Ah, Facebook hacking. It’s one of those things security folks generally warn people against due to its questionable legality regardless of one’s reasons for doing so, yet many continue to go out of their way to look for hacking tools and services online.
Being in the industry, I’ve even heard of stories where users ask colleagues to hack accounts for them as a favour. They were politely turned down, of course 🙂
Whether one genuinely lost their Facebook account password or not, it’s never a good (nor safe) idea to entrust matters to hacking, cracking, or sniffing. There’s almost always a catch. It’s still best to contact Facebook support directly for password retrieval.
Facebook hacking is a topic we’ve seen written over and over and over.
We’re putting a spotlight on it again to make our readers aware and hopefully help curb the demand of account intrusion.
I took a peak at a bit.ly URL related to a hacking tool that is shared around social networking sites and found that it has been accessed by hundreds of thousands of users.
Recently, we discovered a hacking-as-a-service type of site that, aside from claiming it can help users sniff out passwords from accounts of their choosing, it also gives them the capability to view chat logs of others in their network and extract locally stored Facebook account keys from Google Chrome.
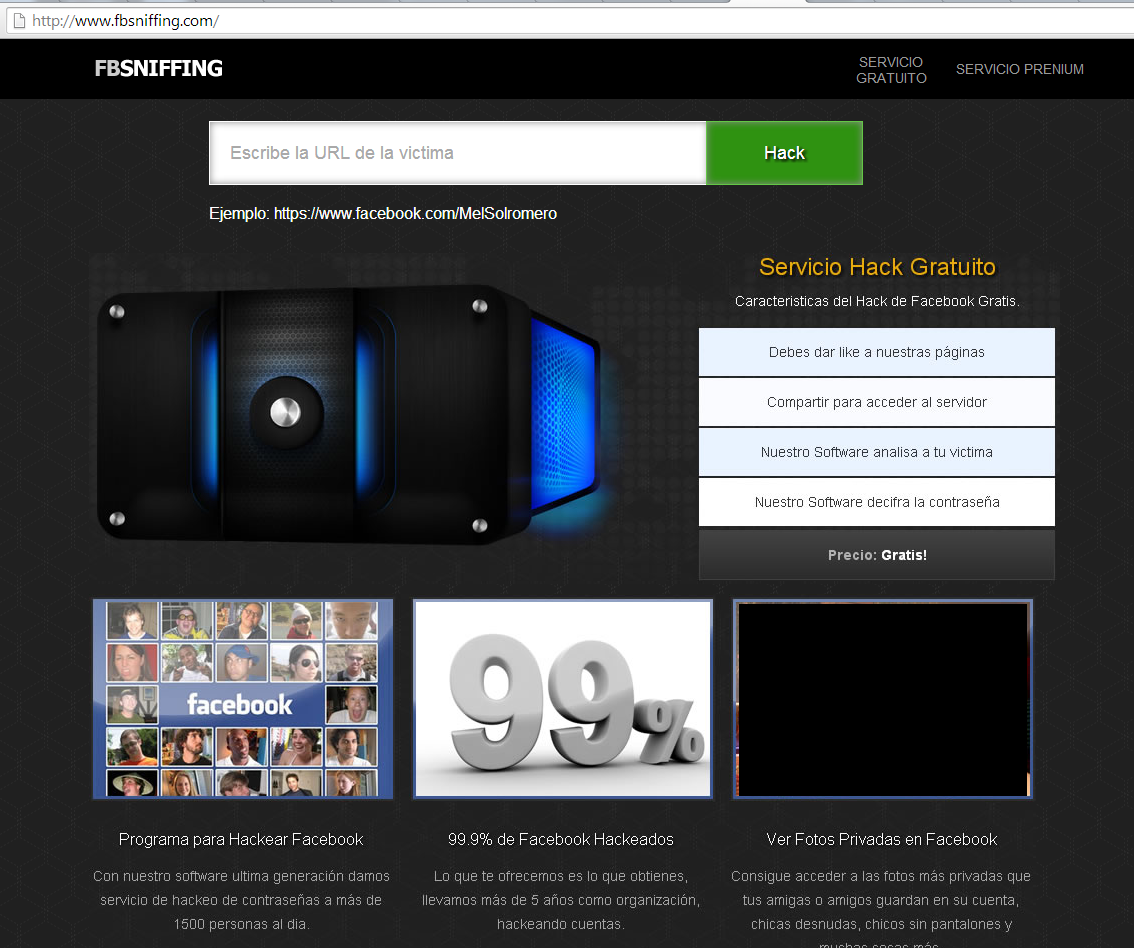
FBSniffing(dot)com, as you can see above, appears sleek, passably professional-looking, and may be convincing enough to get someone to actually try them out. Users who speak Spanish are the main targets of this bogus service.
