Recently a Malwarebytes researcher informed me of a Multiplug PUP that installs a fake Evernote browser extension. Fellow researchers can find the link to this sample on VirusTotal here.
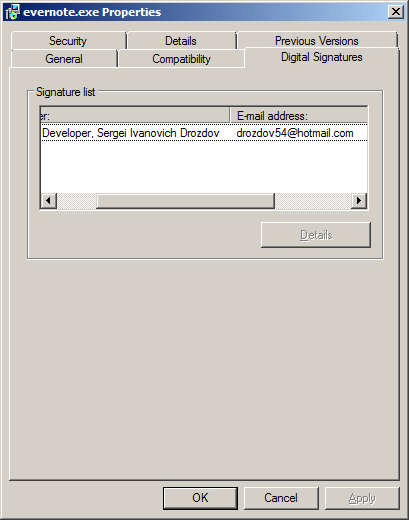
A quick look shows the PUP is digitally signed by “Open Source Developer, Sergei Ivanovich Drozdov”, although the certificate has since been revoked by the issuer. This serves as another reminder that you can’t always trust a program just because it’s digitally signed.
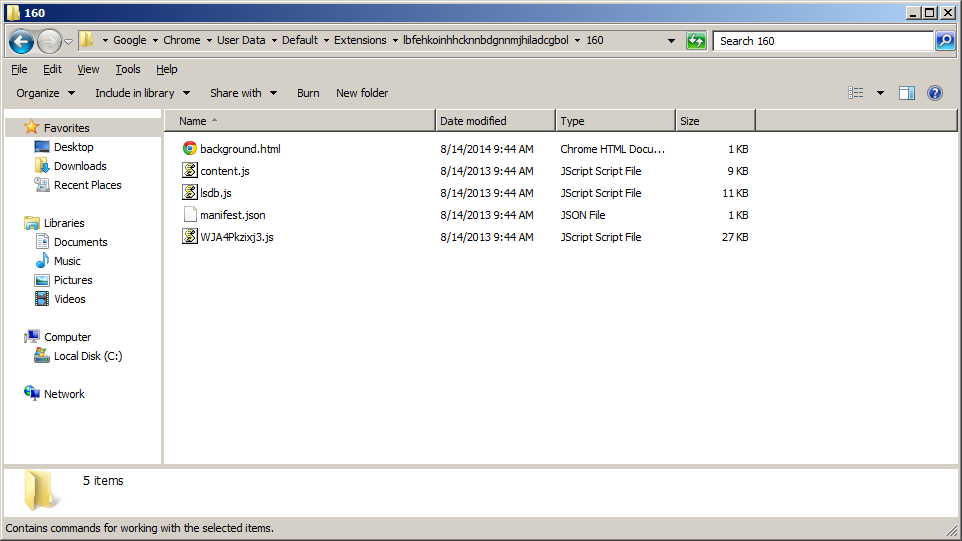
When you execute the PUP, it silently installs a web extension for the Google Chrome, Torch, and Comodo Dragon browsers. The extension takes the form of three obfuscated JavaScript files and one HTML file. The picture shows these files installed in Chrome’s extension directory on a Windows 7 PC.
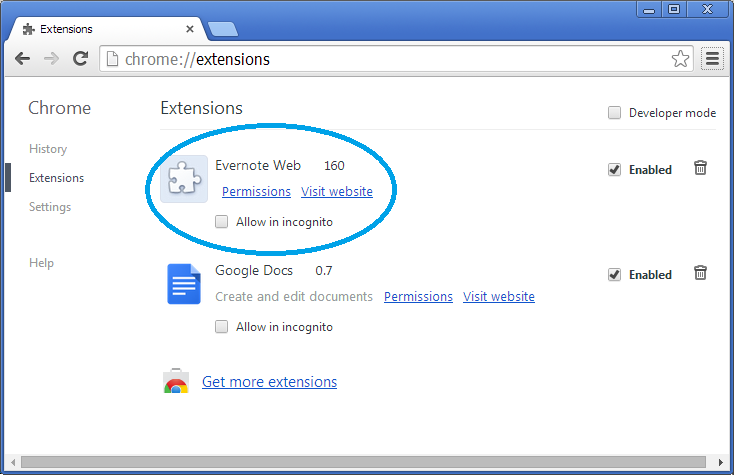
For Google Chrome, the installation of the web extension is achieved by updating the “Preferences” file, which is a json-formatted file used to configure Chrome user preferences. The extension that’s installed is called “Evernote Web,” just like the real extension from Evernote.com.
