Update (May 1, 2014): Microsoft has decided to release an out-of-band security update for CVE-2014-1776 and, in a surprising move, is also issuing one for the not-so retired Windows XP.
We have made the decision to issue a security update for Windows XP users. Windows XP is no longer supported by Microsoft, and we continue to encourage customers to migrate to a modern operating system, such as Windows 7 or 8.1. Additionally, customers are encouraged to upgrade to the latest version of Internet Explorer, IE 11.
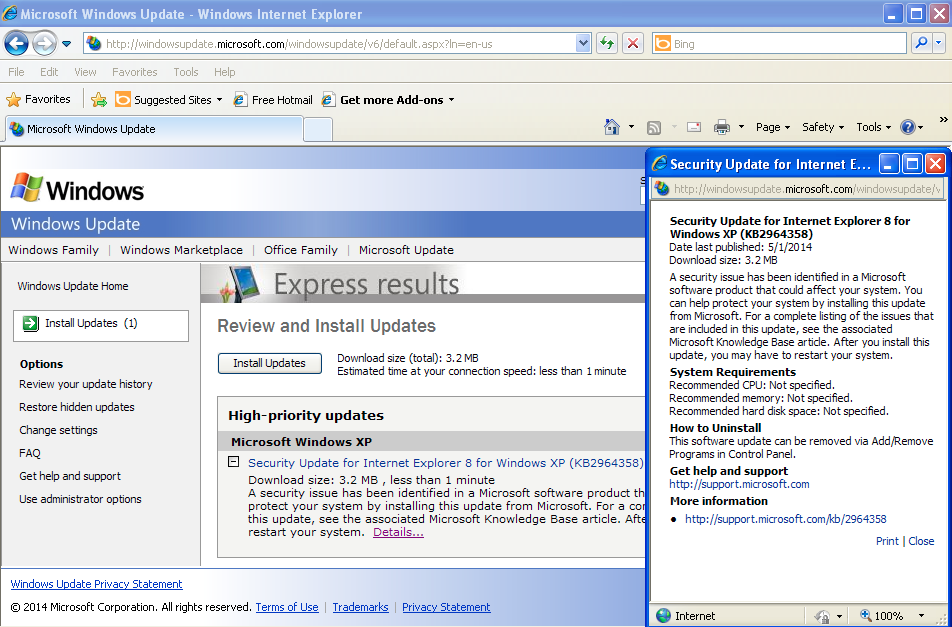
– –
Original story:
Security researchers have discovered a new vulnerability affecting Microsoft Internet Explorer from version 6 to 11 on practically all the different Windows operating systems, including the latest, Windows 8.1.
Microsoft issued a security advisory for this flaw (CVE-2014-1776) which could allow remote code execution simply by browsing to a compromised website.
The advisory does not mention Windows XP in the list of systems affected, since it has officially been retired and is no longer supported.
But since Internet Explorer 6, 7 and 8 are also exploitable, this Zero-Day is not only bad news for everyone, but more so for XP users who will not receive a patch from Microsoft.
Details on the vulnerability are still scarce, but security firm FireEye says that this is another move from the same gang that already exploited use-after-free vulnerabilities in targeted attacks.
To mitigate this attack, users have several options:
- Run Internet Explorer in “Enhanced Protected Mode” (IE10 and IE11).
- Disable the Flash Plugin in IE (this Zero-Day uses the Flash Player to exploit IE).
- Download and install Microsoft’s Enhanced Mitigation Experience Toolkit (EMET). Note that earlier versions of EMET (<=3.0) are ineffective against this Zero-Day.
- Switch to a different browser (this is especially true if you are running XP).
- Install Malwarebytes Anti-Exploit, a non-intrusive and proactive shield for browsers and applications against known and unknown vulnerabilities (if you run Anti-Exploit, you do not need to run EMET at the same time as they may conflict with one another).
This is the first ‘official’ Zero-Day post Windows XP’s End of Life and it certain won’t be the last.
While as far as we know this Zero-Day has only been used in very targeted attacks, you can count on seeing it getting integrated into an exploit kit very soon, meaning a wide distribution to potentially millions of computers.










