VM-related strings in your computer’s display device.

(click to enlarge)
To make analysis easier, it would be very easy to patch this check and remove it. For a more permanent remedy, though, there are other options, to include uninstalling VMware Tools. I have already done this on my Sandbox VM. Below is the output of the same Ransomware when it checks my display
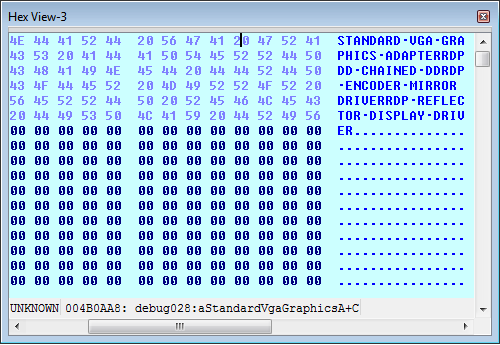
As an analyst, however, it will not always be so easy to determine if VM-detection is occurring. Hardening your VM can be a lengthy process, and can involve a lot of work. In some cases, you may need other tools for hiding processes, files, and registry keys that are created by your VM.
Lastly, if you use VMware, adding these options to your POWERED OFF .vmx file will be of great value if you perform malware analysis.
isolation.tools.getPtrLocation.disable = “TRUE” isolation.tools.setPtrLocation.disable = “TRUE” isolation.tools.setVersion.disable = “TRUE” isolation.tools.getVersion.disable = “TRUE” monitor_control.disable_directexec = “TRUE” monitor_control.disable_chksimd = “TRUE” monitor_control.disable_ntreloc = “TRUE” monitor_control.disable_selfmod = “TRUE” monitor_control.disable_reloc = “TRUE” monitor_control.disable_btinout = “TRUE” monitor_control.disable_btmemspace = “TRUE” monitor_control.disable_btpriv = “TRUE” monitor_control.disable_btseg = “TRUE”
These “undocumented” options are from a research paper done several years ago, but are still useful today in preventing some VM-detection techniques. Please note however, that this will break some VM functionality, as these options sever the communications channel between your host machine and guest VM.
_________________________________________________________________
Joshua Cannell is a Malware Intelligence Analyst at Malwarebytes where he performs research and malware analysis. Twitter: @joshcannell









