A few days ago we spotted an interesting malvertising attack that was unlike others we had seen before. What made it unique was the multi-stage delivery of a Flash exploit via a seemingly benign XML file.
The advert itself is Flash-based and promotes a game called “Sparta – War of Empires”. However, there were several red flags with this ad that most ad networks would (or should) immediately notice.
For instance, when loading the Flash animation, ActionScript code called out an external URL.
Adverts should not perform this sort of action without any user interaction (i.e. a click) and the structure of the URL was a little suspicious (sub domain and .XYZ TLD seen a lot lately associated with malicious activity).
The following diagram summarizes what takes place from the malvertising to the exploit and finally the infection.
There is a very interesting use of XML documents to store a base64 encoded blurb which needs to be XORed twice to give out the actual malicious SWF used to exploit users with CVE-2015-5122.
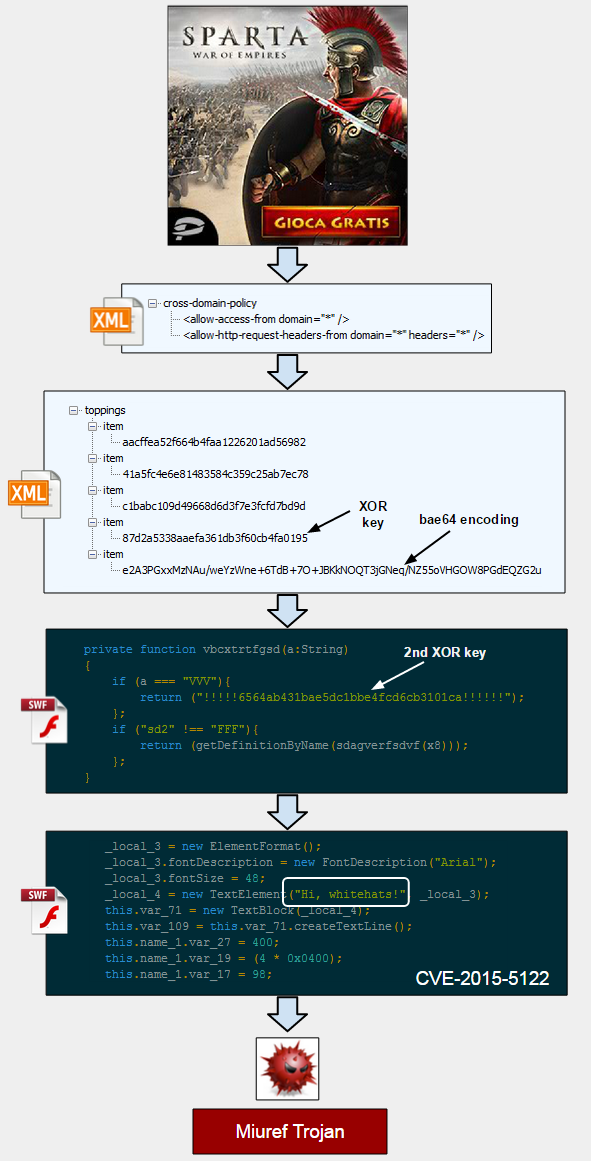
Hiding the SWF exploit within a carefully constructed array inside of an XML document is an interesting technique that allows to load the exploit code directly into memory in a multi-stage attack.
The final payload was the Miuref Trojan, well known for its click fraud and backdoor capabilities. However, Malwarebytes Anti-Exploit users were protected even before the malware binary had a chance to be dropped.
We noticed that Dell SonicWall also wrote about this threat which they called the Spartan Exploit Kit. Given its delivery method, we believe this is more of a “self sufficient” malvertising attack making use of a Flash exploit as opposed to a full fledged ‘Exploit Kit’.
Special thanks to Jerome Dangu, CTO at ClarityAd for the help with this analysis.










