The HackingTeam data leak was a treasure trove for threat actors. As we documented on this blog, it didn’t take long for fresh zero-days to emerge and be used in mainstream exploit kits within a day.
The HackingTeam archive provided very easy to reuse zero-days that even contained instructions. Exploit kit authors still repackaged the exploits to their liking from the original copies, simply reusing the same vulnerability.
Not all threat actors did that though. We found a particular attack on a Chinese website where the perpetrators literally copied and pasted the exploit code from HackingTeam, and simply replaced the default ‘calc.exe’ payload with theirs.
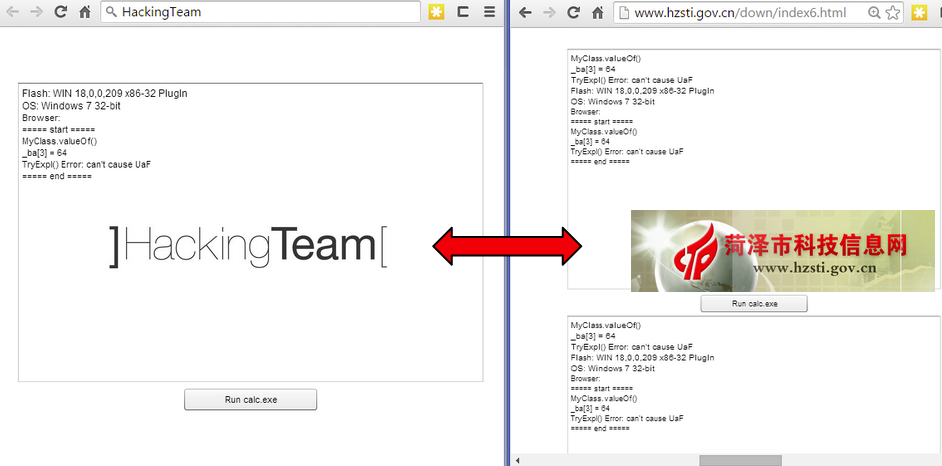