When taking a look at the Chrome extensions page, we can see the extension installed there with the ID “lbfehkoinhhcknnbdgnnmjhiladcgbol,” just like the real Evernote Web extension.
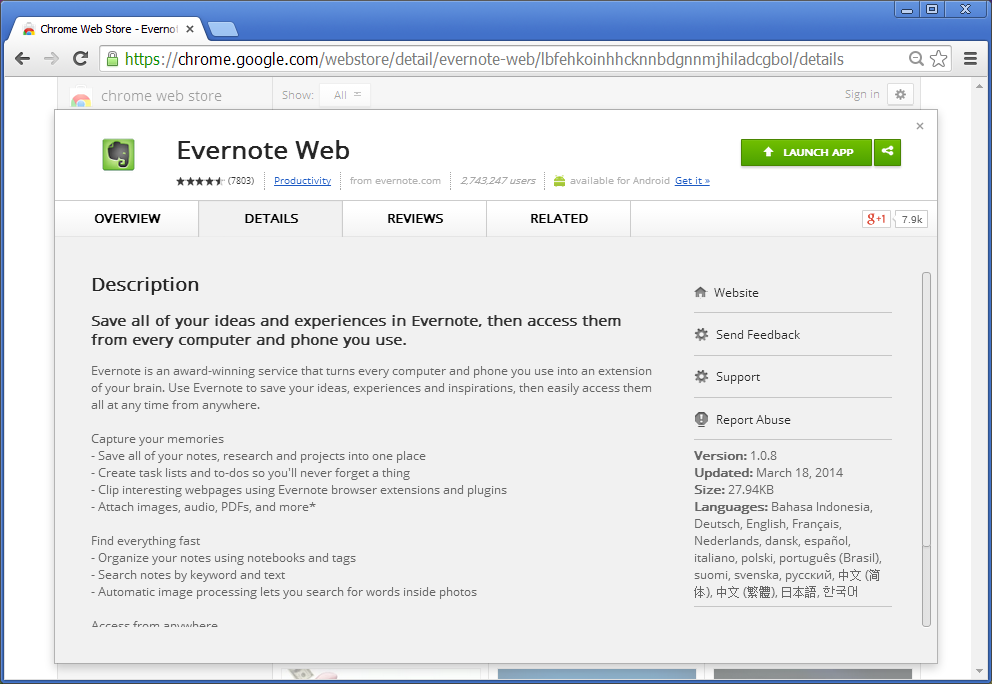
Clicking “Visit website” directs the user to the chrome webstore page for the actual Evernote Web extension. Chrome believes the real extension is installed, as verified by the Launch App button. When clicking this button with the fake extension installed, nothing happens, whereas normally the user is met with an Evernote log in screen.
The extension uses a content script to run in the context of the web pages a user browses. The content script is guaranteed to be loaded into every web page using the extension manifest (manifest.json). When visiting webpages, you’ll get a series of annoying advertisements, all leading to potentially more unwanted programs and offers.
Here is a comparison of visiting newegg.com with and without the fake Evernote extension.
