June and July have set new records for malvertising attacks. We have just uncovered a large scale attack abusing Yahoo!’s own ad network.
As soon as we detected the malicious activity, we notified Yahoo! and we are pleased to report that they took immediate action to stop the issue. The campaign is no longer active at the time of publishing this blog.
This latest campaign started on July 28th, as seen from our own telemetry. According to data from SimilarWeb, Yahoo!’s website has an estimated 6.9 Billion visits per month making this one of the largest malvertising attacks we have seen recently.
- www.yahoo.com | 6.9B monthly visits
- news.yahoo.com | 308.50M monthly visits
- finance.yahoo.com | 135M monthly visits
- sports.yahoo.com | 112.50M monthly visits
- celebrity.yahoo.com | 66.60M monthly visits
- games.yahoo.com | 43.40M monthly visits
ads.yahoo.com -> adslides.rotator.hadj1.adjuggler.net -> ch2-34-ia.azurewebsites.net/?ekrug=sewr487giviv93=12dvr4g4 -> basestyle.org/?id=1423150231&JHRufu346&camp=URhfn67458&click=UEjd856 -> siege.nohzuespoluprace.net/forums/viewforum.php?f=2sb49&sid=y1yki0
As with the previous reported cases this one also leverages Microsoft Azure websites:
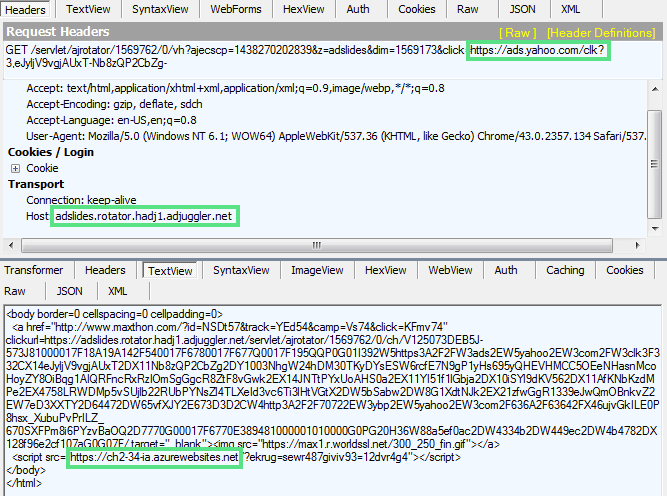
We have observed two main domains being used:
- trv0-67sc.azurewebsites.net/?=trv0-s4-67sc
- ch2-34-ia.azurewebsites.net/?ekrug=sewr487giviv93=12dvr4g4
The sequence of redirections eventually leads to the Angler Exploit Kit:
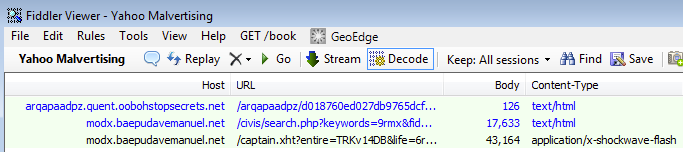
We did not collect the payload in this particular campaign although we know that Angler has been dropping a mix of ad fraud (Bedep) and ransomware (CryptoWall).
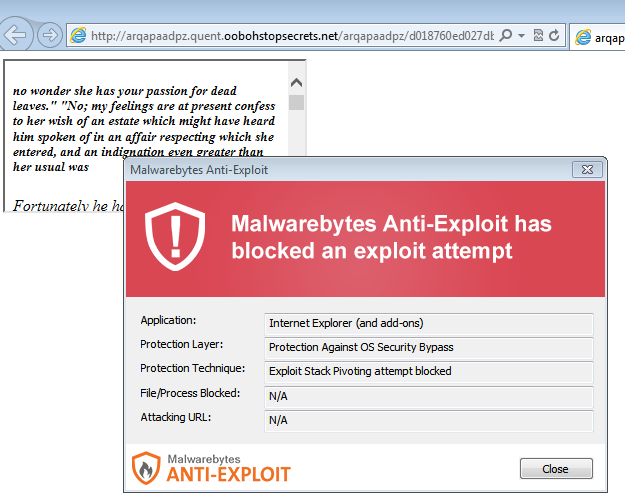
Malwarebytes Anti-Exploit users were already protected against this attack.
We would like to thank Yahoo! for their prompt response with this incident. Here’s their official statement:
“Yahoo is committed to ensuring that both our advertisers and users have a safe and reliable experience. As soon as we learned of this issue, our team took action and will continue to investigate this issue.Unfortunately, disruptive ad behavior affects the entire tech industry. Yahoo has a long history of engagement on this issue and is committed to working with our peers to create a secure advertising experience. We’ll continue to ensure the quality and safety of our ads through our automated testing and through the SafeFrame working group, which seeks to protect consumers and publishers from the potential security risks inherent in the online ad ecosystem.”
Malvertising is a silent killer because malicious ads do not require any type of user interaction in order to execute their payload. The mere fact of browsing to a website that has adverts (and most sites, if not all, do) is enough to start the infection chain.
The complexity of the online advertising economy makes it easy for malicious actors to abuse the system and get away with it. It is one of the reasons why we need to work very closely with different industry partners to detect suspicious patterns and react very quickly to halt rogue campaigns.










