I wrote about bundles in the past, having investigated complaints from a forum user that we had installed undesirable software, along his copy of Malwarebytes Anti-Malware.
Our stance on PUPs, or Potentially Unwanted Programs hasn’t changed, in fact many businesses are now aligning themselves with us in our stance on this type of software and the practices of their creators.
I was personally involved in explaining what behaviors earn programs the PUP classification. You can read about our selection criteria here: https://www.malwarebytes.org/pup/
I am proud of being employed @ Malwarebytes, and I cannot convey how great it feels to meet someone who expresses their gratitude when I tell them I work there.
They often tell me how they tried many products to clean theirs or a relative’s computer, and ours was the only successful one. This happens a lot!
This is why when I see companies use our good name–a good name created from the effectiveness of our product, not through clever marketing ploys–to tack on PUP’s, I get pretty upset.
I get even more upset when I realize that the users who are downloading our program in this manner are probably looking for a solution to a malware problem and are unwittingly inviting more questionable software onto their PC’s.
As always, you can download Malwarebytes Anti-Malware here.

Bad pup is still being bad.
This is still the best place to get our software, as you’re guaranteed to get just what you want.
We come across bundles that include Malwarebytes Anti-Malware all the time. This is a practice we specifically forbid in our EULA.
“Malwarebytes has clearly stated that you may not “transfer, sublicense, lease, lend, rent or otherwise distribute the Software to any third-party.”
Not long ago, these shady bundling practices came up in a discussion I was having with a friend. I am a firm believer in patching the end-user and my friend needed help installing a program. This particular application was only available as part of a bundled package.
I carefully explained how to navigate through the numerous menus of the installer, unselecting this and unchecking that. This was a tedious process that proved to be quite tricky…
Eye-Opening Discussion
After completing the installation, my friend commented that whoever had designed their installer should be canned, as it was exceedingly difficult to navigate. His exact words were: “Wow, I would never have gotten that right, there were so many options!”
I then proceeded to explain to my friend that no, their UI designers were in fact very good at what they did, and probably rewarded for making the install procedure precisely as it was.
I explained that these byzantine menu selections are not the result of bad UI design, as he initially thought, but are in fact very carefully and deliberately built, using in-depth knowledge of human psychology. It is a completely intentional and deliberate decision on the part of the PUP peddling companies to have giant green “DOWNLOAD” buttons peppered throughout the download page, although only one of these point to the actual desired software.
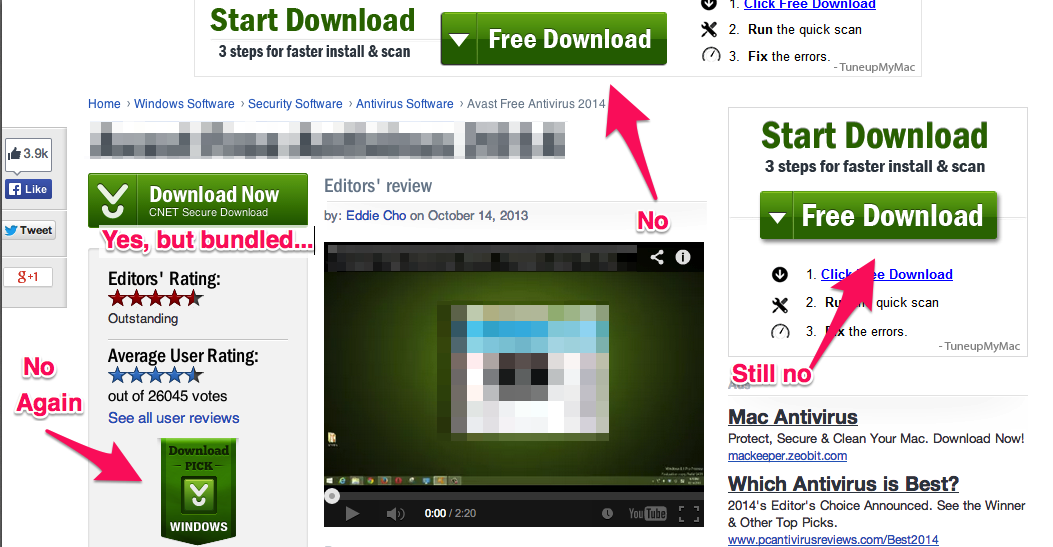
This is done in order to generate additional downloads that rely on a user mistakenly pressing the wrong download link.
A certain percentage of users, tricked into installing PUP’s won’t bother uninstalling it. All of these techniques are used as part of a numbers game.
- Using double negatives.
- Emphasizing the desired outcome by making the button you want the user to press more prominent button.
- Pre-populated checkboxes.
- Hiding the true purpose of programs in exceedingly long EULA agreements.
All of these techniques are widely used on the web. Once the installation procedure was completed, I still had to go and fix a change to the default search engine on all of his browsers. I guess I had missed something somewhere during the installation process…
While these techniques are obvious to most, my friend was both completely floored and righteously incensed when I explained that these practices are indeed intentional.
These bundles, wrappers, download accelerators, secure downloaders, what ever marketing buzz word is chosen to call them rely on something known as “dark patterns”.
Dark Patterns
Dark patterns are UI (User Interfaces) that have been carefully researched and designed to trick the user.
Let’s look at a few…
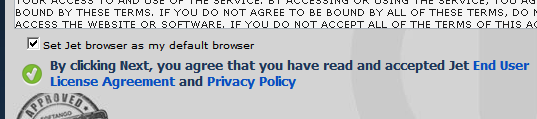
It can be as simple as pre-populating a check box and adding a “seal” as an additional credibility indicator. That seal isn’t official in any way, but split tests probably showed better conversions with it present. The minuscule size of the check mark was certainly split test against as well.
Another common technique involves favoring an outcome by emphasising the desired UI element. Note the muted tones of the skip button, and the seal makes a second appearance.
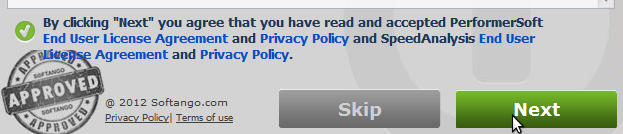
It is a shame that some major players are also involved in these shenanigans.
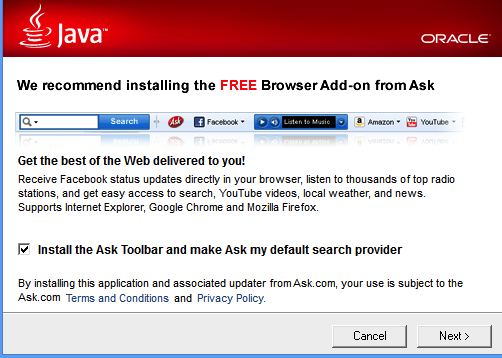
You can read all about these shady techniques at http://darkpatterns.org/ a website curated by Harry Brignull and other like minded user experience professionnals, who are documenting these techniques in an effort to stamp them out. They have posted a YouTube video presentation that goes in great detail explaining the inner mechanics of Dark Patterns, and explains how these tactics actually come about.
While these practices might seem obvious to most, many new or inexperienced users fall victim to these ploys.
I realize that there is a need to monetize, but this should never be achieved at the expense of all morals and ethics. You have to ask yourself, do you trust a company to have your best interests at heart, when they have a team of UI designers perform endless split tests to ensure that the interface you use is optimally designed to trick you into doing something you wouldn’t do of your own volition?
@jean_taggart