Once users enter a Facebook URL to the text box provided and click “Hack”, they are then directed to a results page that looks like this:
The predictable results
It displays the target user’s avatar, name, Facebook email address, and it’s supposed user ID, which is actually just a fixed number value. From here, users can click the “Entrar a Facebook” (“Enter Facebook”) button where they are then directed to this page:
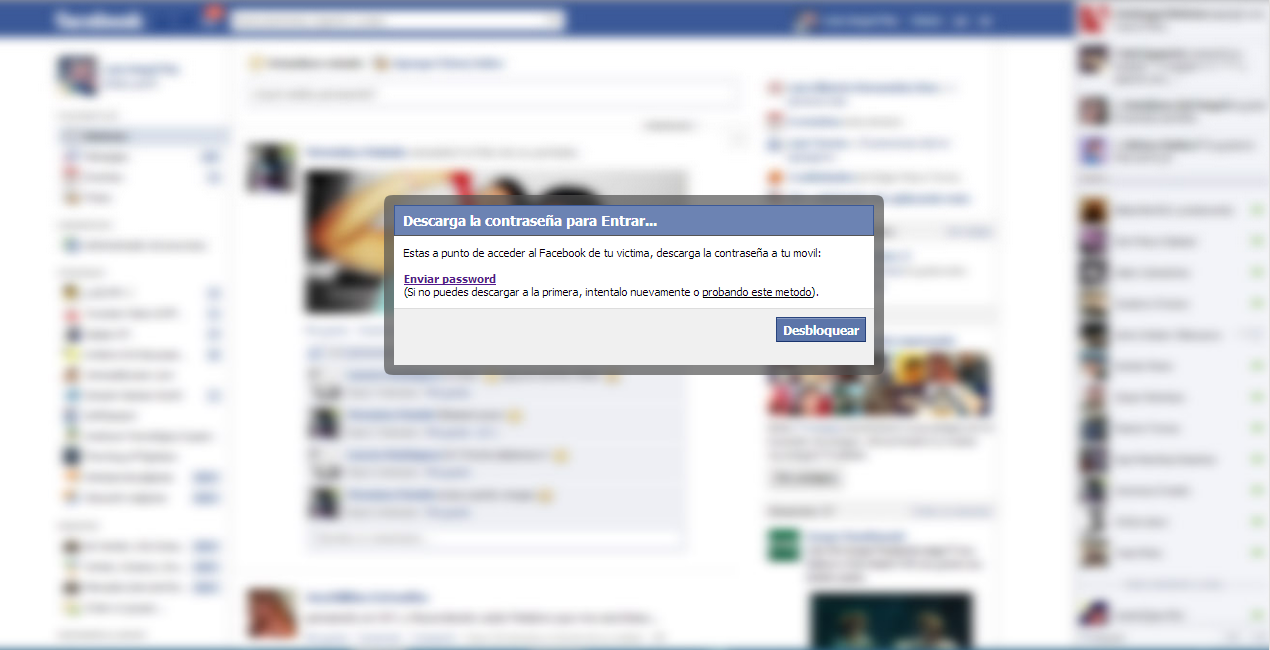
“Claim your password here”
This is where users can download the password they want from the tool. Supposedly—until the page starts to ask them about their mobile number and unique PIN code that the site sends over as “a form of verification.”