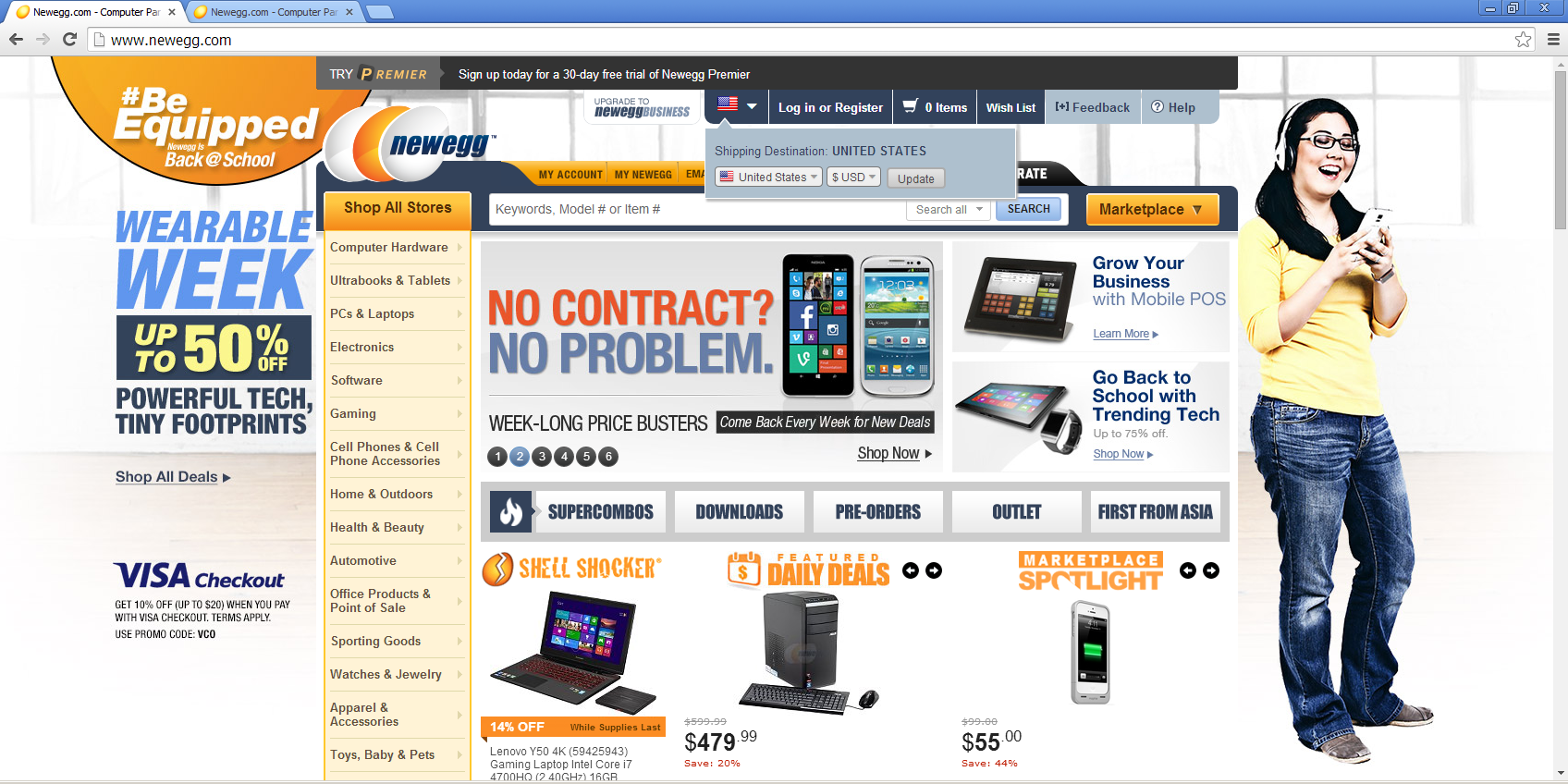
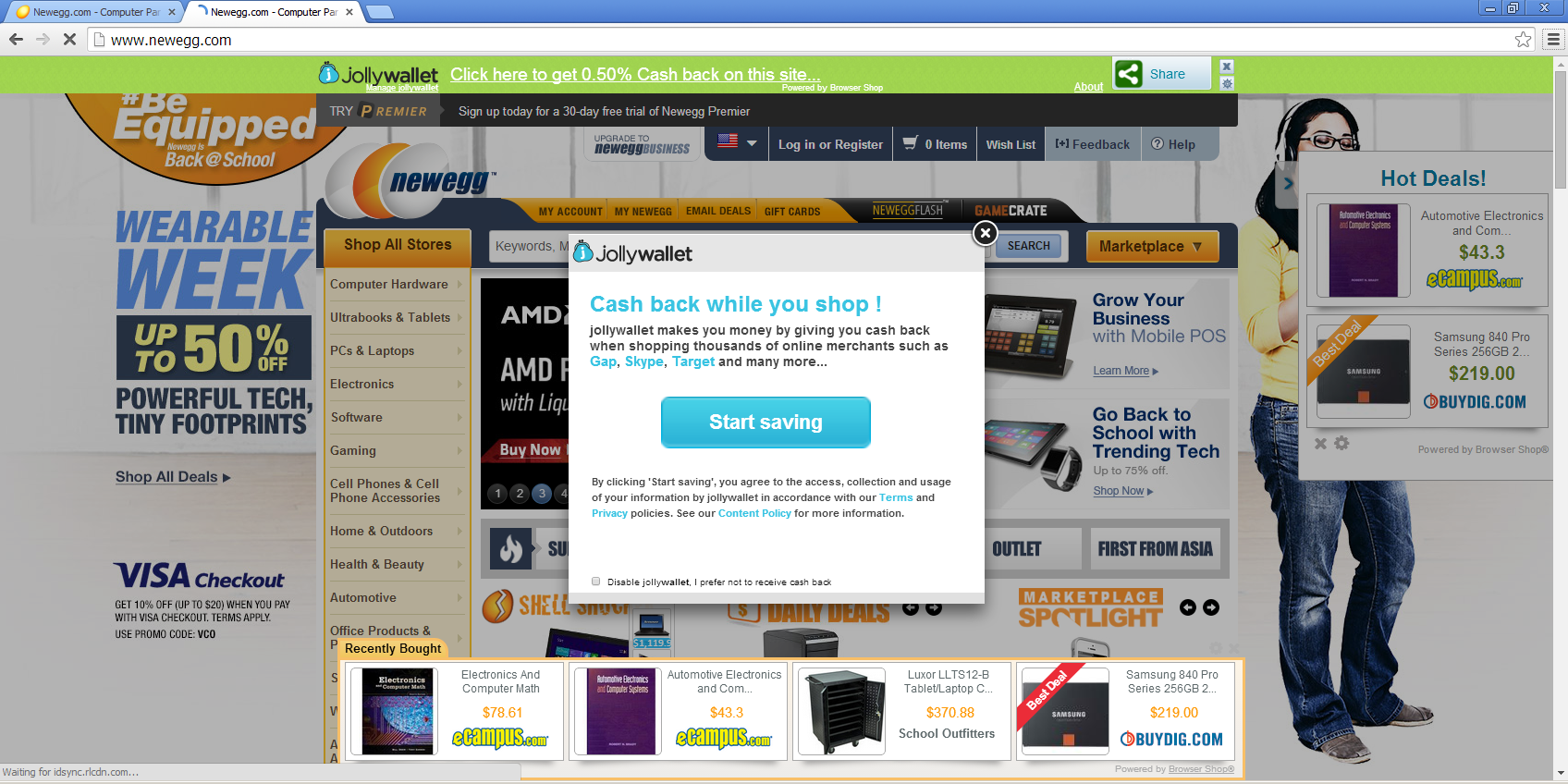
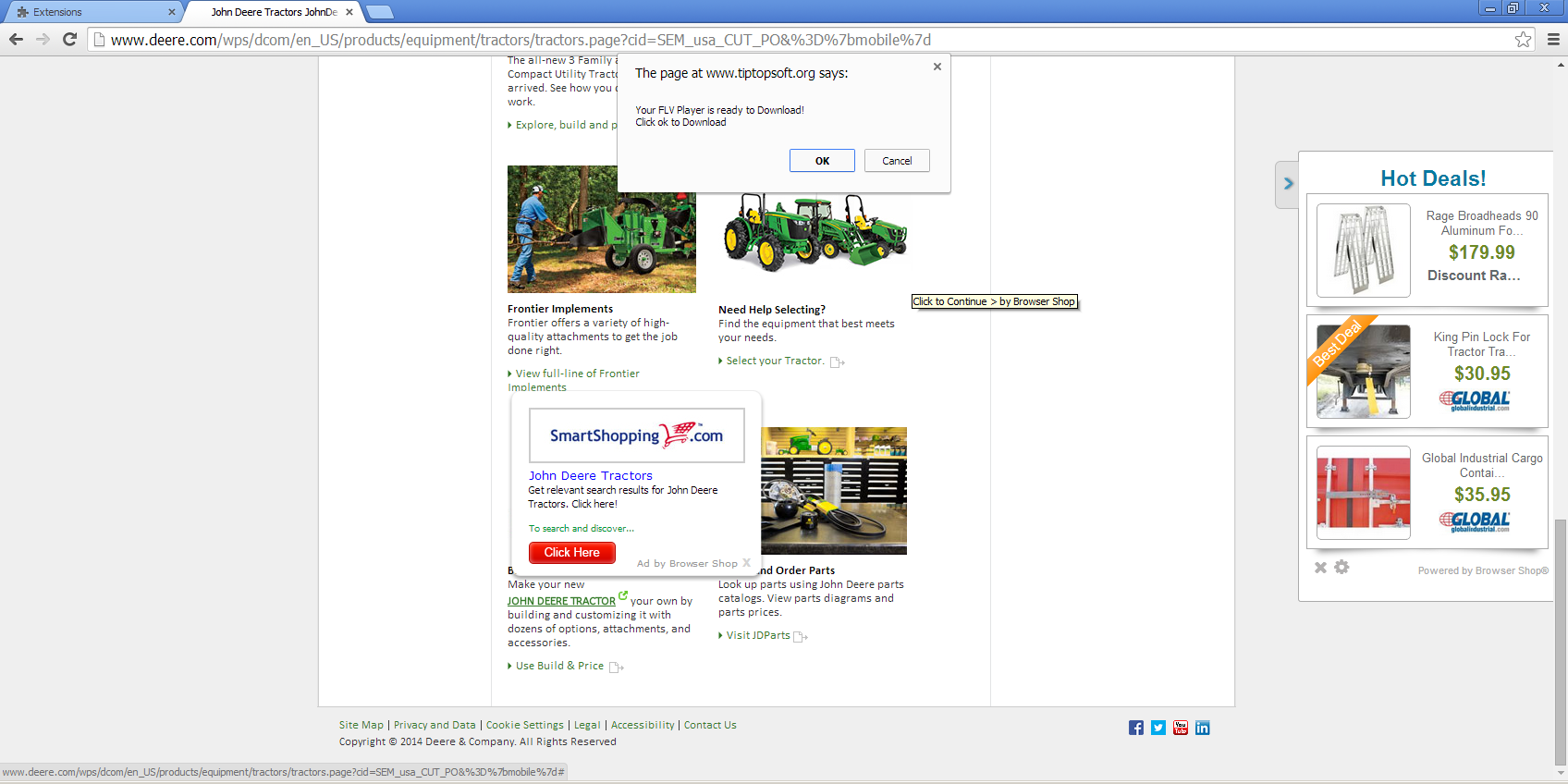
On the surface, it may seem like the pop ups and advertisements are coming from the websites themselves, but are in fact from the fake Evernote web extension.
Fortunately, removing the extension is a simple task. For Chrome users, simply visit the extensions page and click the picture of a garbage can, and you’re done. You also might want to run a free scan using your Antivirus or Anti-malware programs (like Malwarebytes Anti-Malware) to make sure there wasn’t anything else added while you had the extension.