Not only is the ‘landing’ template exactly the same (they even left the Run calc.exe button!), the Flash exploits are also identical.
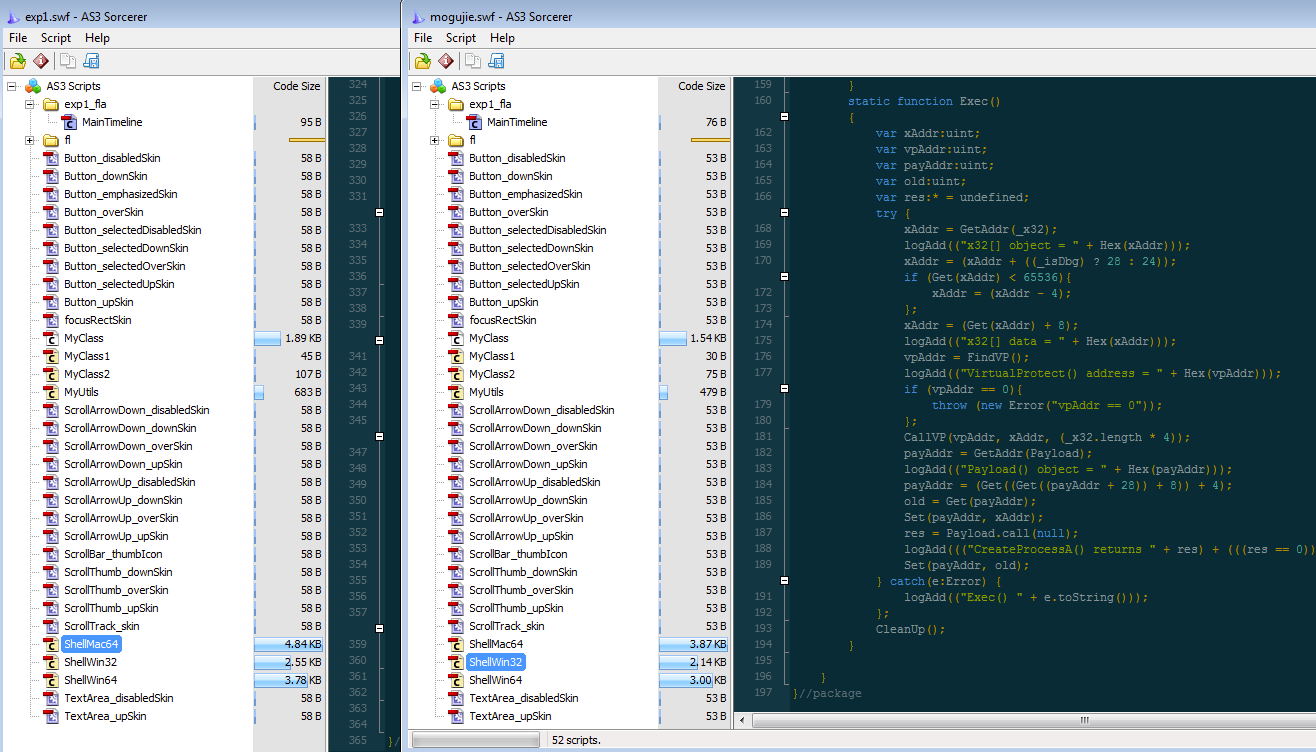
The only thing that really differs is the payload, which instead of being the calculator consist of malicious binaries.
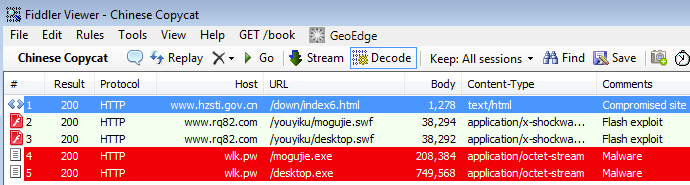
Files used:
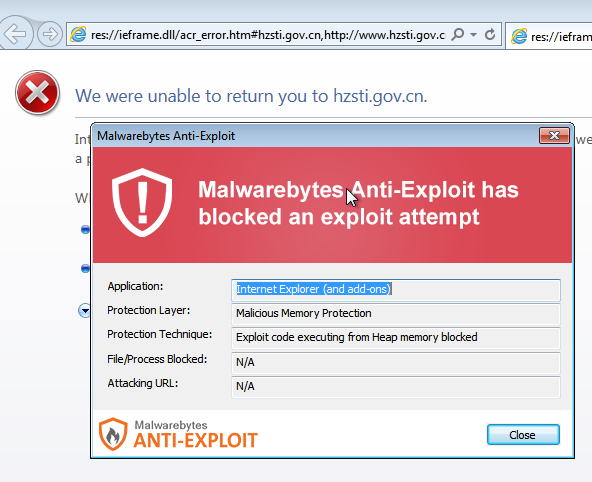
Malwarebytes Anti-Exploit protects you from this threat:
[Update 08/11]
One of the binaries has a hardcoded IP which links to this open directory:
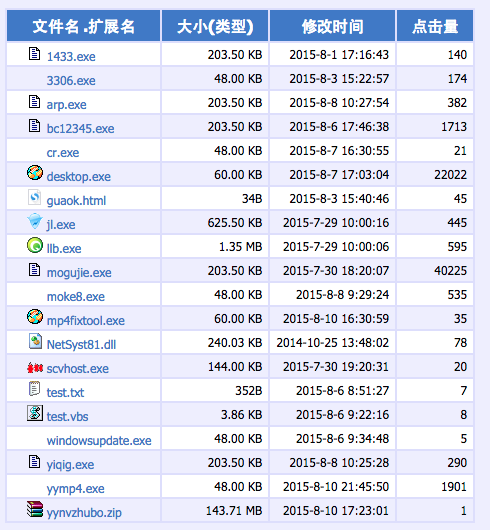
The last column indicates the number of hits or loads. One of the malware files was downloaded over 40K times.
[/Update]