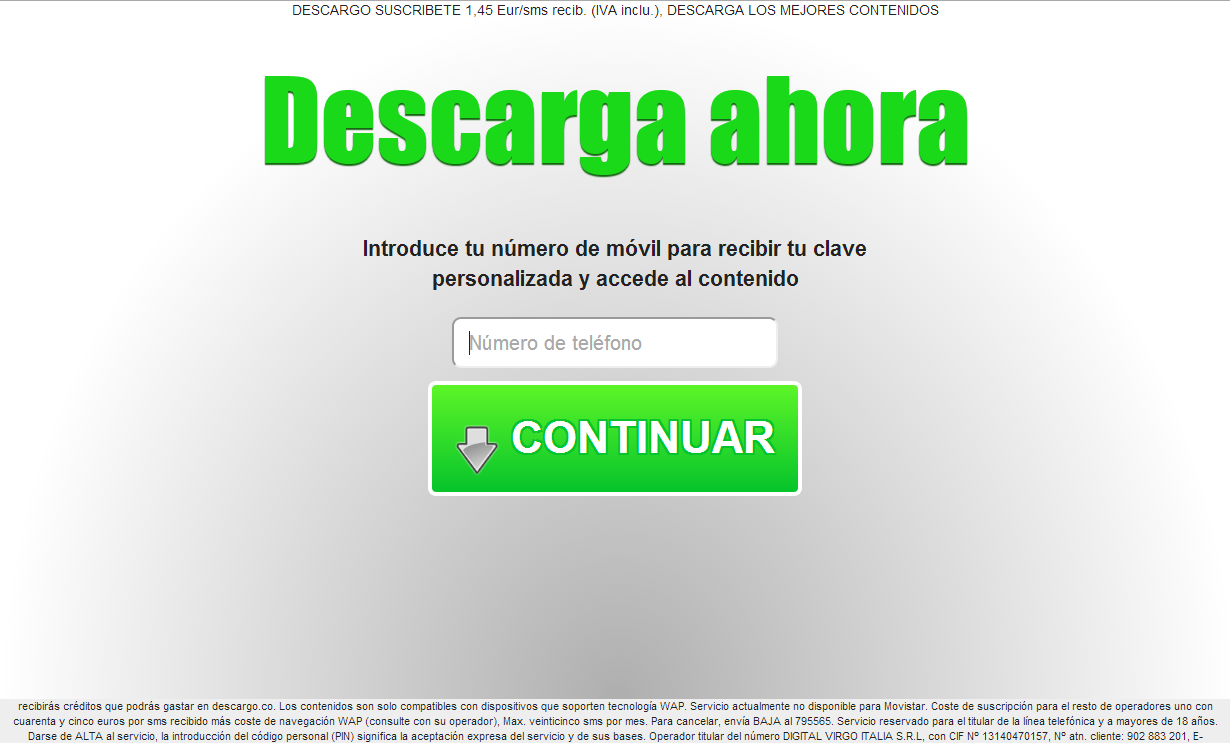
Put your mobile number here…
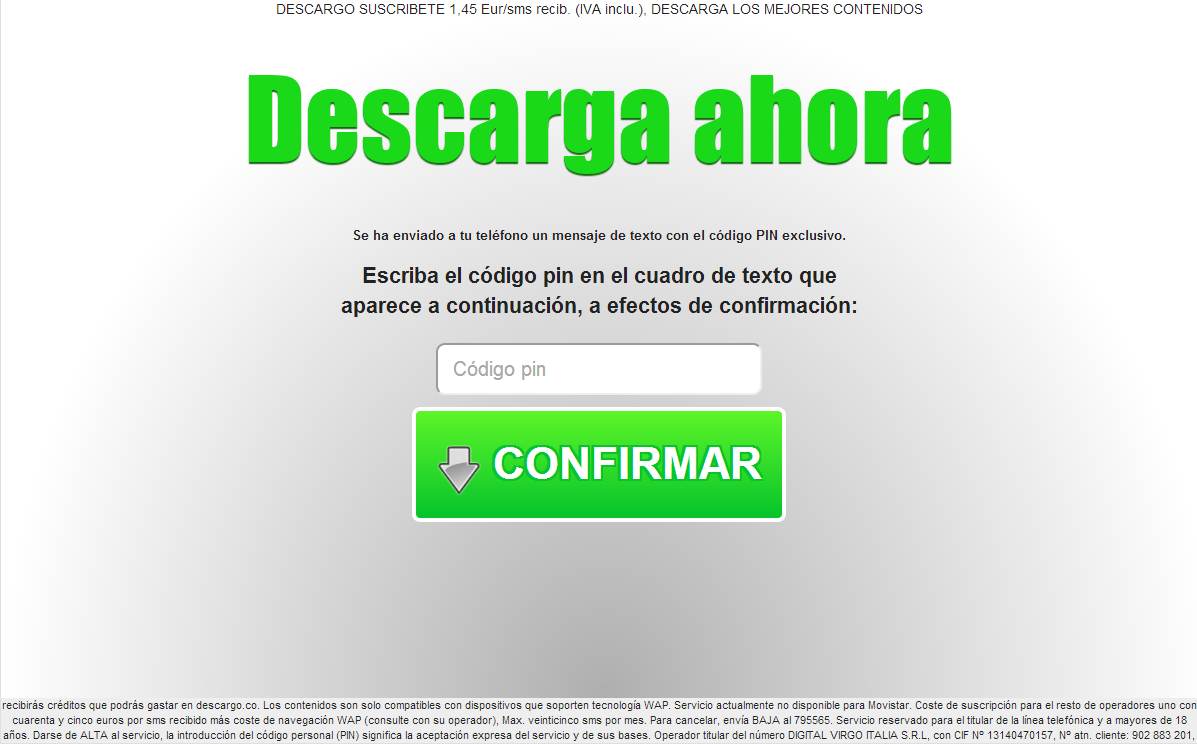
…and put the PIN there…. Done, right?
Not only will users end up not getting what they expected to get, they will also be subscribed to a mobile service (with a fee) that they never wanted or asked for.
May this bogus site serve as a reason for users considering trying hacking not to do it.
Delving into the business of shady fellows who’re only waiting for users to fall into their lures will cost more for users than the tool and its developer or the entity offering the illegal service.
Jovi Umawing










